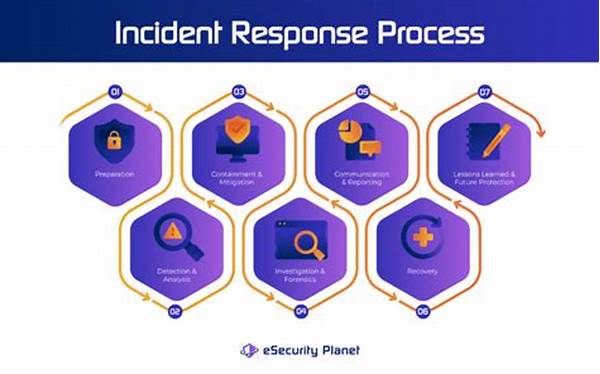
In the fast-evolving world of cybersecurity, incident detection and prevention strategies have become crucial components for any organization seeking to safeguard its digital assets. At the heart of these strategies is the need to not only identify threats as they occur but also predict and prevent potential breaches before they happen. The stakes are high; with more at risk than mere data, reputational and financial damages can cascade into long-term harms for businesses. Let’s delve into a world where incident detection is as thrilling as a detective novel and prevention strategies are your organization’s superhero, swooping in just in time.
The first step in building formidable incident detection and prevention strategies is understanding the landscape. Cyber threats are as varied as the villains in a comic book, each with its unique modus operandi. From phishing attempts masquerading as legitimate emails to sophisticated ransomware attacks locking down entire systems, the nature of potential threats is limitless. Organizations must remain on high alert, employing advanced threat intelligence and employing cutting-edge technology such as Artificial Intelligence and Machine Learning to effectively discern between benign activities and genuine threats. But, like any good detective, understanding the criminal is only half the battle; one must also be prepared with strategies to prevent crimes from occurring in the first place.
Let’s make it clear: incident detection and prevention strategies are not just for the big leagues. Whether you’re managing a startup or steering a multinational corporation, these strategies are your community’s unsung heroes. Employing regular security audits, for instance, can unveil vulnerabilities that might have gone unnoticed. Meanwhile, employee training sessions can transform your workforce into vigilant sentinels, aware and ready to challenge suspicious activity before it spirals into an incident. In this way, every staff member becomes an integral part of the organization’s protective net, helping prevent incidents simply by being informed and cautious.
Crafting an Effective Approach
A story shared by one of our clients truly encapsulates the value of proactive strategies. This customer, a mid-sized tech firm, had initially fallen victim to a CEO fraud scheme. The perpetrator masqueraded as the company’s CEO and managed to coax valuable information out of an unsuspecting employee. This could have been the end, but instead, it was a catalyst for change. After implementing tangible changes such as updated cybersecurity protocols, regular simulation exercises, and strengthened two-factor verification systems, not only did they regain their footing, but they thrived, emerging as advocates of robust incident detection and prevention strategies with many even referring to them as the standard-bearers of enterprise security.
The Purpose and Vision Behind Incident Detection and Prevention
Understanding the purpose behind the development of incident detection and prevention strategies is fundamental for any organization. The core aim is to protect data integrity, confidentiality, and availability from external and internal threats. It’s about giving organizations the confidence to operate in an increasingly complex digital landscape without fear. It’s about prevention, ensuring that potential breaches are stopped in their tracks before they can wreak havoc.
The implementation of comprehensive detection strategies hinges on layered security. Think of it as an elaborate security system in a museum that protects precious artworks. Each layer serves a different purpose; firewalls can block unauthorized access, intrusion detection systems monitor suspicious activities, and endpoint protection guards individual devices. These layers work in unison to provide a blanket of protection, ensuring comprehensive coverage from all angles.
