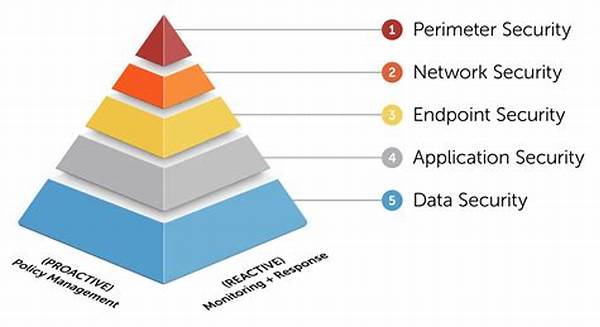
Multi-Layer Security Protocols
In an ever-evolving digital landscape, safeguarding sensitive information is paramount. Welcome to the world of multi-layer security protocols, the unsung heroes behind your data’s protection! Imagine venturing into a mystical fortress laden with layers of armor, each designed to fend off lurking cyber threats. With each passing second, organizations and individuals alike depend on these robust systems. Why settle for average when the digital realm offers exclusivity?
Our journey begins with a captivating tale of innovation and defense. Picture yourself navigating through a complex yet fascinating maze. As you traverse each layer, you’ll uncover the intricacies that make multi-layer security protocols both indispensable and fascinating. These protocols don’t just stand guard; they raise the battlements, deploy the archers, and arm the knights—all while ensuring seamless user experience. Let’s delve deeper into the first layer and discover its significance in the grand scheme of cybersecurity.
In our first layer, we find encryption—a fundamental and vital protector of data. Encryption works like a lock and key mechanism, making data indecipherable to unauthorized access. By translating information into secure codes, it ensures the safe transmission of data. It’s like speaking in a secret language, understood only by the intended recipient. But encryption is just the beginning! Every defense mechanism plays its role in this well-orchestrated security ensemble.
As we scratch the surface of comprehensive digital protection, the multi-layer security protocols thrive on diversity. They integrate firewalls to block unwanted intrusions, employ virtual private networks (VPNs) to cloak activities, and deploy intrusion detection systems for early threat warning. Harnessing the power of diversity, these protocols optimize each layer for top-notch defense. And, like a spectrum of colors blending to craft a masterpiece, they create a seamless security experience that’s second to none.
Understanding the Multi-Layered Approach
Yet, our tale is far from complete. Multi-layer protocols are not just about technology but involve people and education. Awareness campaigns form the backbone of risk mitigation, transforming human errors into informed decisions. Picture a company, once vulnerable, now fortified through regular training sessions, empowering employees to become first-line defenders. Imagine the synergy of technology with trained minds, crafting an unbreachable fortress against potential threats. Together, they epitomize the epitome of cybersecurity.
—
An In-Depth Look Into Multi-Layer Security Protocols
In the bustling world of cybersecurity, multi-layer security protocols are a shining beacon, guiding organizations towards a safer digital haven. But what makes these protocols so effective, you ask? Let’s dive into the secrets of their craftsmanship and why they are the preferred choice for many seeking a formidable defense arsenal. If you’ve ever pondered over enhancing your security, prepare to be intrigued!
First up, the core concept of layering is pivotal. Multi-layer security protocols aren’t one-size-fits-all solutions. Instead, they combine multiple technologies and practices, tailor-suiting themselves to the unique demands of any environment. The rationale? Much like dressing for unpredictable weather, layering keeps the vulnerabilities at bay. Each layer addresses a specific weakness, nullifying potential threats like a seasoned gladiator on battle grounds.
Have you ever considered the mind-boggling statistics of cyber threats? Reports suggest a continuous rise in cyber-attacks, with businesses losing billions annually. Here’s where multi-layer security protocols shine, reducing the threat landscape to nearly a flat plain. By leveraging firepower drawn from antivirus, anti-malware, and sophisticated authentication methods, they safeguard data and resources. The beauty lies in their redundancy; should one layer falter, another kicks into action.
What makes this defense system unique is its adaptability. According to recent research, adaptable security systems respond to evolving threats in real-time. With multi-layer security protocols, the defensive boundaries continuously morph, evolving with the digital ecosystem’s dynamic nature. Imagine a stealthy chameleon, shifting hues to blend with its surroundings. In cybersecurity, static defenses are relics. Instead, proactive adaptation wins the day.
Campaigns highlighting the protocol’s efficacy are more than just informative—they’re revolutionary. Hearing testimonials from businesses transformed by these methods adds a layer of credibility and relatability. Consider a startup priorly vulnerable, rejuvenated post-implementation, investing in growth and innovation without lurking fears. The narrative of secured innovation sells itself!
One cannot overlook the emotional aspect. How secure do you feel working from a protected environment? The sheer tranquility of knowing your data—regardless of being a multinational conglomerate or an individual—remains impenetrable is invaluable. Imagine the peace of mind as vast networks spread security’s charm, reaching far and wide. Now, that’s what I call multi-layered peace of mind!
To conclude, adopting multi-layer security protocols transforms the digital nightmare into a safe, seamless dreamland. Taking action to secure your fortress is imperative. Reach out to professionals, learn, adopt, and let the multi-layered symphony orchestrate harmony in your digital realm. Whether it’s your corporate data on the line or personal information, no measure of cybersecurity is excessive when multi-layer security protocols laurel the crown of ultimate safety.
