In the modern digital age, where cyber threats loom large and data breaches make headlines, organizations are in a relentless pursuit of robust intrusion detection mechanisms. The adage “prevention is better than cure” rings true here more than ever. As cybercriminals become more sophisticated, traditional methods of detecting network intrusions often fall short. This is where the transformative power of machine learning steps in, offering a glimmer of hope for those yearning for enhanced security protocols. The machine learning models for intrusion detection promise not only innovation but also a significant leap in spotting and responding to cyber threats with improved efficiency.
Imagine a world where machine learning models for intrusion detection seamlessly integrate with existing systems, transforming data into actionable insights with a flick of an algorithm. The promise of machine learning in intrusion detection is akin to a superhero offering a shield against the villains of the cyber world. Yet, beyond the flashy allure, there are layers of complexity and intricacies that deserve a closer examination. So, how do these models operate, and what makes them indispensable in the fight against cyber threats?
With cyber-attacks becoming a daily occurrence, businesses are left with no choice but to adapt and evolve. From phishing scams to advanced persistent threats, the landscape of digital threats is as diverse as it is dangerous. Machine learning models for intrusion detection stand as the sentinels of digital fortresses, constantly vigilant and ever-learning. They sift through massive data warehouses, detecting anomalies and identifying potential threats faster than any human eye could. However, the journey of these models from theory to practice is a narrative filled with challenges, triumphs, and continuous learning.
Organizations aiming to harness the full potential of machine learning models for intrusion detection must understand the models’ architecture, data requirements, and the integration process. It is not merely a matter of flipping a switch; it requires strategic planning, understanding the unique needs of your organization, and sometimes, a dash of creativity. With the right approach, machine learning not only enhances security but also offers a competitive edge in the digital landscape. The journey, while daunting, is a rewarding endeavor that underscores the adage that in the realm of cybersecurity, forewarned is indeed forearmed.
The Revolution: How Machine Learning Enhances Security
Machine learning models for intrusion detection are not just a technological upgrade, but rather a revolution in the cybersecurity domain. Their ability to learn from data continuously and evolve with emerging threats makes them a cornerstone of modern network security protocols. These models bring a unique advantage — the ability to detect patterns and anomalies that might go unnoticed by traditional systems. As cybersecurity continues to evolve, so does the sophistication of the attacks, necessitating an equally sophisticated defensive mechanism.
—
In cybersecurity, remaining a step ahead often means the difference between thwarting an attack and becoming the next headline. It’s akin to being a chess player anticipating the opponent’s moves three steps ahead — an analogy that perfectly captures the essence of machine learning models for intrusion detection. As threats evolve, these models adapt, learning from vast datasets, identifying patterns, and predicting future vulnerabilities. But how do they fit into the broader cybersecurity ecosystem?
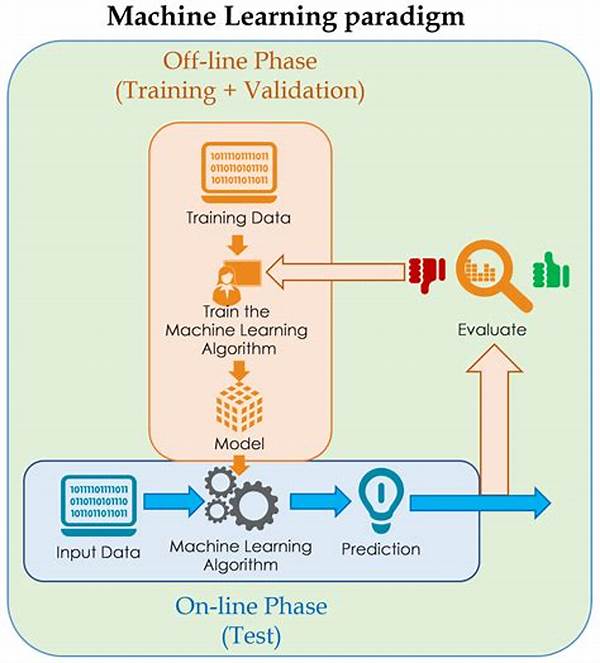
At their core, machine learning models for intrusion detection capitalize on algorithms designed for pattern recognition. Picture them as digital detectives, tirelessly scanning network activity, picking up the faintest whispers of irregularity in a sea of data. They utilize supervised and unsupervised learning techniques, learning from past data to predict future anomalies. The impact? A significant reduction in false positives, faster response times, and heightened overall security.
