- Why Security Incident Investigation Processes Matter
- Steps in Security Incident Investigation Processes
- Tools and Technology in Security Incident Investigation Processes
- Importance of Documentation in Security Incident Investigation Processes
- Real-World Examples of Security Incident Investigation Processes
- Final Thoughts on Security Incident Investigation Processes
Hey there, fellow bloggers and tech enthusiasts! Today, we’re diving into a topic that’s as crucial as your morning coffee—security incident investigation processes. Whether you’re a cybersecurity pro or just someone who’s curious about what happens behind the digital curtains when things go awry, you’re in the right place. Let’s unpack this intriguing topic with a casual, conversational vibe. Grab your favorite beverage, and let’s get started!
Why Security Incident Investigation Processes Matter
In our interconnected world, security incidents can be as varied as my snack choices during a Netflix binge—limitless and sometimes unexpected. So, why should we care about security incident investigation processes? Well, these processes are like the unsung heroes of the digital realm. They meticulously piece together the who, what, when, where, and how, giving us the answers we desperately need post-incident.
Imagine a detective show but in the cyber world. The cybersecurity team becomes Sherlock Holmes, chasing digital breadcrumbs and turning binary bits into comprehensive narratives. That’s what security incident investigation processes bring to the table. They identify what went wrong, limiting potential damage and ensuring a plan is in place to prevent future mishaps. By understanding and appreciating these processes, we’re better equipped to navigate and protect our digital worlds. So, next time you think about skipping the nitty-gritty, remember: those detailed steps play a pivotal role in safeguarding our precious data treasures.
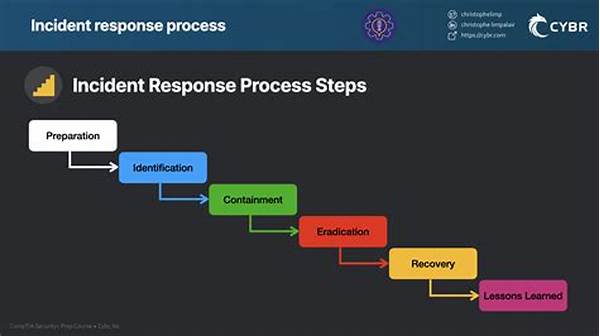
Steps in Security Incident Investigation Processes
1. Identification Stage: The start of every journey! It’s all about spotting anomalies just like spotting that one friend who didn’t get the memo about the dress code.
2. Containment Phase: Imagine tackling the spillage before it floods. This phase is all about damage control in the security incident investigation processes.
3. Eradication Endeavors: Think of this like a massive digital cleanup. You’re eradicating the source, ensuring it doesn’t sneak its way back.
4. Recovery Route: Bringing things back to normal is everyone’s favorite part in security incident investigation processes. It’s about resurrecting data and systems.
5. Lessons Learned: Don’t let the mistakes go to waste! Reflect, adapt, and make those necessary changes for future fortification.
Tools and Technology in Security Incident Investigation Processes
Alright, tech lovers, this one’s for you! Let’s chat about the red cape to our digital superheroes: tools and technology. In the realm of security incident investigation processes, tools like SIEM (Security Information and Event Management) systems, intrusion detection systems, and log analyzers are the unsung wizards. They’re sifting through heaps of data like pros playing Minesweeper, pinpointing potential threats and anomalies.
For those who love gadgets and software, this is where your fascination meets functionality. These technologies enable cybersecurity teams to gain insights, craft detailed reports, and do a virtual magnifying glass analysis of what went down. So next time you come across an SIEM, IDS, or log analysis tool, give it a nod of respect because they’re quietly holding the digital fort. Embrace the geeky goodness here and understand how tools are not just about flashy dashboards but are essential players in effective security incident investigation processes.
Importance of Documentation in Security Incident Investigation Processes
Documentation might just seem like a mundane task, but in the security incident investigation processes world, it’s like keeping a diary of your cyber adventures. Remembering what happened, when it happened, and how it was resolved ensures that you’ve got a roadmap for any repeat scenarios. Plus, it helps in turning chaos into orderly knowledge.
Having detailed documentation makes sure everyone’s singing from the same song sheet. It provides clarity when piecing together the digital jigsaw puzzles that incidents tend to leave behind. Moreover, having this info at hand not only aids present investigations but acts as a touchstone for future learning and preventative measures. So, if documentation seems dull to you, consider it the guiding star in the night sky of the security incident investigation processes.
Real-World Examples of Security Incident Investigation Processes
Ever wondered what a security incident looks like in the wild? Picture this: You’re working late, and suddenly, your screens flicker. Security incident investigation processes kick into high gear like a detective duo leaping into action. Real-world scenarios, like the infamous WannaCry ransomware attack, highlight the importance of these processes.
The initial stage of identifying the attack is like spotting that your gelato is melting. From containment to eradication, recovering systems to implementing lessons learned—each step unveils a new layer of understanding. By dissecting these real-world incidents, we not only learn what to do but, often more importantly, what not to do. In security incident investigation processes, it’s about embracing each blunder as a stepping stone to stronger defenses in the future.
Final Thoughts on Security Incident Investigation Processes
To wrap things up, security incident investigation processes are more than just procedural; they’re essential. They’re the behind-the-scenes magic that makes sure our data isn’t just floating aimlessly in cyberspace. From understanding the steps involved to recognizing the unparalleled importance of tools and documentation, each facet plays its part in this digital symphony.
So here’s the takeaway: it’s not just about reacting to incidents but evolving with them. The world of cybersecurity is ever-changing and demands our constant attention and adaptation. As we learn and grow, these processes remind us that while the digital landscape holds potential threats, it also offers the opportunity for robust safeguards. Embrace the details, respect the processes, and safeguard your digital sanctuary.