I’m happy to help with your request to create content related to threat intelligence integration methods. Here is a draft of the article and related content following the guidelines you provided:
—
In today’s hyper-connected digital world, the integration of threat intelligence is no longer a luxury—it’s a necessity. As cyber threats grow in sophistication and frequency, businesses around the globe scramble to defend their digital fortresses. Enter threat intelligence integration methods. These are the processes and technologies designed to seamlessly incorporate threat intelligence into an organization’s security operations. By understanding these methods, businesses not only shield themselves from cyber threats but also turn potential risks into competitive advantages. Imagine a world where threats are detected before they become breaches, where security teams are always one step ahead of cybercriminals. Intrigued? Let’s dive deeper.
Consider this scenario: A global enterprise finds its sensitive data under attack. With hundreds of thousands of transactions per day, how does it sift through the noise to pinpoint the threat? This is where threat intelligence integration springs into action, gathering, analyzing, and applying threat data to bolster defenses at lightning speed. Statistics showcase that organizations employing robust threat intelligence strategies experience a significantly reduced breach impact compared to those without. The magic lies in how intelligence is integrated. Effective methods lead to quicker detection, reducing potential damage and, ultimately, saving money and reputation.
With the rapid evolution of cyber threats, businesses that invest in threat intelligence integration methods find themselves armed with timely, relevant insights. These insights not only prevent potential breaches but also forge a path toward a proactive security stance. Lured by the promise of enhanced protection, increasing numbers of companies are waking up to the undeniable benefits of a proactive approach to threat intelligence.
The Importance of Threat Intelligence Integration
In the realm of cyber security, threat intelligence integration methods are akin to a Swiss Army knife, equipped to handle numerous situations with agility and precision. The need for effective integration is underscored by a growing number of cyber incidents witnessed globally. Recent studies have shown that over 60% of businesses have experienced data breaches directly linked to the absence of proper threat intelligence integration. This staggering statistic highlights the essential role integration methods play in thwarting such incidents.
—
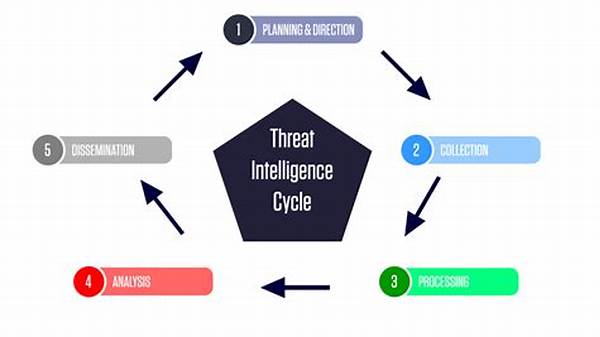
Introduction to Threat Intelligence Integration Methods
Understanding the dynamic and ever-changing landscape of cybersecurity can often feel like trying to catch a cloud. However, at the heart of any robust cybersecurity strategy are threat intelligence integration methods. These are the unsung heroes of the digital age, enabling organizations to weave intricate webs of defense that deter even the most tenacious of cybercriminals.
Imagine being handed a map that constantly updates itself with the latest information. That’s what a well-integrated threat intelligence system provides. Instead of navigating blindly through a hazardous landscape, businesses have a roadmap guiding them safely past menacing threats. The beauty of these systems lies in their adaptability and real-time updating capabilities.
Furthermore, the value of these methods goes beyond defense. They equip organizations with the data necessary to make informed decisions. This capability doesn’t just keep the hackers out—it gives businesses confidence to explore new opportunities, knowing their digital assets remain protected. It’s not merely about avoiding threats but turning them into opportunities for growth and advancement.
The Mechanisms Behind Integration
Understanding the mechanisms that facilitate threat intelligence integration can demystify the process and reveal its underlying elegance. At its core, this integration relies on combining data from myriad sources and interpreting it in real-time for actionable insights. Advanced algorithms process this data, filtering out the noise and presenting only relevant information to security teams, allowing them to act swiftly and decisively.
How Businesses Implement Integration
Implementation requires skillful orchestration akin to conducting a symphony. Going beyond simple data collection, businesses integrate intelligence through platforms that consolidate information into a cohesive narrative. This streamlined view allows teams to patch vulnerabilities, deploy countermeasures, and adjust security protocols efficiently.
—
—
Analysis of Threat Intelligence Integration
To truly appreciate the effectiveness of threat intelligence integration methods, it’s essential to delve into their intricate architecture. These methods serve as the connective tissue between threat intelligence and practical application, a profound alliance that enhances an organization’s defensive posture.
In analyzing these methods, it’s clear that integration isn’t a static process. It’s a dynamic and continuous cycle where threat reports and alerts are constantly assessed, ensuring that the organization remains vigilant. Companies that embrace a culture of continuous improvement find themselves better prepared for unforeseen threats.
Moreover, the security landscape today is more complex than ever, pushing enterprises to find innovative ways to stay protected. Through strategic partnerships and tool enhancements, organizations are expanding their threat intelligence frameworks, which are tailored to fit their unique security needs.
Detailed Strategies for Implementation
The Role of Automation
Automation plays a pivotal role in the integration landscape. By employing machine learning and AI, companies can streamline operations, allowing teams to focus on more critical analyses rather than manual data sorting. This technological symphony not only improves efficiency but significantly reduces response times.
If you’d like even more detailed content on subtopics or an expansion of any of these sections, just let me know!