—Essential Actions with Multi-Layer Security Protocols
Discovering the Dynamics of Multi-Layer Security Protocols
Behind every cyber-safe organization, there’s a playbook of intricate protocols. Let’s explore these steps deeper. Encryption is a fundamental tool, offering confidentiality and safeguarding data from interception. Imagine it as writing a secret diary, only you and your confidante can unlock its pages.
Buffering the entry points of your network lies a firewall – consider these as the bouncers of your digital nightclub. Only verified guests enter, while potential threats are turned away. It’s a simple yet effective way to manage what comes through your digital doors.
VPNs, a rather nifty invention in the evolution of networking, act as your online invisibility cloak, masking your IP, and allowing anonymous browsing on public networks. Imagine the salacious gossip remaining locked away, as prying eyes cannot decipher where or what’s happening on your side of the screen.
No matter how robust the tech is, employee awareness plays a critical role. Regular training molds individuals into vigilant cyber warriors, ensuring multi-layer security protocols receive human support, reducing errors and subsequent vulnerabilities. With this dynamic synergy, companies promote resilience organically.
Building an environment secured by multi-layer protocols is akin to fortifying a castle—each part has its role. As threats evolve, so must defenses. Procedures must be flexible, adjusting like a river stream changing course. A solid incident response plan acts as your emergency protocol, assuring timely and effective resolutions for any breaches encountered.
This elaborative multi-layer security setup empowers users beyond just technology; it’s a blend of techniques braided with human intellect. A commitment to these practices ensures not just data safety but a peace of mind – a luxury often underrated when it comes to digital engagement.
—
Implementing Effective Multi-Layer Security Protocols
Seven Tips for Implementing Multi-Layer Security Protocols:
Securing the digital fortress is more important than ever. As we emphasize the process, conducting frequent risk assessments ensures you build a solid foundation. It’s like checking the integrity of every brick before constructing a building; audits let you identify and eliminate vulnerabilities.
Leveling access turns out to be a valuable strategy. The ‘least privilege’ principle ensures users only access what they need, nothing more, guarding against unnecessary leaks. Just as you don’t hand the whole treasure map to an apprentice, privilege scaling preserves core secrets.
Market-leading security software offers complex coding strength but introduces simple usability. Selecting dependable software brands translates to easy implementation without diluting the strength of these multi-layer security protocols.
Security’s human element remains critical. Regular employee training not only enhances vigilance but builds a proactive culture. Consider it spreading knowledge like wildfire, igniting every team member’s security consciousness, turning them into active protectors.
There’s more behind the scenes—employing threat detection systems acts as backstage security guards. Real-time anomalies and suspicious behavior can be swiftly countered, much like an alert bodyguard intercepting peril before it reaches the star.
A robust backup system offers a digital safety net, ensuring business continuity even during breaches. Adequate preparation guards you against data loss, enabling swift recovery as operations resume smoothly.
Finally, compliance with regulations isn’t merely legal necessity—its active protocol enhancement. Legal alignment reflects responsibility and deters heavy penalties, ensuring you remain the true king of your digital realm, ruling with an iron-clad defense—thanks to your multi-layered strategies.
—Exclusive Insights into Multi-Layer Security Protocols
Exploring the myriad possibilities within the realm of cybersecurity, one realizes the pivotal role multi-layer security protocols play in modern digital defense. They’re no mere tech buzzwords; instead, a comprehensive strategy safeguarding countless bytes of data daily. This storytelling venture into the heart of these protocols brings forth unfiltered insights into their necessity and implementation.
Multi-layer security protocols are like a well-oiled machine, designed to counteract varied levels of cyber threats. Imagine this: you walk into a grand fortress, flanked with several defensive barriers; each barrier represents a unique security protocol crafted to ward off intrusions. In today’s cyber battlefield, where threats take numerous shapes and forms, relying on a singular strategy is akin to inviting calamity. Hence, diverse protective layers form a comprehensive buffer, offering myriad defenses—an FPV drone fleet overseeing the entire vicinity, if you will.
Nowadays, businesses overly reliant on primitive defense mechanisms find themselves vulnerable. Integration of modern multi-layer security protocols provides them an upgraded arsenal. Yet, what separates successful organizations is not simply adopting technology, but nurturing a robust, inquisitive culture. Through regular education, teams embrace cutting-edge strategies while stripping down old vulnerabilities.
A focused approach forms the backbone of robust cyber hygiene. The blend of automated systems and knowledgeable users becomes crucial. As threats morph at alarming rates, real-time incident management controlled by both man and machine averts potential disasters. Recall iconic sci-fi films where intelligent systems collaborate with humans to counter threats physically—transpiring before our digital eyes.
Secure networks aren’t confined to direct cyber threats but encapsulate personal safety, privacy, and client trust. Confidence in digital interactions raises overall experience standards and fosters an environment where creativity can thrive unburdened by apprehensions. It affixes a brand to a golden pedestal—reassuring users of priority in privacy commitment.
Chart this course, imagine your enterprise as a flagship equipped with these protocols, emboldened, and nurtured to blossom without borders. Envision your workforce, armed with knowledge and partnered with technology, navigating uncharted waters—a cyber ocean filled with possibilities. Here lies a beacon for digital existence, branded with security excellence, all thanks to the marvel of multi-layer security protocols.
Adopting these protocols? Step forward into the world of digital fortresses, grow and flourish amidst the cyber equivalent of the high seas. This transformed narrative is your narrative—ready to unfold, exclusive and secured, in your digital domain.