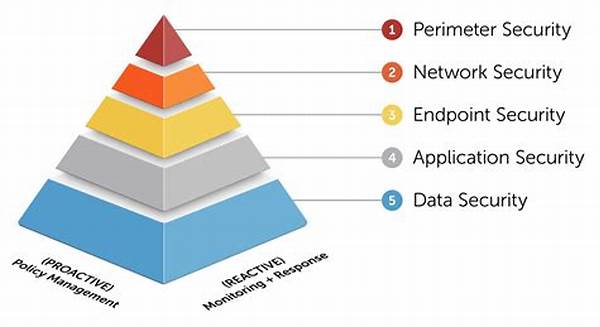
In the ever-evolving landscape of digital threats and cybersecurity challenges, companies today are forced to transform their approaches to ensure robust defenses against potential breaches. The concept of multi-layered security infrastructure planning is not just another buzzword but a strategic framework that businesses are adopting to enhance their security postures. As cybercriminals grow more sophisticated, so does the defense mechanism surrounding our critical data and tech infrastructures. Imagine your company’s defense system as an onion; the more layers you have, the harder it becomes to reach the core.
Read Now : Thorough Overview Of Ai Concepts
Think of it: a classic case of tech evolution met by an equally intense evolution in hacking techniques. This is where multi-layered security infrastructure planning shines. Consider how houses built in high-crime areas incorporate security fences, cameras, locked gates, and sometimes even guard dogs; each layer acts as both a deterrent and a point of failure management. The same principle applies to digital security, where every added layer complicates the intruder’s access path, buying valuable time for detection and response.
In today’s blog, unravel the allure of this planned defense strategy as we deep dive beyond the jargon. We’ll explore how this multi-faceted approach not only isolates threats but also enhances operational resilience. Hear from industry pioneers who have implemented these layers and discovered that a shield of organized chaos can be your best friend. So, gear up for an enlightening journey that combines humor, statistics, and stories to debunk myths, sprinkle tips, and maybe even incite a chuckle or two while pointing you toward better security strategies.
Why Multi-Layered Security is Crucial
A multi-layered security approach serves as a versatile umbrella of protection mechanisms, each capable of defending against distinct kinds of threats. This architecture is vital in adapting to the unpredictability of cybersecurity breaches. By deploying multiple defense strategies—from encryption to firewalls, antivirus software, and incident response—organizations can prevent vulnerabilities and manage intrusions more effectively. Once you appreciate the intricacies of these frameworks, it becomes clear why they are the cornerstone of any robust tech environment.
—
The Essence of Multi-Layered Security Infrastructure Planning
Adapting to the Dynamic Threat Landscape
In the digital age, adapting to an ever-changing threat environment is not just wise but essential, and this is precisely the forte of multi-layered security infrastructure planning. With malware, ransomware, phishing attacks, and more lurking around every cyber corner, each with unique characteristics, a single security layer is not sufficient. An integrated array of defenses provides a fallback system if one layer fails, offering a coherent response mechanism across multiple potential points of failure.
Maintaining a fortified front involves investing in cutting-edge solutions and customizing configurations to best fit organizational needs. This is the tactic that successful enterprises use to avert the chaos that ensues from singular-layer defenses collapsing. According to a recent study, companies employing at least three layers of security are 80% less likely to experience significant breaches than their less-prepared counterparts.
Implementing the Layers: A Tiered Defense Strategy
Implementing a multi-layered strategy involves an intelligent blend of technology, practices, and policies. From basic firewalls and intrusion detection systems to more sophisticated user authentication processes, each layer is an integral piece of the security puzzle. By investing in a variety of protective measures—such as antivirus programs, secure access controls, encryption protocols, and regular system updates—businesses can thwart numerous types of cyber incursions. The dynamic orchestration of these components enables organizations to operate with a peace of mind that single-layered defense simply cannot offer.
Read Now : Ontology-based Semantic Extraction
Benefits of a Multi-Layered Approach
Comprehensive Coverage and Flexibility
The advantage of multi-layered security infrastructure planning lies within its comprehensive coverage and inherent flexibility. It adapts fluidly to new threats while solidifying digital perimeters. Organizations can choose various technology mixes based on prevalent threats and environmental demands. This agility is critical in the current era, where cybercriminals continuously evolve their strategies. By cultivating a well-rounded approach, businesses can secure both current operational needs and future uncertainties effectively.
Enhancing Compliance and Corporate Assurance
In addition to thwarting digital threats, a multi-layered defense system aids businesses in complying with strict regulatory landscapes. Frameworks like GDPR, HIPAA, and others often mandate stringent security configurations which layered defenses support. Through meticulous implementation, companies can ensure their security systems are socially responsible, ethically sourced, and legally compliant, boosting consumer trust and elevating corporate reputation.
—
Strategies for Successful Multi-Layered Security Infrastructure Planning
A successful multi-layered security approach requires collaboration between IT departments, policy makers, and all stakeholders involved in the technology ecosystem. Proper training and constant refreshing of best practices are pivotal. Innovating continuously and remaining vigilant allows for preparation not solely against immediate threats but latent ones as well. Get inspired by industry innovators who share their testimonials about pivoting to a multi-layered architecture for holistic digital protection and organizational resilience.
Key Components of Multi-Layered Security
The Path Forward: Top Tips
Multi-layered security infrastructure planning isn’t just an industry term—it’s the future of safeguarding the digital world. Adopting such an approach ensures that whether you’re a small startup or a large corporation, your operations can withstand the evolving landscape of cyber threats with confidence and competence.