Step-by-Step Firewall Setup Tutorial
Securing your network is imperative in today’s digital age. With cyber threats increasing every day, the significance of firewalls cannot be overstated. A firewall serves as your first line of defense, filtering out potential dangers before they infiltrate your system. This step-by-step firewall setup tutorial is designed not only to guide newcomers through the maze of firewall configurations but also to empower them to safeguard their digital assets effectively. Whether you’re a small business owner or just someone who values online privacy, setting up a firewall doesn’t have to be a daunting task. This guide promises to be your trusty companion, offering clear, concise steps to achieve your security goals.
First, it’s essential to understand what a firewall does. Imagine your home: locking the doors at night keeps burglars out. Similarly, a firewall blocks unwanted traffic while allowing legitimate communications to flow seamlessly. The beauty of technology, however, is that it can do much more than a lock and key. With this step-by-step firewall setup tutorial, you will not only learn how to install a firewall but also how to fine-tune it to best serve your needs.
Decision paralysis is a real issue when faced with myriad security tools and jargon. This tutorial cuts through the noise, making the setup process approachable for everyone. Remember, every minute spent on improving your network’s security is a well-invested effort for your peace of mind.
The digital landscape is rife with pitfalls, but equipping yourself with the right knowledge diminishes risks significantly. As we venture into this step-by-step firewall setup tutorial, be prepared to shield your network with newfound vigor. Knowledge is power, and by the end of this guide, you’ll wield it confidently against cyber threats.
The Basics of Firewall Configuration
Description
In today’s fast-paced digital world, where information is gold and security breaches are more common than ever, knowing how to protect your digital assets is crucial. A firewall, as a barrier between your network and possible cyber threats, acts as a gatekeeper—monitoring, filtering, and blocking malicious traffic. But how do you ensure it’s set up correctly? That’s precisely where our comprehensive guide, the step-by-step firewall setup tutorial, comes in.
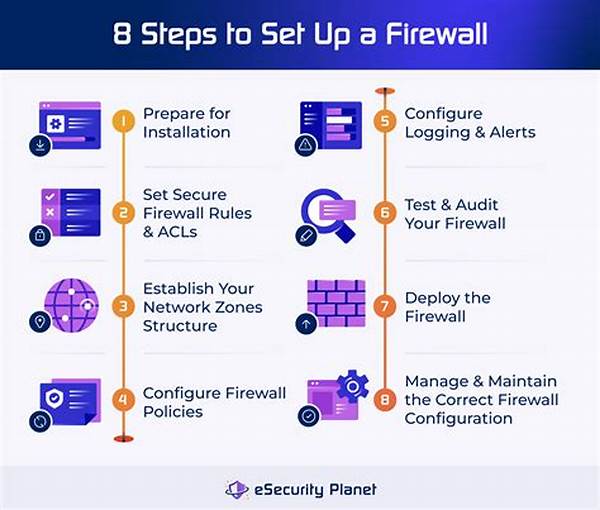
To start, it’s important to recognize the different types of firewalls available. From software and hardware firewalls to proxy and packet-filtering firewalls—each has its strength. Knowing which one suits your needs can set the tone for effective network protection. Our step-by-step firewall setup tutorial will guide you through these options, helping you select the perfect match for your security requirements.
Furthermore, understanding your network’s architecture is essential when setting up a firewall. Every network is different with unique traffic patterns and vulnerabilities. This tutorial will assist you in mapping out your network structure, identifying key areas that need protection, and configuring your firewall to cater to these needs.
Types of Firewalls
Next, implementation is key. It’s one thing to know what needs to be done, but effectively executing your plan is another challenge. With detailed illustrations and examples, this tutorial will walk you through firewall installation, ensuring that no detail is overlooked. From setting up rules to testing configurations, our guide leaves no stone unturned.
Moreover, maintaining a firewall is just as important as setting it up. Regular updates and monitoring are vital to keep up with the evolving cyber threats. The tutorial provides tips on how to keep your firewall robust and resilient, turning you into not just a user, but a proficient network guardian.
Finally, learning from others’ experiences can accelerate your understanding and effectiveness. Real-life case studies, along with testimonials from users who have successfully bolstered their network security, are included to provide insights and inspiration. By the time you finish this step-by-step firewall setup tutorial, not only will you have fortified your network, but you’ll also possess a deeper understanding of network security.
Discussion Topics
Adopting a firewall is no longer optional in the modern digital landscape, with threats looming at every corner of the web. Engaging in discussions about the nuances of firewall setup and the importance of customized security can significantly elevate your ability to protect your valuable data. Participating in forums, networking with IT professionals, and enrolling in security workshops can provide real-world insights and practical know-how.
In professional settings, knowing how to implement and manage a firewall services clients well—particularly for IT consultants and system administrators. These skills not only boost your employability but also empower you to offer more comprehensive and effective solutions to your clients. It’s a valuable asset that reflects your commitment to excellence and security.
Collaboration and constant learning remain central to mastering cybersecurity, and engaging with community discussions about this step-by-step firewall setup tutorial is a step in the right direction. Share your experiences, learn from others, and continually enhance your security posture.
Firewall Setup Discussion
The Dynamics of Network Protection
Related Topics
Key Considerations in Firewall Setup
The cybersecurity landscape is continuously evolving, with new threats appearing daily. Hence, it’s essential to be proactive rather than reactive regarding network security. As cyber threats become more sophisticated, so too should your defense mechanisms. This step-by-step firewall setup tutorial arms you with the critical knowledge to set up robust security defenses, capitalizing on clear instructions and expert advice.
Imagine being able to sleep peacefully at night, knowing your network is secured against malicious attacks. That’s not just a dream but a reality waiting at the end of this tutorial. Embark on this journey of securing your network today, take control of your digital safety, and stand firm against the ever-growing tide of cyber threats.