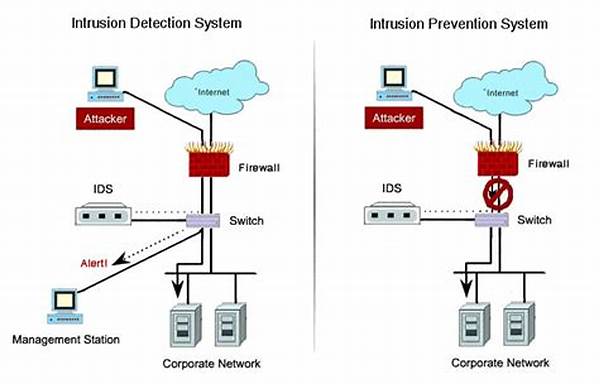
Intrusion Detection and Prevention Systems
In today’s digital age, where every click, transaction, and message moves at the speed of light, the necessity of securing our digital environment is paramount. The unsung heroes in this field are the Intrusion Detection and Prevention Systems (IDPS), acting as vigilant sentinels to safeguard our networks. With cyber threats growing increasingly sophisticated, these systems employ a mixture of proactive and reactive measures to not only detect potential intrusions but prevent them altogether. Imagine having a virtual bodyguard that can anticipate a threat before it manifests, neutralizing it in real-time. The magic lies in their ability to learn and evolve, adapting to the changing landscape of cyber threats. For anyone serious about protecting their digital assets, understanding and employing these systems is not just an option but a necessity.
The modern IDPS is designed to provide an umbrella of security through real-time monitoring and analysis. By continuously scanning for unusual patterns and behaviors, these systems alert network administrators of any abnormalities, allowing for swift responses. With data breaches costing companies millions, the role of intrusion detection and prevention systems cannot be overstated. It’s like an insurance policy, but one that actively prevents damage from occurring in the first place.
Moreover, in a world where data is as valuable as gold, businesses cannot afford to be reactive. Implementing an IDPS system is an investment that pays dividends. Not only does it protect sensitive information, but it also safeguards a company’s reputation. Many businesses have been left reeling in the aftermath of a cyber-attack because they underestimated the value of such security measures.
Finally, the adaptability of these systems makes them indispensable. As cyber threats evolve, so too do intrusion detection and prevention systems, utilizing machine learning and AI to stay one step ahead. They provide peace of mind, ensuring that as digital landscapes evolve, businesses remain protected from potential threats, armed with the latest in security tech.
The Evolving Role of Intrusion Detection and Prevention Systems
IDPS have evolved over the years, from basic logging tools to complex systems utilizing AI and machine learning. Their evolution is a testament to how crucial they’ve become in our increasingly interconnected world. These systems are not just about protection; they’re about maintaining trust. In industries where customer data is paramount, ensuring its protection is both a legal and moral obligation. Thus, IDPS is the unsung hero, quietly operating in the background, ensuring that every piece of data is safe from prying eyes.
—Introduction to Intrusion Detection and Prevention Systems
The digital era has spawned not only unparalleled convenience and connectivity but also a vast array of security challenges. As businesses transition to digital platforms, the risk of cyber threats looms larger than ever. Enter the world of Intrusion Detection and Prevention Systems (IDPS), a crucial line of defense in the realm of digital security. These systems are both our shield and sword in the battle against cyber intrusions, ensuring that networks are not only secure but also resilient.
At the heart of any effective cybersecurity strategy is the ability to respond aptly to threats as they emerge. Intrusion Detection and Prevention Systems act as the nerve center of such strategies, constantly monitoring and analyzing traffic to pinpoint threats. With cyber attackers becoming savvier, the role of IDPS evolves rapidly, marking it as indispensable in the digital security toolkit.
In a world where data breaches have become commonplace, the ability of intrusion detection and prevention systems to combat these threats is critical. An IDPS essentially acts like an ever-vigilant virtual security guard, scrutinizing network activity for signs of danger and acting before it’s too late. The potential losses from cyber attacks include not just financial damages, but also reputational harm that can take years to rebuild.
The core function of IDPS lies in their ability to detect and prevent unauthorized activities on networks. Whether it’s a case of malware trying to siphon sensitive data or a covert attempt to compromise system integrity, IDPS are designed to thwart such efforts. Their role in maintaining business continuity, therefore, cannot be overstated.
Furthermore, intrusion detection and prevention systems are not static entities. They incorporate the latest in machine learning and artificial intelligence to stay ahead of cybercriminals. This means they are continuously learning and adapting to new threats, ensuring that businesses always have the upper hand.
The Components of IDPS
The Value Proposition of IDPS
Investing in intrusion detection and prevention systems is an act of forward-thinking. It is about safeguarding the future of businesses by ensuring the security of digital operations today. The cost of neglecting this vital aspect can be devastating. Thus, the story of any modern enterprise seeking sustained growth and trust is incomplete without the inclusion of robust IDPS solutions.
—Key Features of Intrusion Detection and Prevention Systems
Understanding How IDPS Works in Practice
Intrusion Detection and Prevention Systems (IDPS) operate through a combination of detection and response tactics. When an anomaly is detected within network traffic, these systems act swiftly to contain the threat, preventing any potential data leaks or unauthorized access. By employing both signature-based detection, which looks for known patterns of threats, and anomaly-based detection, which identifies unusual patterns, IDPS offer a robust security net.
