I’m happy to help with your request! Given the complexity and length involved in creating multiple types of content related to “secure data transmission via VPNs,” I’ll create a snippet for each requirement to give you an idea of how you can structure them.
Article: Secure Data Transmission via VPNs
H1: Secure Data Transmission via VPNs
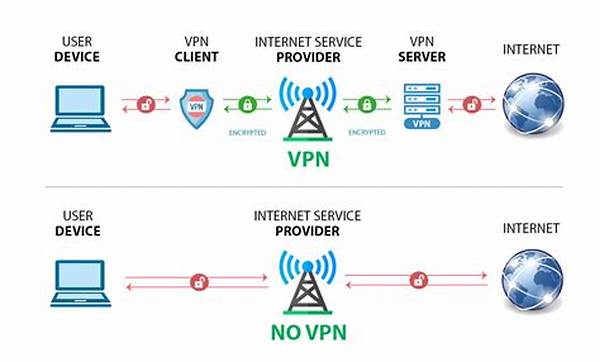
In the digital age where privacy and cybersecurity concerns are at an all-time high, secure data transmission via VPNs (Virtual Private Networks) has become pivotal for individuals and businesses alike. Whether you’re a globe-trotting entrepreneur or a college student accessing public Wi-Fi at your local cafe, the necessity of protecting your data cannot be overstated. The journey to secure data transmission via VPNs begins with understanding the inherent vulnerabilities of the internet and how VPNs offer a robust shield against these threats.
For those yet uninformed, a VPN is like a private tunnel in the vast ocean of the internet, cleverly routing your connection through servers located globally. This not only masks your IP address but also encrypts the data traveling back and forth, ensuring that hackers, government entities, and even your ISP cannot easily monitor your online activities. Secure data transmission via VPNs is designed for seamless connectivity while offering the peace of mind that your sensitive information is secure.
But hold your horses – it isn’t just about creating an invisible cloak for your internet activity. Secure data transmission via VPNs extends beyond privacy; it grants you access to geo-restricted content, making your world wide web ventures effectively boundless. That’s right, while everyone’s talking about the latest Netflix series that’s unavailable in your region, VPN users are already ahead in the game.
Consider this: a VPN isn’t just about hiding and streaming. When businesses implement secure data transmission via VPNs, they’re securing remote work connections, safeguarding intellectual property, and ensuring compliance with industry regulations. It’s a must-have tool that promises business continuity without comprising data integrity. Imagine your business documents silently voyaging across oceans, untouchable by prying eyes, locking yourself into a virtual fortress of solitude.
H2: Understanding How VPNs Enhance Security
—
Description of Secure Data Transmission
H2: Why You Need a VPN?
The modern digital space is saturated with cybersecurity threats; hence, the need for secure data transmission via VPNs becomes ever more pressing. Let’s dive deeper into the importance of using VPNs and the benefits they bring to your digital life.
Imagine accessing your bank accounts, confidential emails, and work documents over a bustling public Wi-Fi—the thought is unsettling, right? This is where the role of secure data transmission via VPNs becomes indispensable. By encrypting your data, VPNs ensure that nothing short of Fort Knox security stands between your private life and the cybercriminals.
H3: The Mechanics Behind VPNs
VPNs operate by creating an encrypted tunnel for data. When you initiate a connection, it’s like entrusting your private letters to a trustworthy courier who is invisible to would-be interceptors. This doesn’t just protect vital personal information but also maintains high-speed connections to avoid those dreaded buffering screens. With VPNs, users achieve the best blend of high bandwidth and unobserved privacy.
Thanks to secure data transmission via VPNs, you are no longer limited by geographical content barriers. Imagine catching up with the latest series, unrestricted by location, or accessing region-locked academic resources for your research without crying a river over digital gates.
The beauty of utilizing a VPN is the simplicity wrapped in advanced tech. VPNs typically boast user-friendly interfaces—configurable with a few clicks, and soon, your online travel gets a security makeover. It’s like putting on your trusty helmet before embarking on a digital adventure, complete with all the hiccups and occasional laughable technical glitches.
—
Discussion Points
H2: Engaging Topics on VPN Security
In today’s connected world, safeguarding our online presence is critical, and secure data transmission via VPNs plays a central role in achieving that security. From business users accessing sensitive information remotely to everyday internet users surfing the web, VPNs offer robust protection against cyber threats. The discussions surrounding secure data transmission via VPNs are varied, reflecting the multifaceted nature of this invaluable technology.
As technology advances, VPNs are evolving, integrating even more sophisticated encryption techniques to counteract emerging threats. The conversations delve into diverse themes like encryption mechanisms, operational nuances, and the future trajectory of VPN technology. In securing your online interactions, VPNs transform the digital landscape, promising a safer, more versatile experience on the information highway.
—
Article Points
H2: Key Functions of Secure Data Transmission via VPNs
—
Short Content on Secure Data Transmission
In an age where digital and cybersecurity go hand in hand, how we approach secure data transmission via VPNs sets the stage for privacy and protection online. Through secure data transmission via VPNs, individuals can enjoy a digital world where freedom and privacy coexist, all without compromising on performance or accessibility.
The critical aspect of secure data transmission via VPNs lies in its encryption capabilities. It’s akin to a digital vault, protecting your data even if interception occurs. Think of VPNs as an exclusive club, giving you privileges like accessing geo-restricted content while keeping uninvited guests out.
Secure data transmission isn’t just a luxury—it’s a necessity. In businesses, the seamless integration of VPNs into the digital workspace has marked a notable improvement in safeguarding information, promoting productivity, and ensuring compliance. Secure data transmission via VPNs is the unsung hero of the corporate world.
H2: VPNs for Personal and Professional Security
H3: Future-Proofing Your Digital Journey
Navigating the digital sphere without the security net of a VPN is like surfing without a life jacket—it’s daring but risky. With secure data transmission via VPNs, not only do you gain security, but you future-proof your digital journey. It’s the smart, rational choice for anyone concerned about privacy today and in the years ahead.