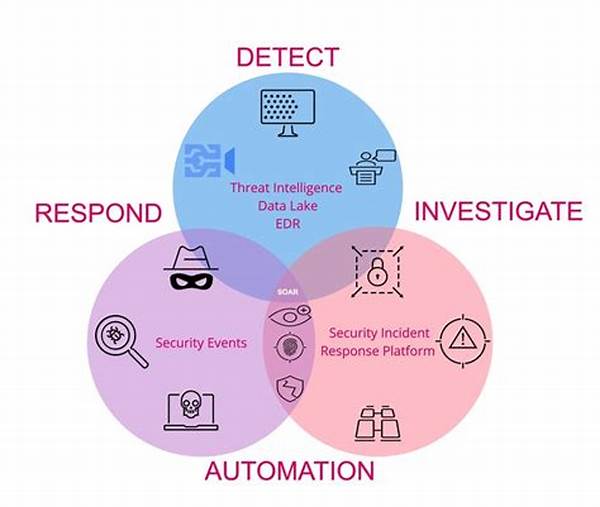
- Why Real-Time Threat Management is Essential
- The Future of Cybersecurity Systems
- Five Key Discussions on Real-Time Threat Management in Cybersecurity Systems
- Introduction to Real-Time Threat Management
- Navigating the Complex World of Real-Time Threat Management
- Insightful Execution and Strategic Planning
- The Human Element in Cyber Defense
- Tips for Implementing Real-Time Threat Management in Cybersecurity Systems
In today’s fast-paced digital landscape, real-time threat management in cybersecurity systems is not just a technological advantage but a necessity. Cyber threats are evolving at an unprecedented rate, requiring businesses and individuals alike to arm themselves with efficient and proactive defense mechanisms. Imagine having an invisible shield, instantly reacting to any attempt to penetrate your digital walls. This is not science fiction—it’s the reality brought by advancements in cybersecurity systems. Gone are the days when security teams could afford to address threats after an attack had occurred; the need of the hour is real-time threat management.
Real-time threat management in cybersecurity systems offers a multifaceted suite of solutions designed to detect, analyze, and neutralize threats as they occur. Every second counts, and having a system that operates in real-time can mean the difference between a minor hiccup and a catastrophic breach. But what makes this technology truly captivating is its ability to adapt and learn, continuously evolving to match wits with cybercriminals’ latest tricks. By implementing real-time cybersecurity measures, businesses can protect their assets, data, and reputation, ensuring a safer environment for growth and innovation.
Why Real-Time Threat Management is Essential
The dynamic nature of cyber threats means that older methods of dealing with these dangers are now obsolete. With a real-time threat management system, businesses are not only protecting themselves against known threats but also against emerging ones. This kind of proactive defense provides peace of mind that cannot be undervalued. Additionally, it enhances operational efficiency, allowing for a smoother business transaction and minimizing downtime.
—
In our ever-evolving digital era, the parameters of cybersecurity are constantly being tested. Real-time threat management in cybersecurity systems has emerged as a transformative force, providing a robust defense against rapidly changing cyber threats. As technology surges forward, hackers and malicious actors devise crafty new methods to breach conventional defense mechanisms. Hence, the need for nimble, unwavering protection has never been greater.
Real-time threat management offers organizations the facility to detect and respond to threats instantaneously, akin to having a vigilant guardian on continuous patrol. These systems harness the power of artificial intelligence and machine learning to anticipate and thwart potential threats before they escalate into devastating breaches. The promise of immediate action and adaptation resonates with businesses that cannot afford data breaches or any consequential reputational damage. For real-time threat management in cybersecurity systems to be effective, it must integrate the latest technological advancements, offering layers of continuous protection.
The vitality of real-time threat management goes beyond simply blocking attacks; it encompasses comprehensive threat analysis, identifying the root cause, and adjusting strategies to prevent future occurrences. Yet, the technology is not without its financial implications. The initial investment is undeniably substantial, but the risk of operating without such security could be exponentially costlier. It’s the peace of mind and reliability that draws many businesses to invest in real-time threat systems.
The Future of Cybersecurity Systems
As we venture further into the digital age, real-time threat management in cybersecurity systems will no longer be an optional luxury but a standard expectation. This proactive approach ensures not just the protection of sensitive data but fortifies trust between a business and its clientele. The question for businesses is no longer “if” but “when” they will embrace real-time threat management. By evolving alongside technology, businesses can safeguard their future in an increasingly interconnected world.
Embracing Innovation in Cybersecurity
For real-time threat management systems to remain effective, staying ahead of hackers’ disruptive innovations is crucial. This means continuous research, development, and refinement of our digital shields. As these systems gain sophistication, the fusion of threat intelligence and real-time analytics will usher in a new era of holistic cyber safety.
—
Five Key Discussions on Real-Time Threat Management in Cybersecurity Systems
- The importance of integrating machine learning and AI for improved real-time analysis.
- How businesses globally react and adapt to cyber threats in real time.
- The role of user behavior analytics in enhancing cybersecurity systems.
- Challenges and misconceptions about implementing real-time threat management.
- The balance between cost and security investment in real-time threat solutions.
Introduction to Real-Time Threat Management
The phrase “real-time threat management in cybersecurity systems” might sound like something out of a sci-fi thriller, yet it has become a cornerstone of modern business strategy. With the surge in digital data and cyber attacks, companies can no longer rely on reactive strategies that leave vulnerabilities exposed until it’s too late. Real-time threat management affords businesses the ability to stay one step ahead of malicious actors by deploying technology capable of instantaneously monitoring, detecting, and neutralizing threats.