Yet, introducing machine learning into intrusion detection is not without its challenges. Entities must ensure that their data is clean, unbiased, and comprehensive. A biased dataset can lead to catastrophic oversights, making it crucial for organizations to invest in data integrity as much as in the algorithms themselves. Moreover, the human element still plays a vital role. While machine learning can analyze and predict, having skilled cybersecurity professionals interpret and act on these findings is indispensable.
The promise of machine learning models for intrusion detection extends beyond immediate threat detection. They offer insights into potential future threats, allowing organizations to fortify their defenses proactively. By continuously analyzing data, these models identify patterns that may suggest a brewing threat, providing a strategic advantage over malicious actors. The result? A dynamic, responsive cybersecurity strategy that’s as fluid as the threats it seeks to neutralize.
Not Just a Tool, But a Strategic Partner
Harnessing the Power of Data
Machine learning models for intrusion detection are not just tools; they are becoming strategic partners for organizations intent on maintaining data security. These models continuously adapt, learning from every piece of data they process. They’re akin to having a vigilant, ever-diligent security guard that perceives not just the immediate risk but the potential for future threats.
—
Goals of Machine Learning Models for Intrusion Detection
As the digital realm expands, so does the need for sophisticated security systems. Machine learning models for intrusion detection provide an edge, evolving with the ever-changing landscape of cyber threats. They don’t just detect known threats, but predict potential vulnerabilities, serving as a preemptive strike against what could be.
These models leverage vast datasets, frequently updating and learning from each interaction. This ability to self-improve is crucial in a domain where yesterday’s defense mechanisms may be obsolete today. It’s like having a security system that grows smarter and more intuitive each time it encounters new data. For organizations, this means a robust defense not just against current threats, but future ones as well.
Yet, adopting these models isn’t merely a plug-and-play solution. It requires strategic planning and often, a cultural shift within the organization. The perception of machine learning in cybersecurity needs to be one of partnership, where both technology and human expertise are integral to the solution. When effectively integrated, the value provided is not just in enhancing security but also in driving operational efficiencies and building trust with stakeholders.
Bridging the Gap Between Man and Machine
Adapting to a New Security Paradigm
Machine learning models for intrusion detection bridge the gap between human skills and machine efficiency. They serve as a testament to how technology and human intelligence can collaborate to create a future where security is proactive rather than reactive.
—
Seven Tips for Implementing Machine Learning Models for Intrusion Detection
When embarking on the journey of implementing machine learning models for intrusion detection, there are crucial considerations to keep in mind. The path is not linear, littered with challenges yet ripe with opportunities. A successful implementation relies heavily on understanding the unique needs of the organization and how these models can be tailored to meet those needs effectively.
Moreover, these models require constant nurturing. Security threats evolve, and so must your defense mechanisms. The real power of machine learning models lies in their adaptability — their ability to learn and recalibrate in real time. But even the best models need oversight, and periodic reviews can ensure that they remain aligned with organizational goals and security needs.
Finally, the human component cannot be overlooked. Machine learning models augment human capabilities; they do not replace them. Training and educating teams on utilizing these powerful tools effectively ensures that companies can fully leverage their potential, creating a formidable defense against the ever-looming cyber threats.
—
By integrating machine learning models for intrusion detection, businesses stand in good stead to not only detect potential threats but to foresee and neutralize them before they even materialize. This proactive approach, underpinned by technological advancements and human expertise, marks a new era in cybersecurity. It’s an investment in peace of mind, where vigilance doesn’t rest and security isn’t just a process but a culture.