Hey there, tech enthusiasts! Welcome back to the blog, where we dive into all things cybersecurity with a side of casual chatter. Today, we’re talking about something that might sound a bit like jargon but is crucial for your network’s wellbeing: network segmentation security techniques. So, grab your coffee and let’s get into the nitty-gritty of how you can keep those pesky cyber threats at bay!
Why Network Segmentation Matters
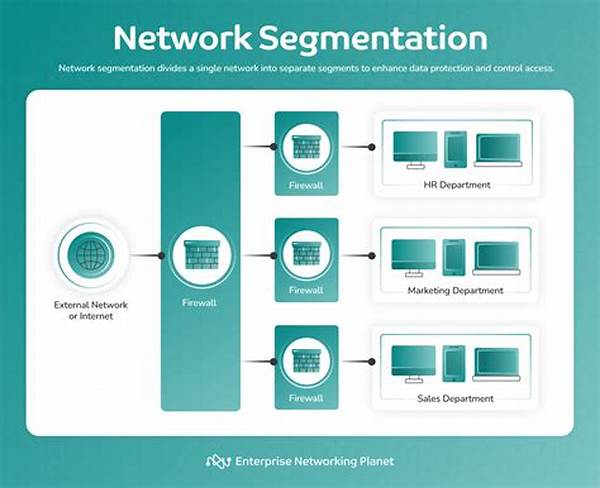
Alright, let’s kick things off with why you should care about network segmentation security techniques. Picture this: your network is like a house with tons of rooms. Now, imagine if a burglar got into one room and had access to every single space. Scary, right? Well, that’s where network segmentation comes in. It’s like putting locks on each room, so even if one gets breached, the others stay safe and sound. This technique is all about enhancing security by dividing a network into separate segments, and it’s a game-changer for protecting sensitive data from unauthorized access. Think of it as your network’s way of saying, “Not today, hackers!”
By implementing network segmentation security techniques, businesses can control who gets access to what, minimizing the risk of unauthorized usage or data breaches. It’s like having a VIP section for your most valuable data. Segmentation also helps in managing traffic more efficiently, improving the performance of your network by reducing congestion. So, not only does it protect your data, but it also makes sure your network runs smoothly. It’s the superhero your network never knew it needed!
Now, if you’re wondering how exactly these network segmentation security techniques work, you’re in luck. They involve setting up firewalls, creating virtual local area networks (VLANs), and employing subnets to section off parts of the network. It’s like the trifecta of security! So, stick around as we dive deeper into each of these techniques and get you on your way to fortress-level network security.
Key Components of Network Segmentation
Let’s break down the essentials of network segmentation security techniques. Here’s a quick-fire list to get you started:
1. VLANs (Virtual Local Area Networks): Creating logical segments even within the same physical network. They’re the neat partition markers.
2. Firewalls: The brave guards that monitor and control incoming and outgoing network traffic.
3. Subnets: These divvy up IPs to control group access, kind of like assigning seats on a crowded flight.
4. Access Control Lists (ACLs): Dictate who gets access to what within your network. Think of them as a VIP list for network rooms.
5. Jump Hosts: Special systems used to access a portion of the network securely.
With these tools, network segmentation security techniques provide a robust shield against data breaches and unauthorized access. Who knew your network could be this secure?
Benefits of Network Segmentation
It’s time to chat about why network segmentation security techniques are worth your time. First off, they reduce the attack surface of your network. Imagine eliminating the unnecessary paths a hacker might take—just like sealing off irrelevant corridors in a maze. It’s less room for intruders to snoop around!
Furthermore, segmentation enhances risk management. You can prioritize which sections of the network need beefier security based on the sensitivity level of their data. It’s like deciding which part of a castle deserves the thickest walls and strongest guards. Resources can be allocated more wisely, ensuring maximum protection where it matters most.
Lastly, these techniques improve detection and response times. With a segmented network, it’s easier to spot abnormal behavior in a small section rather than scanning the entire setup. Think of it as having sentry towers in strategic spots—if an alarm goes off, you’ll know exactly where to look!
Implementing Your Own Segmentation Strategy
Ready to dive into network segmentation security techniques? Let’s roll out a straightforward plan:
1. Assess Your Current Setup: Take a good look at your network’s layout. Identify where sensitive data resides and which areas need the most protection.
2. Plan the Segments: Categorize your network into segments based on access needs and data sensitivity.
3. Deploy Security Measures: Implement VLANs, subnets, firewalls, and ACLs to enforce segmentation.
4. Monitor and Adapt: Regularly review your network’s performance. Adjust segmentations and security rules to counter new threats.
5. Educate Your Team: Ensure everyone in your organization knows about segmentation policies and their importance. A bit of training goes a long way.
With these steps, you can tailor network segmentation security techniques to bolster your network’s defenses. And remember, it’s not a one-time gig; continual assessments ensure you stay armed against evolving threats.
Network Segmentation in Practice
Let’s talk applications of network segmentation security techniques in the real world. Start with segmenting by departments within a business. Marketing shouldn’t have access to HR data, right? By creating isolated segments, you can protect sensitive information while ensuring everyone has the tools they need to excel in their roles.
Another practical application is in the world of Internet of Things (IoT) devices. These gadgets can be entry points for cyber-attacks if lumped together in one network. But by employing network segmentation security techniques, you can separate them from critical systems, limiting potential breach avenues. It’s like letting your smart fridge be itself without risking the main system!
Lastly, consider remote work scenarios. With more professionals logging in from home, segmenting your network ensures secure access to resources without compromising the whole system. It’s a winning strategy for maintaining both flexibility and security standards in modern work environments.
Challenges in Segmentation
While network segmentation security techniques offer robust solutions, they aren’t without challenges. Initially, reconfiguring a network can be labor-intensive and require detailed planning—think of it as redecorating the entire house room by room!
Another issue could be maintaining balance. Segmentation can sometimes lead to communication barriers between departments or divisions. Ensuring seamless flow of information without compromising security can be tricky but essential for effective operations.
Lastly, there’s the challenge of scalability. As a business grows, its network needs change, demanding continuous assessment and restructuring of segments. It’s a dynamic process that requires flexibility and vigilance to remain effective in a fast-evolving tech landscape.
Wrapping Up Our Segmentation Adventure
Alright, time to cap off our deep dive into network segmentation security techniques! Hopefully, you’re now a bit more clued in on how these practices not only shield your network from potential threats but also enhance efficiency and control. By divvying up your network into smaller, manageable parts, you’re reinforcing boundaries against unwelcome visitors while streamlining your team’s workflows.
Whether you’re a small business owner just dipping your toes into cybersecurity or a seasoned network engineer refining your setup, these techniques have plenty to offer. Remember, the key to a strong defense is continuous evolution. Stay curious, keep learning, and always be ready to adapt—because cyber threats won’t wait!
Thanks for hanging out and exploring the world of network segmentation with me today. Don’t forget to drop your thoughts or questions in the comments section—I’m here to help your network stay as fortress-like as possible. Until next time, stay secure and surf smart, my tech-savvy friends!