In the realm of cybersecurity, Network Intrusion Detection Systems, also known as NIDS, serve as vigilant gatekeepers, constantly on the lookout for suspicious activities within a network. Imagine them as security cameras that not only record footage but alert you instantly when they detect something unusual. In an era where data has become as valuable as gold, organizations are increasingly investing in these systems to protect their digital assets. But what exactly makes these systems so crucial, and how can they transform your network’s security posture?
What are Network Intrusion Detection Systems?
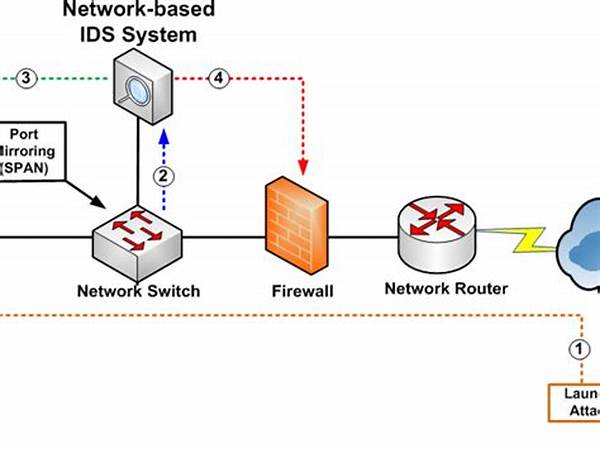
Network Intrusion Detection Systems play a pivotal role in identifying potential threats before they can cause any damage. They analyze inbound and outbound traffic, applying a set of predefined rules to flag anomalies. These systems are both reactive and proactive, capable of sending alerts for immediate human intervention or, in some cases, automatically taking steps to neutralize threats. Whether you’re a small business owner or a large enterprise, the appeal of having a robust NIDS in place is undeniable. It’s akin to having a seasoned detective who never sleeps, consistently working to protect your network.
There are two main types of Network Intrusion Detection Systems: signature-based and anomaly-based. Signature-based systems operate much like antivirus software, detecting threats based on known patterns. While effective against known threats, they might miss new or evolving attacks. Anomaly-based systems, on the other hand, use machine learning to understand the normal operations of a network and can detect deviations from this baseline. This dual approach ensures that whether an attacker uses a common tactic or a novel one, the chances of detection remain high.
While some might view the investment in Network Intrusion Detection Systems as an optional upgrade, testimonials from cybersecurity professionals consistently underscore their necessity. Many have shared stories of how NIDS intercepted malicious activities that other systems overlooked, highlighting the need for their implementation. With ever-evolving threats, investing in NIDS is no longer a matter of choice but a fundamental requirement for modern businesses.
Benefits of Implementing NIDS
Network Intrusion Detection Systems aren’t just about stopping the bad guys; they also offer a plethora of benefits that can vastly improve your network’s security strategy. For starters, NIDS provide real-time monitoring and analysis, ensuring you are always aware of the traffic trends within your network. This constant vigilance deters potential intruders, as they know their activities are being closely monitored.
NIDS also enhance your overall incident response plan. By providing detailed logs and alerts, they enable faster identification and mitigation of threats, reducing the potential damage and downtime a breach might cause. Furthermore, these systems can integrate with other security solutions, offering a comprehensive defense-in-depth strategy that enhances the overall security posture.
Investing in NIDS also sends a strong message to stakeholders and clients about your commitment to cybersecurity. As data breaches become headline news, demonstrating that you are proactive rather than reactive can bolster your organization’s reputation. In a world where trust can make or break a business, having robust measures like NIDS in place is not just wise; it’s essential.
Looking for a way to enhance your network’s defense? Look no further than Network Intrusion Detection Systems. Today, companies are turning a new leaf in the fight against cyber threats. These systems have come into the spotlight as unsung heroes providing the intelligent, adaptive security that modern networks require.
Types of Network Intrusion Detection Systems
With various types of Network Intrusion Detection Systems available, it’s important to understand which could be a perfect fit for your organization. Whether it’s signature-based systems known for identifying known threats or anomaly-based solutions using machine learning algorithms, the options are diverse. Signature-based NIDS act like a time-honored detective with a handbook full of known suspect profiles, sniffing out malicious patterns with precision. On the other hand, anomaly-based systems are akin to astute detectives who rely on their instincts and years of experience to suss out abnormal behavior. Each type has its merits and can cater to specific security needs depending on the organization’s focus.
In one recent case study with a tech-savvy startup, Network Intrusion Detection Systems managed to detect unusual traffic patterns indicative of a novel phishing attack. This automated alert system provided the IT team with precious time to block malicious IP addresses, saving potentially millions of dollars in damages. This example underscores the critical role that NIDS play in modern cybersecurity strategies.
In this digital age where cyber threats loom large, safeguarding your network is not just a priority; it’s imperative. Network Intrusion Detection Systems offer an exciting opportunity to elevate your cybersecurity measures. Their ability to detect, analyze, and respond to unusual network activities makes them an invaluable tool for organizations striving to protect sensitive data.
As businesses grow, so do the avenues for cyber threats. Enter Network Intrusion Detection Systems, robust solutions designed to monitor and defend against unauthorized access. Like having a sophisticated alarm system for your home, NIDS provide peace of mind and alert you to potential problems before they become disastrous. For organizations committed to securing their networks and earning trust, these systems are a game-changer.
Key Features of Network Intrusion Detection Systems
Understanding the key features of Network Intrusion Detection Systems can guide you in leveraging these tools effectively. Valuable features include real-time monitoring, comprehensive logging, alert system integration, and customizable threat detection parameters. In addition, advanced NIDS offer adaptability with machine-learning capabilities, allowing them to evolve alongside emerging cyber threats and adapt to new environments effortlessly. Their scalable design ensures they can grow with your business, consistently offering protection without compromise.
Through the lens of technological advancement, NIDS exemplifies the integration of artificial intelligence into everyday security protocols. Businesses now view them as crucial allies in the mission to protect valuable data assets. Navigating the ever-complex world of cybersecurity becomes less daunting with NIDS as part of your arsenal. Ready to add Network Intrusion Detection Systems to your cybersecurity toolkit? Dive into the types, features, and benefits and transform your security strategy today.