Network Security Layers: The Multi-Layered Fortress Guarding Your Data
In the fast-paced digital era, where cyber threats lurk in the shadows, businesses and individuals alike face the constant challenge of securing their valuable information. Enter the concept of network security layers—a sophisticated, multi-layered approach to safeguarding digital assets. Imagine a fortress, each layer of brickwork representing a different level of security, each designed to thwart potential intruders. From corporate giants to small startups, everyone is joining the bandwagon to protect their digital realms. Why should you care? Simply because, in the digital age, data is the new gold. Leaving your information unprotected is akin to leaving vault doors wide open. This article will unravel the intricacies of network security layers by exploring their structure, effectiveness, and implementation.
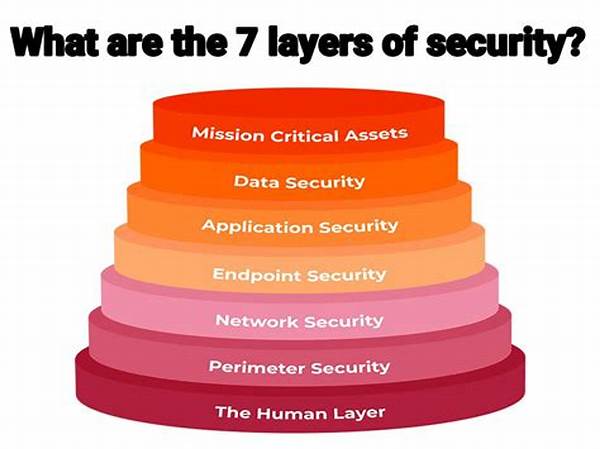
The layers in network security are akin to a series of sentinels, each battling a different threat. The intrigue lies in how each layer incorporates unique tactics, technologies, and strategies to bolster the defense mechanisms. Network security layers are not just a one-size-fits-all solution but rather a meticulously crafted ensemble designed to address specific vulnerabilities.
But why are network security layers the go-to solution? Their layered complexity is their strength, offering a blend of simplicity and sophistication. They provide a scalable solution that grows with your organization’s needs. With threats evolving every day—phishing, ransomware, DDoS attacks—having multiple lines of defense isn’t just beneficial; it’s critical. Companies vouch for its efficiency, and IT experts swear by its necessity. Are you still wondering if network security layers are right for you? The real question is, can you afford not to have them?
Integrating Network Security Layers in Your Organization
Having introduced the concept, you might be wondering how to apply these network security layers effectively within your organization. The first step involves understanding the various components that form these layers.
1. Firewalls: As the gatekeepers, firewalls control inbound and outbound traffic, ensuring unauthorized access is denied. They act as the first line of defense in network security layers.
2. Intrusion Detection Systems (IDS): These systems constantly monitor network traffic for suspicious activity, alerting administrators to potential threats, thus serving as an early warning system.
3. Antivirus and Anti-malware: This layer involves deploying software to scan and remove malicious software, ensuring your network remains virus-free.
The beauty of network security layers lies in their customizability. You can pick and choose the levels you need, like crafting a bespoke suit, ensuring it fits your unique organizational needs. It’s not just about keeping the bad guys out but also about reliably securing what’s inside.
Understanding the Pillars of Network Security Layers
Ensuring your network is secure requires an understanding of the core components of network security layers. In this section, we delve deeper into each of these critical layers to paint a clearer picture.
1. Access Control: This layer ensures that only those with the right permissions can access your network, preventing unauthorized users from entering.
2. Encryption: Vital for protecting sensitive information, encryption scrambles data so only those with the key can decipher it.
3. Network Segmentation: By dividing a network into various segments, unauthorized access is restricted to specific parts rather than the entire network.
Statistics reveal that companies investing in network security layers experience fewer breaches and more secure data handling processes. Don’t just take our word for it—consider the testimonials from organizations that have successfully integrated these layers and witnessed a significant drop in cyber incidents.
Summary of Network Security Layers
The Core Components of Network Security
Network security layers are essential in creating a formidable shield against cyber threats. But how can these layers be implemented effectively? Let’s discuss.
Research shows that adopting network security layers results in a 75% reduction in successful attacks, transforming businesses from vulnerable targets to robust entities. With these defenses in place, companies spend less time worrying about breaches and more time focusing on growth and innovation.
Implementing Network Security Layers Effectively
The journey to robust security is continuous and dynamic. With network security layers, organizations not only protect themselves but also stand as leaders in cybersecurity best practices. Now is the time to invest in comprehensive security that ensures peace of mind for you and your stakeholders.