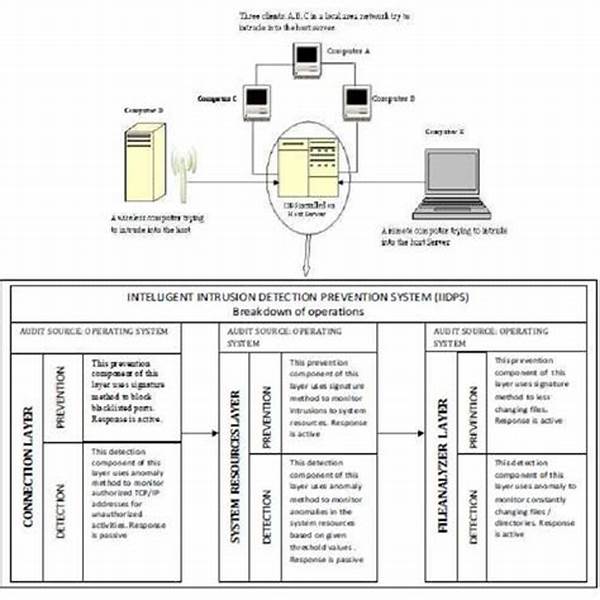
Intelligent Intrusion Prevention Techniques
In a world where digital landscapes are constantly expanding, the need for robust security solutions is no longer a luxury but a necessity. Enter intelligent intrusion prevention techniques, the unsung heroes that shield us from digital chaos. Imagine, if you will, a bustling internet world where cyber intruders lurk behind every virtual corner. These digital villains are not your ordinary neighborhood pranksters; they are sophisticated, armed with ever-evolving tactics and algorithms. Hence, the cricket orchestra of firewalls and antivirus software isn’t enough anymore. What we need is an ensemble of intelligent intrusion prevention techniques.
Picture this: You’re sipping your morning coffee, catching up on emails, when you unknowingly click on a malicious link. Suddenly, your personal data is at risk. This isn’t just a plot twist in a cybersecurity thriller; it’s a reality for millions. Intelligent intrusion prevention techniques are designed to prevent such calamities by identifying, analyzing, and neutralizing threats even before they reach your doorstep. With artificial intelligence at its core, these techniques anticipate threats, learning from past patterns to safeguard your digital fortress effectively.
But why stop there? It’s not just about the unseen heroes; it’s about understanding how these guardians operate. These intelligent solutions are akin to seasoned detectives, employing a combination of anomaly detection, behavior analysis, and threat intelligence to identify suspicious activities. The moment an anomaly is detected, these systems spring into action, blocking potential breaches with precision and agility. This isn’t just technology; it’s digital wizardry, ensuring your peace of mind.
Now, you might wonder, how can you benefit from these intelligent intrusion prevention techniques? Well, imagine a service that offers not just protection but peace of mind. Subscription services provide round-the-clock monitoring, ensuring that threats are neutralized before you even realize they exist. By investing in these techniques, you secure not only your data but also your reputation and financial well-being. It’s a small price to pay for a fortress guarding your digital existence.
How Intelligent Intrusion Prevention Works—Introduction to Intelligent Intrusion Prevention Techniques
Welcome to the digital age, where data flows seamlessly, connecting nations and industries in a web of information. However, this convenience comes with risks. Cyber threats are on the rise, becoming more sophisticated with each passing day. If you’ve ever found yourself frantically trying to recover stolen data, you understand the importance of intelligent intrusion prevention techniques. This isn’t just a buzzword—it’s a lifeline, a beacon of hope amid the storm of digital threats.
Imagine unlocking the potential of your business without the constant fear of cyber intrusions. How do you achieve this? Through intelligent intrusion prevention techniques, of course! These techniques equip your business to anticipate and neutralize threats efficiently. Think of them as your digital bodyguards, always alert and ready to shield your assets. Unlike traditional methods, these techniques alleviate the pressure of potential threats, allowing you to focus on what truly matters: innovation and growth.
