In today’s fast-paced digital era, where cyber threats loom larger than ever, implementing effective threat intelligence strategies is vital. Imagine a world where security breaches are a thing of the past, and your organization navigates cyberspace with confidence. Picture walking into the office every morning knowing that your threat intelligence system is working round the clock, identifying and neutralizing risks before they even enter your purview. It’s like having your very own cyber superhero, guarding the gates of your digital world.
Many organizations struggle to keep up with the ever-evolving landscape of cyber threats. Countless headlines scream tales of data breaches and ransomware, leaving businesses in a state of perpetual worry. This is where the power of implementing effective threat intelligence strategies comes into play. By leveraging these strategies, you arm your organization with the tools and insights needed to detect threats ahead of time, understand the motives of cyber adversaries, and safeguard your most valuable assets.
Yet, diving into the realm of threat intelligence can seem daunting. But fear not! Implementing effective threat intelligence strategies doesn’t require you to be a tech wizard. With the right guidance and support, it’s as easy as ordering pizza online—minus the cheesy crust. So, as you sip your cup of coffee and settle into your workday, remember that the journey to enhanced cyber security begins with a single step: developing a robust threat intelligence strategy that aligns with your business needs.
Why Threat Intelligence Matters More Than Ever
The modern digital landscape is not what it was a decade ago. With increasingly sophisticated cyber attacks, organizations face potential risks daily. Cybercriminals are no longer just lone hackers; they are organized, smart, and equipped with formidable resources. Thus, implementing effective threat intelligence strategies isn’t just a luxury—it’s a necessity for survival.
The Art of Crafting Your Threat Intelligence Plan
So you’ve decided to dive into the world of implementing effective threat intelligence strategies—great! But where to begin? Crafting an effective plan starts with understanding your organization’s unique needs and vulnerabilities. It’s similar to tailoring a suit; it needs to fit perfectly to serve its purpose.
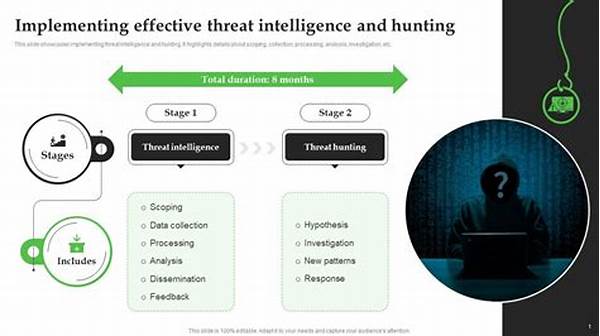
Breaking down the process into digestible steps, organizations can begin by defining their strategic goals. Identifying potential threats and vulnerabilities is crucial. Then, collecting and analyzing data becomes the backbone of this strategy. The key is continuous monitoring and reassessment, adapting the strategy as the threat landscape shifts.
Topics Related to Implementing Effective Threat Intelligence Strategies
In the bustling realm of cyber security, staying one step ahead is not merely a tactic—it’s a survival mechanism. And implementing effective threat intelligence strategies is the key. Think of it as equipping your digital fortress with an ever-watchful guardian angel, one that never sleeps. This guardian analyzes every byte and packet, alerting you at the first sign of danger, painting a proactive picture of security.
Through implementing effective threat intelligence strategies, organizations are empowered to not only secure their data but also to build trust with stakeholders by showcasing a robust security posture. It’s time to move beyond reactive measures and embrace the proactive approach that effective threat intelligence provides. If you’re quizzical, just ponder—who wouldn’t want a digital immune system that’s both vigilant and adept, ensuring your organization’s long-term success?
What Does It Take to Implement an Effective Threat Intelligence Strategy?
The journey of integrating effective threat intelligence strategies is akin to assembling a jigsaw puzzle. You begin with the frame, outlining the priorities and goals of your security blueprint. Let existing resources guide you, as they’re often the missing pieces you haven’t yet recognized. Engage stakeholders, foster collaboration, and ultimately curate a strategy that’s uniquely yours.
Elements of Successful Threat Intelligence Integration
Within the heart of implementing effective threat intelligence strategies lies data—raw, unfiltered, and vital. Gathering this intelligence requires a meticulous approach, using state-of-the-art tools that facilitate real-time analysis and prioritization of threat data. This isn’t just about adding pieces to the puzzle. It’s about crafting a cohesive picture, continually evolving as threats morph and grow more complex.
For organizations to remain ahead, adaptability becomes the touchstone of survival. Implementing effective threat intelligence strategies requires an ongoing commitment to learning and improvement, employing technology as both sword and shield. Any successful implementation is deeply rooted in a well-orchestrated symphony of human expertise and technological prowess, designed to anticipate, adapt, and respond effectively to the shifting cyber threat landscape.
Illustrating Threat Intelligence Strategies
Behind every successful cyber defense stands an intricately designed defense strategy—one that mitigates risks and protects digital assets. Implementing effective threat intelligence strategies is your way of staying one step ahead. Investing time and resources into these strategies today ensures a fortified tomorrow, providing peace of mind that is priceless in today’s digital age.
Navigating this ever-evolving labyrinth of threats may first appear daunting, but with the right direction and plan laid out, rest assured you’re on the course to safeguarding not just your business but fostering trust among your clientele. Are you ready to embark on this journey of resilience and fortification? Let’s step into a world where your digital integrity remains uncompromised—one effective threat intelligence strategy at a time.