In one case, a large corporation avoided a significant breach due to their IDPS detecting an unusual data transfer at an odd hour. With immediate alerts and automated lockdowns, the threat was neutralized before it could cause harm. Such real-world applications demonstrate the effectiveness and necessity of IDPS in today’s cybersecurity strategies.
Implementing Intrusion Detection and Prevention Systems
The implementation of IDPS involves evaluating the specific needs of a network and selecting a system that complements the existing infrastructure. Businesses need to consider factors like scalability, ease of integration, and the level of customization required. Training on managing the IDPS for IT staff is also essential, ensuring systems function optimally and staff remain vigilant.
Regularly updated, IDPS systems ensure that businesses can adapt quickly to emerging threats, maintaining a defensive posture that instills trust among clients and partners alike. For industries handling sensitive data, such confidence is paramount.
Why Every Business Needs an IDPS
The more reliant a business becomes on digital infrastructure, the greater the necessity for a robust intrusion detection and prevention strategy. From e-commerce platforms to financial institutions, the risks of not implementing such systems can lead to catastrophic data breaches. As the adage goes, it’s better to be safe than sorry, and investing in an IDPS is one of the soundest ways to protect a business’s digital future.
—Tips for Choosing an Intrusion Detection and Prevention System
Choosing the Right IDPS for Your Business
Selecting the suitable intrusion detection and prevention system can mean the difference between a minor security incident and a major data disaster. Many IDPS vendors offer custom solutions tailored to specific industries, understanding that no two networks are identical. The first step is conducting a comprehensive risk assessment to identify potential vulnerabilities within your network.
Understanding the nuances of each system, from their detection capabilities to their integration ease, is crucial. A mismatch in either aspect can lead to inefficient operations and potential vulnerabilities. Therefore, the decision to choose and implement an IDPS should be made with careful consideration of both present and future needs.
Engage with vendors to discuss how their systems align with your business goals and digital environment. Often, this collaboration results in a tailored solution that offers optimal protection while maintaining operational efficiency.
Ultimately, the investment in a reliable intrusion detection and prevention system is not merely an expense but a proactive step towards safeguarding an organization’s digital assets, reputation, and future growth.
—Intrusion Detection and Prevention in Daily Operations
The backbone of any effective cybersecurity framework, Intrusion Detection and Prevention Systems (IDPS), continually monitors and safeguards an organization’s information systems. Imagine IDPS as the vigilant guardian, observing network traffic patterns like an elite detective. Detecting anomalies and thwarting unauthorized access is their forte, ensuring businesses remain shielded from insidious cyber threats. While some perceive cybersecurity as the domain of IT aficionados, intrusion detection, and prevention is practical, tangible, and necessary for everyone who cherishes data integrity.
In a humorous twist, think of IDPS as the network’s night watchman, donning a virtual detective hat. Whether it’s thwarting bad actors or simply sending gentle reminders (“Hey, this password isn’t very strong!”), IDPS are the unsung heroes of the digital age. Like a seasoned investigative journalist, they methodically pursue leads—only their fieldwork involves algorithms and data packets.
IDPS and the Modern Cyber Landscape
As cyber threats evolve, businesses face the dual challenge of adapting to new digital technologies while simultaneously fending off threats. Traditional security measures no longer suffice; it’s here that IDPS comes into play, merging detection capabilities with preventive measures for a more integrated approach. What sets IDPS apart is their adaptability, continuously updating algorithms to identify and halt emerging threats.
These systems aren’t static; they’re empowered by AI and machine learning, making them adept at spotting even the subtlest of digital deceptions. It’s like having an adaptable ace up your sleeve in the unpredictable game of cyber defense.
In a landscape where a simple data breach can tarnish reputations and cost millions, the emphasis on adopting a formidable IDPS has never been greater. The cornerstones of any thriving business in the digital age are vigilance, adaptability, and robust defense mechanisms—embodied perfectly by Intrusion Detection and Prevention Systems.
The IDPS Toolbox
With features ranging from real-time monitoring to automated threat response, IDPS systems are designed to act swiftly and decisively. Visualization tools provide clear, actionable insights, while seamless integration capabilities ensure they work harmoniously with other security tools. The ability to learn from previous encounters makes these systems invaluable in the ongoing quest to thwart cybercriminals.
Seeing such systems in action is akin to watching a thrilling heist movie—only this time, the cybersecurity team is ahead of the game, neutralizing the culprits before they strike. A robust IDPS isn’t just part of the defense; it’s an integral part of business continuity and success.
Strategies for Maximizing IDPS Potential
To harness the full potential of an intrusion detection and prevention system, organizations must focus on continual learning, adaptation to emerging threats, and seamless integration into existing cybersecurity frameworks. Regular updates and active monitoring are crucial in ensuring the system provides optimal protection. Engaging staff through ongoing training ensures everyone is aware, proactive, and informed about cybersecurity best practices, creating a unified front against potential threats.
Navigating the complexities of cybersecurity can feel like treading a labyrinthine maze of digital threats. Yet, equipped with a well-deployed IDPS, businesses can chart a course toward safety, prosperity, and digital peace of mind.