We all love stories, and the world of cybersecurity is no different. Picture a business thriving in the digital marketplace, thanks to intelligent intrusion prevention techniques. These unsung heroes diligently keep watch, ensuring that malware doesn’t crash the party. The result? A thriving ecosystem where stakeholders and consumers interact without fear. That’s the power of intelligent intrusion prevention, a story where safety meets opportunity.
In the battle against cyber threats, knowledge is your most potent weapon. Understanding intelligent intrusion prevention techniques means recognizing patterns, analyzing behavior, and adapting to evolving threats. It’s not just about technology; it’s about empowering users. Once you’re armed with this knowledge, you can make informed decisions, safeguarding your digital footprint with confidence. Intelligent intrusion prevention isn’t just a necessity; it’s a game-changer in the digital landscape.
The Benefits of Integrated Security Solutions—Seven Actionable Intelligent Intrusion Prevention Techniques
—Detailed Overview of Intelligent Intrusion Prevention Techniques
The digital domain is vast and filled with both opportunities and threats. As we navigate this space, protecting our data and infrastructure is paramount. That’s where intelligent intrusion prevention techniques come in. These evolved methods use cutting-edge technologies, combining artificial intelligence and machine learning, to anticipate and thwart cyber adversaries. It’s like having Sherlock Holmes in your server room, deducing and acting on potential threats before they strike.
Now, you might be asking, “How does this work in practice?” The essence of intelligent intrusion prevention lies in its ability to analyze patterns. Machine learning algorithms scrutinize network behavior, identifying deviations from the norm. These systems learn from every interaction, becoming more astute and refined in their threat detection. This dynamic learning curve ensures that no two intrusions are handled the same way, making defenses impregnable and constantly adapting.
But it doesn’t stop at detection. Intelligent intrusion prevention techniques also include automated response protocols. Imagine a system that doesn’t just raise an alarm but actively engages potential threats. Once suspicious activity is identified, these systems take swift action, either by isolating the threat or neutralizing it altogether. It’s a proactive approach, ensuring minimal disruption to daily operations while maintaining optimal security.
Furthermore, these techniques offer the advantage of seamless integration. They can work in tandem with existing security apparatus, complementing traditional methods while enhancing overall efficacy. Be it firewalls or antivirus software, intelligent intrusion prevention can enhance them, turning them into formidable bastions of security. This synergy ensures that your digital environment remains unbreachable, providing peace of mind to organizations and individuals alike.
Adapting to a Dynamic Cyber Threat Landscape—Eight Tips for Implementing Intelligent Intrusion Prevention Techniques
—Concluding Thoughts on Intelligent Intrusion Prevention
Imagine a world where cyber threats are not a looming threat but a manageable entity. Intelligent intrusion prevention techniques transform this vision into reality. Their primary offering isn’t just security; it’s peace of mind. With these techniques, you can focus on innovation without the constant dread of cyber intrusions. Therefore, embracing these techniques isn’t just a smart choice—it’s an essential step in today’s interconnected world.
The beauty of these methods lies in their adaptability. By harnessing the power of artificial intelligence and machine learning, intelligent intrusion prevention techniques offer a robust framework that evolves with threats. As a result, businesses can stay one step ahead, transforming potential adversities into opportunities for growth and advancement.
In conclusion, the digital world need not be a landscape of uncertainties. By leveraging intelligent intrusion prevention techniques, you empower yourself with the tools needed for resilience and success. This isn’t just a defense mechanism; it’s a strategic advantage. With each passing day, as cyber threats continue to evolve, the importance of intelligent, proactive measures becomes even more crucial.
Through awareness, training, and implementation of these intelligent techniques, cybersecurity isn’t just an aspect of digital operation—it becomes the bedrock of sustainable development. So, whether you’re an industry leader or a digital novice, consider the profound impact of embracing these techniques. Your digital future depends on it.