From multinational corporations to fledgling startups, the race to safeguard sensitive information has become a critical priority. Imagine for a moment the intricate digital dance that occurs every second of the day: billions of bits of data transmitted across global networks, each at risk of interception by cybercriminals. This isn’t to scare you but to underscore the gravity of the situation and highlight the necessity for robust cybersecurity frameworks.
Investing in real-time threat management systems is a proactive measure, much like a vaccine to guard against disease. Just as healthcare professionals champion preventative care, cybersecurity experts advocate for measures that preemptively shield against vulnerabilities. Ultimately, these systems are about creating a fortified IT environment where innovation and expansion can occur without the constant shadow of potential disaster looming overhead.
Navigating the Complex World of Real-Time Threat Management
Without real-time threat management, businesses expose themselves to multifaceted risks that could lead to devastating outcomes. These systems aren’t just a safety net; they are catalysts for business continuity and resilience. Implementing real-time threat management in cybersecurity systems is about aligning strategic goals with the inevitable evolution of digital threats.
Understanding the Technological Backbone
Real-time threat management systems are powered by intricate algorithms that relentlessly scrutinize network activity. They utilize machine learning and artificial intelligence to make lightning-fast analyses and decisions, predicting and neutralizing threats before they blossom into full-scale breaches. This intricate operation is designed to combat the evolution of cyber threats effectively.
Insightful Execution and Strategic Planning
The effectiveness of real-time threat management lies in its strategic execution, requiring seamless integration and constant updates. Businesses must prioritize employee education, ensuring everyone understands their role in maintaining the cybersecurity ecosystem. They need real-time insights to adapt their systems efficiently to combat evolving threats, turning awareness into action.
The prospect of employing such an advanced system invokes visions of exorbitant costs; however, in many cases, the benefits far outweigh the investments. It’s about understanding the long-term security and financial implications of cyber threats that can cripple operations. By deploying robust real-time threat management systems, organizations fortify their shield against cyber incursions.
The Human Element in Cyber Defense
While technology plays a pivotal role in cybersecurity, the human element cannot be overlooked. People are often the weakest link in the cyber defense chain, making education and training paramount. Real-time threat management provides a powerful tool, but without informed individuals at the helm, the full potential remains untapped.
Commitment to a Secure Digital Future
Embracing real-time threat management in cybersecurity systems is not just about facing present challenges but preparing for future threats. The continuous evolution of cyber threats requires a commitment to innovate and adapt, shaping a secure digital environment where progress is unobstructed by potential cyber threats.
—
Tips for Implementing Real-Time Threat Management in Cybersecurity Systems
- Integrate AI and machine learning for robust, real-time threat detection.
- Regularly update and patch systems to close known vulnerabilities.
- Conduct continuous employee training to heighten security awareness.
- Leverage user behavior analytics to detect unusual activity.
- Develop a comprehensive incident response plan.
- Invest in scalable solutions that grow with your business needs.
As businesses navigate the intimidating tides of cybersecurity threats, embracing real-time threat management emerges as a crucial strategy. Despite the complexities involved, these systems provide dual advantages of immediate threat detection and an analytical apparatus for future defense optimizations. The marriage between technological advancements and strategic planning presents an enriched cyber-defense narrative. Adaptation is crucial—organizations must remain vigilant, continually updating systems and educating employees to close vulnerabilities.
The vigor of a business parallels its cybersecurity stature. By adopting proactive measures, businesses demonstrate resilience against cyberattacks, subsequently safeguarding their reputations and client trust. Employing systems capable of evolving alongside the digital threat landscape speaks to a broader strategic initiative, reinforcing not just cybersecurity but fortifying business longevity.
With real-time threat management, businesses can now refocus on core objectives without the constant dread of impending cyber chaos. This aligns business goals with technological advancements, ultimately creating an environment conducive to growth. Embracing this proactive stance ensures businesses are not left vulnerable, highlighting real-time threat management in cybersecurity systems as a cornerstone for triumph in the digital domain.
—
In a world where data breaches and cyber attacks are commonplace, real-time threat management in cybersecurity systems stands as a beacon of hope and innovation. The value of protecting sensitive information cannot be overstated, with businesses needing to ensure that data remains safe from unauthorized access. The proactive nature of real-time threat management means anticipating and addressing potential threats before they become actualized.
A compelling real-life example involves a company that experienced a significant security breach due to outdated threat management strategies. After adopting real-time systems, not only did they stave off further attacks, but they also enhanced their overall security posture. This demonstrates the crucial shift many organizations must make—from reactive to proactive threat management.
Real-time threat management combines speed and intelligence, utilizing advanced algorithms and machine learning to identify and neutralize threats swiftly. This integration of cutting-edge technology ensures businesses are not just reacting but anticipating threats, providing an unprecedented level of security. As the world becomes increasingly digital, the role of cybersecurity becomes paramount.
Understanding the broader implications of real-time threat management sheds light on its necessity in modern business operations. It’s not merely about blocking attacks—it’s about cultivating an environment where innovation can flourish without the looming fear of cyber threats. Companies not only save resources by preventing breaches but also bolster their market reputation by showcasing a commitment to security.
The Role of Real-Time Analytics
Real-time analytics forms the backbone of these management systems, allowing businesses to extract valuable insights and adapt dynamically. By understanding patterns and anomalies in network behavior, organizations gain a strategic advantage, fortifying their defenses against an ever-evolving threat landscape. This predictive capability is invaluable in maintaining robust cybersecurity protocols.
The transition to real-time threat management is undoubtedly a strategic decision that reaps extensive benefits. By embracing this paradigm shift, businesses are securing their future, ensuring that as technology evolves, so too does their defense mechanism, keeping cyber threats at bay and promoting sustainable growth.