Education and Awareness
Another crucial element of incident detection and prevention strategies is ongoing education and awareness. Cyber threats are continuously evolving, and so too must the knowledge and skills of your team. Regular training sessions and workshops can keep employees abreast of the latest threats, ensuring that they can recognize and respond to potential dangers effectively. This ongoing education builds a culture of security throughout the organization, reinforcing the idea that everyone has a role to play in keeping data safe.
Tools and Technology
The technology employed in incident detection and prevention strategies must be both cutting-edge and meticulously maintained. This means investing in robust security tools that offer real-time monitoring, threat intelligence, and automated response capabilities. The goal is to create a seamless and adaptive security posture that can rapidly detect and respond to incidents without causing undue disruption to the business’s daily operations.
As organizations continue to operate in an environment characterized by multiplying cyber threats, the importance of incident detection and prevention strategies cannot be overstated. Not only do they protect valuable digital assets, but they also enable organizations to maintain their reputation and operate with confidence in the digital age. As the saying goes, “An ounce of prevention is worth a pound of cure,” and in the realm of cybersecurity, this couldn’t be more accurate.
Examples of Incident Detection and Prevention Strategies
Discussion on Strategies
Diving deeper into the realm of incident detection and prevention strategies, it’s evident that these approaches are not a one-size-fits-all. Each organization must tailor its strategies to its unique needs and environment. This might involve a fundamental rethinking of current processes or enhancing existing ones with new technologies and methodologies. A few key elements should always be a priority: ongoing updates, regular training, and comprehensive audits.
Adopting incident detection and prevention strategies is not merely about purchasing the latest security software or implementing multi-layered firewalls. It’s about embedding a culture of security within the organization. Employees at every level must understand the significance of their role in maintaining security and be encouraged to voice concerns or report suspicious behavior. This cultural shift not only bolsters security architectures but also fosters an environment where staff feel valued and involved, leading to heightened morale and productivity.
Moreover, it’s crucial to recognize that these strategies must evolve. As cybersecurity threats become more sophisticated, so too must our means of combatting them. Regular reviews and updates to security protocols and techniques will ensure that an organization remains resilient against threats both known and unknown. Keeping incident detection and prevention strategies dynamic and responsive is the ultimate way to safeguard against the unpredictable landscape of cybersecurity.
The Significance of Ongoing Evaluation
As we continue to explore incident detection and prevention strategies, a central thesis emerges: continuous re-evaluation is crucial. Stagnation is the enemy of security. Every strategy implemented must be dynamic and adaptable to the ever-changing threat environment. Regular simulations, penetration testing, and feedback loops can help organizations identify gaps in their current defenses and make necessary adjustments.
Real-life stories from businesses that have successfully navigated cybersecurity landscapes highlight the effectiveness of incident detection and prevention strategies when they are agile. For example, a tech startup in San Francisco diverted a potential data breach simply because they had a routine check-up scheduled. During this check-up, they discovered anomalies that were swiftly addressed, showcasing the essence of an agile approach to cybersecurity.
An Organization’s Best Investment
Lastly, incident detection and prevention strategies should not be seen merely as a cost, but rather as an investment into the future of the organization. In today’s digital-first world, the payoff for having robust cybersecurity can be immense. It protects not only the organization’s data but also its reputation and customer trust.
The road to establishing effective incident detection and prevention strategies can seem daunting, especially for smaller businesses with limited resources. However, starting small—perhaps with employee training and basic endpoint security—and gradually scaling up can yield substantial dividends over time. Cybersecurity does not have to be an obstacle; instead, it can be an enabler, empowering businesses to achieve more without fear.
Benefits and Psychological Assurance
The flow-on effects of this investment extend beyond the operational. They foster peace of mind among employees and clients, knowing that their data is handled with care and expertise. The psychological reassurance alone is worth its weight in gold—a protected organization is an empowered organization, ready to thrive and innovate in its field without hesitations.
By adhering to these principles, organizations can stand tall against cyber threats, ensuring their security is as strong as it is agile. Leveraging incident detection and prevention strategies effectively will assure sustainable security for any enterprise in the modern digital age.