Step-by-Step Firewall Setup
In the digital age, ensuring the security of your online assets is more crucial than ever. As our dependency on technology deepens, so does the precision and sophistication of cyber threats. Enter the world of firewalls—a digital defense mechanism standing guard between trusted internal networks and untrusted external networks, such as the internet. It’s akin to a vigilant sentry preventing unauthorized access while allowing legitimate communication to flow freely. Understanding the setup of a firewall can sometimes seem daunting, but worry not; this guide simplifies the steps so that even those new to IT security can grasp the essentials.
Firewalls play a pivotal role in safeguarding your network’s integrity. Imagine them as the sturdy walls and locked doors of a fortified castle. Without them, any malicious entity could waltz in uninvited, causing untold damage. Our goal is to empower you with the knowledge of a step-by-step firewall setup, enhancing your digital armory against potential threats. While the concept might seem overly technical, breaking it down into a comprehensive guide will ease the process. You’ll soon find yourself confident in implementing security measures that fit your unique needs, whether you’re an individual user or managing a corporate network.
Why You Need a Firewall
Setting up a firewall is not merely a recommendation; it’s a necessity. With cyber threats lurking around every corner of the internet, having a robust defense is non-negotiable. Imagine walking into your home to find strangers rummaging through your personal space. Unnerving, right? This is precisely what can happen when your network is left unprotected. With a proper step-by-step firewall setup, you create a barrier that filters out the unwanted, ensuring only safe and verified accesses are permitted. Modern-day cyber threats can sometimes bypass standard security practices, making a firewall a vital component in any security toolkit.
—
The Importance of a Methodical Firewall Setup
When stepping into the world of cybersecurity, one of the primary pillars of a secure network is a properly configured firewall. Picture the firewall not just as a security measure, but the very blueprint of your network’s safety architecture.
Understanding Firewall Mechanisms
It’s fascinating how firewalls operate, acting as the front line of defense in your IT infrastructure. By meticulously following a step-by-step firewall setup, you ensure that your home or business environment is defended from unauthorized access while allowing legitimate traffic. This process involves configuring firewall policies, setting up proper filtering rules, and regularly updating security protocols. These measures can be compared to customizing the locks on your digital doors to ensure maximum security tailored to your lifestyle or business operations.
In a series of comprehensive steps, this guide examines the essential elements and techniques required for implementing an effective firewall strategy, ensuring data privacy and safeguarding against potential threats. Utilizing analytics and statistical data from recent cyber threat studies reinforces the importance of a robust setup. So, as they say, buckle up, because the journey towards a fortified digital presence begins here.
Ensuring Optimal Performance
Like a well-oiled machine, your firewall should operate seamlessly without disrupting daily activities. This necessitates periodic reviews and updates of your security measures to keep up with evolving threats. Imagine owning a car; regular maintenance is imperative to ensure safety and performance. Similarly, maintaining your firewall ensures your network remains impregnable, adapting to new challenges and threats.
Of course, true to its purpose, a firewall isn’t just a one-time setup. It’s an evolving strategy that demands attention and periodic updates. Just as you wouldn’t let a garden grow wild and unkempt, neither should you ignore the signs of wear or potential vulnerabilities in your firewall system.
—
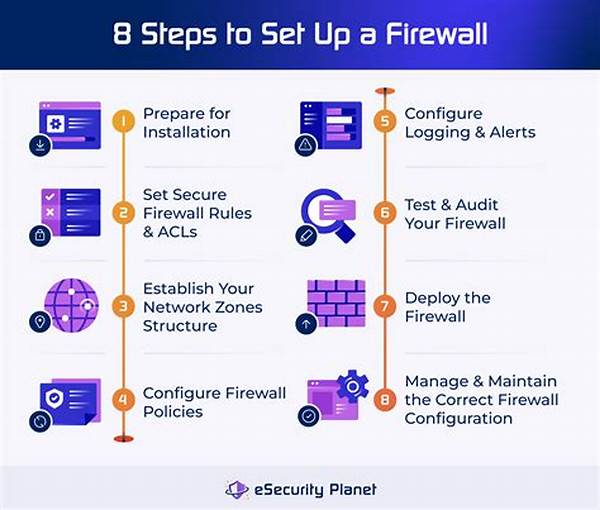
Examples of a Step-by-Step Firewall Setup
Before implementing a firewall, ensure you have a clear understanding of your network’s overall structure.
Choose a firewall that fits your specific needs, depending on whether it’s for personal use or enterprise-level protection.
Correctly configure the network interfaces to clearly distinguish different network zones.
Set up rules that dictate which types of traffic are allowed or denied.
Establish strict access control measures to restrict and monitor access to your network.
Monitor firewall logs regularly for any suspicious activity that could indicate security breaches.
Ensure your firewall’s firmware is up-to-date to protect against new vulnerabilities.
Regularly test your firewall setup to ensure it is functioning as intended and effectively blocking threats.
Keep abreast of new firewall technologies and strategies to enhance your setup over time.
Enhancing Your Digital Fort Knox
Each step plays a pivotal role in erecting a digital fortress unparalleled in its security robustness. A step-by-step firewall setup equips you with the digital armor necessary to withstand persistent threats while simultaneously offering peace of mind in a digital-first era. By embracing this setup, you won’t just be in control; you’ll be empowered.
—
Investigation into Step-by-Step Firewall Setup
Setting up a firewall involves more than just enabling device settings; it demands a comprehensive strategy aligned with your security goals. One can compare this setup process to cooking a deliciously intricate dish—each ingredient, or in this case, each step, is crucial for the final product to turn out as desired. In recent studies, organizations reported a significant reduction in cyber threats post a step-by-step firewall setup, emphasizing its importance in the digital landscape.
How to Leverage Firewall Technology
Leveraging firewall technology effectively requires understanding the varied types available. Firewalls can take many forms: packet-filtering, proxy, stateful inspection, or next-gen. Choose one that aligns with your specific use-case scenario. Creating simple yet effective policies ensures consistent network protection without unnecessary complexity. Streamlined configurations can sometimes outperform intricate ones, providing efficiency without compromising security.
Building a Human Firewall
Despite having high-tech solutions, never underestimate the power of human awareness in cybersecurity. Educating individuals on the basics of network security can turn employees or family members into allies who complement the digital measures you have in place. This ‘human firewall’ works alongside your technology, providing an additional layer of protection.
Ultimately, setting up and managing a firewall is a dynamic task requiring vigilance and adaptability. The threats landscap change rapidly, and so must your fortress. Embrace the process, and you’ll ensure your network is as solid as rock.
Achieving proficiency in these setups not only impacts immediate security but builds the foundation for consistent safety practices, keeping intruders at bay. The true power is, therefore, in both the simplicity and comprehensiveness of a solid step-by-step firewall setup.
—
Key Elements of a Firewall Strategy
Knowledge of potential vulnerabilities and threats keeps you proactive.
Tailor the firewall settings to the specific organizational or personal needs.
Frequent updates ensure your firewall adapts to evolving cyber threats.
Implementing clear rules about who can access what on the network.
Use analytics to interpret evolving patterns and threats.
Educating users about risks and encouraging secure practices.
Preparing a response plan for dealing with breaches.
A step-by-step firewall setup is indispensable, not merely serving as a first step towards more extensive measures but as an integral component of digital defense. Embrace this educational journey to fortify your cyber realm, ensuring safety, security, and peace of mind in the digital age.