Hey there, tech enthusiasts! Today, we’re diving into the world of layered security architecture implementation. Sounds intriguing, right? It’s like stacking security blankets, but for your digital realm. Just as you wouldn’t rely solely on a single lock for your house, neither should you depend on a single line of defense for your IT systems. So, sit back, grab a cup of your favorite brew, and let’s unpack what this is all about.
Why Layered Security Matter
Think of layered security architecture implementation as creating multiple hurdles for any potential threat. It isn’t just putting locks on your doors but also sensors, cameras, alarm systems, and even a friendly neighborhood watch. Each layer plays a crucial role, from firewalls blocking unauthorized traffic to antivirus software zapping malicious code. By the time a hacker makes it through one, there’s another waiting for them. It’s essentially a game of chess where you’re always a few steps ahead. The beauty of this approach? It drastically reduces the chances of any nasty surprises popping up in your network.
Now, let’s think about how this all fits together. Imagine your network as a treasure chest. The jewels inside? That’s your sensitive data. With layered security architecture implementation, you’re putting guards at every entrance, employing the best alarm systems, and maybe even a few safeguard decoys to throw off unwanted visitors. The idea is not merely about keeping the hackers out but making their lives so complicated that they decide to give up and move on. By integrating diverse defenses, like encryption, access controls, and intrusion detection, you’re ensuring a resilient shield around your digital treasure chest. It’s the foundation of peace in the cybersecurity realm.
The Building Blocks of Layered Security
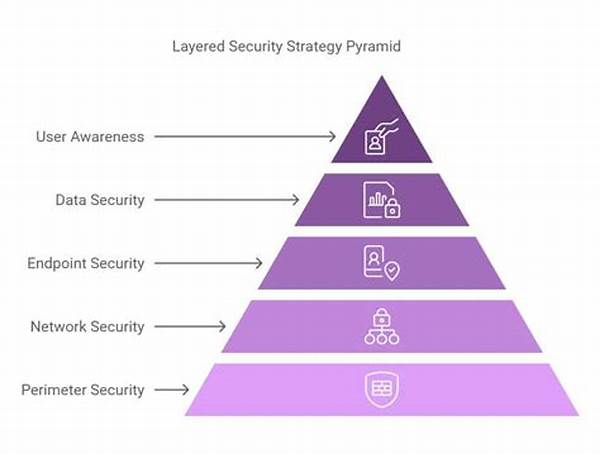
1. Firewalls First: This is your first line of defense. During a layered security architecture implementation, a firewall filters incoming and outgoing network traffic based on predetermined security rules.
2. Antivirus Action: Keep those pesky viruses at bay. Antivirus software continually scans and identifies malicious software as part of the layered security architecture implementation.
3. Encryption Endeavors: Encrypt your data to prevent unauthorized access during its transmission and storage, a crucial part of layered security architecture implementation.
4. Access Control Acumen: Ensure that only authorized personnel have access to specific data or systems. This step is vital in layered security architecture implementation.
5. Intrusion Detection Systems (IDS): These systems are your vigilant guards, spotting suspicious activities and alerting you in real time, integral to any layered security architecture implementation.
Implementing Effective Strategies
When you’re ready to dive into the world of layered security architecture implementation, start with a solid game plan. Identify what assets need the most protection and tailor your security layers accordingly. It’s all about creating a personalized set of defenses that match your organization’s specific risks and needs. Perhaps you need more robust encryption methods or increased monitoring of outsider access. With careful planning, each layer reinforces the next, crafting a resilient, dynamic security posture.
As we geek out over this tech marvel, remember that technology alone isn’t enough. Alongside implementing strong security architectures, nurturing a culture of security awareness within your organization is essential. Train your employees to recognize potential threats, like phishing attempts. After all, humans can be both the weakest link and the staunchest defenders in the security chain. It’s about evolving together and aligning cybersecurity strategies with day-to-day operations for holistic protection.
Understanding the Importance
Let’s break it down: implementing layered security architecture isn’t just a technical maneuver; it’s about peace of mind. You can’t predict every potential cyber threat, but you can prepare for them. By wrapping your digital realm in layers of security, you’re essentially telling cybercriminals, “Not today, buddy!” Think of it as setting up a series of fail-safes against unforeseen crisis moments. This approach not only shields but deters potential breaches from even considering your system a viable target.
With a smart layered security architecture implementation, it’s like having a fortress with multiple walls. It’s about strategy, foresight, and dedication. Consider it your organization’s defense choreography, where each layer performs a specific protective dance. The end goal of all these efforts? It’s not just being equipped against attacks but achieving resilience that adapts and responds to new threats. So, next time you think about security, picture it as an evolving story rather than a static solution.
The Role of Human Elements
Let’s not forget; in all this tech talk, the human element is key. While software and hardware form the backbone of security measures, human intelligence adds a dynamic layer of defense. Regular training and awareness programs can transform your team into savvy security warriors. Encourage active discussions around layered security architecture implementation and make cybersecurity a part of everyday conversation. An informed team is a crucial part of creating safer digital ecosystems.
The beauty of incorporating humans into this architecture is their ability to adapt, learn, and outsmart potential threats. Machines can process data at lightning speed, but they rely on human oversight for strategic decisions. By fostering a culture that values security, you aren’t merely installing layers; you’re invigorating each layer with the human intuition and creativity that machines can’t replicate. It’s this human-machine synergy that forms the heart of effective layered security architecture implementation.
Wrapping It Up
So, what’s the final takeaway in this layered security architecture implementation journey? Technology, strategy, and human insight blend to create a robust defense system. In our interconnected world, vulnerabilities lurk in unexpected corners. With a thoughtful mix of protective measures, you’re not just reacting to threats but creating a proactive shield. Remember, implementing such an architecture is a journey, not a destination. It’s all about continuous refinement.
These layers ensure that even if one defense fails, others stand ready to protect. So, whether you’re a small business or a large corporation, always prioritize layering your defenses. By embracing a layered security architecture implementation, you’re safeguarding precious data and paving the way for a resilient future. Keep learning, adapting, and revisiting your security strategies. The digital realm is ever-evolving, and your approach should be as well. Secure your chain; secure your future!