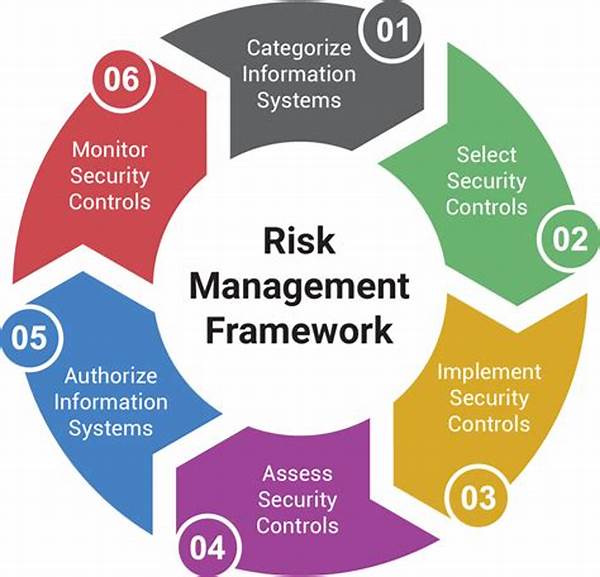
In an era where digital transformation is revolutionizing industries at an unprecedented speed, the significance of implementing continuous security risk management is taking center stage. As businesses increasingly rely on digital infrastructures, the landscape of security threats is evolving with equal vigor. From sophisticated cyber-attacks to subtle data breaches, the challenges are becoming more formidable, demanding an adaptable and continuous approach to security. Implementing continuous security risk management is not just about setting up barriers but also about pro-active, round-the-clock vigilance that ensures threats are identified and neutralized before they can cause havoc.
Enterprises today are no longer operating in a silo; they are part of a global network constantly exchanging information. This interconnectivity, while advantageous in driving business growth, also opens doors to numerous vulnerabilities. Consequently, adopting a continuous risk management methodology becomes imperative. But fear not, dear readers, because this concept isn’t as daunting as it sounds. Picture it like a superhero with a keen sense of foresight, ready to combat any villainous cyber miscreant that dares to hurdle across the firewall. By recognizing and preparing for potential risks before they strike, businesses can save millions in potential losses and reinforce the trust of their clients.
In fact, organizations with a robust continuous security risk management system in place find themselves at an advantage. They are agile, responsive, and maintain business operations without major interruptions. The approach goes beyond preventing threats; it’s a comprehensive strategy that encompasses threat detection, response, and recovery. This dynamic defense mechanism is becoming the must-have armor for digital enterprises.
The Core Benefits of Continuous Security Risk Management
Implementing continuous security risk management isn’t just a trend; it’s becoming a blueprint for operational excellence. Companies that invest in it often find themselves lauded for their proactive stances towards safeguarding data integrity and client confidentiality. In today’s volatile market, possessing such a robust system can act as a differentiator, providing an exclusive edge over competitors.
—
Purpose of Implementing Continuous Security Risk Management
A Strategic Move Towards Enhanced Security
The purpose of implementing continuous security risk management is multi-faceted. At its core, it aims to equip organizations with the tools needed to anticipate, identify, and mitigate potential risks in real-time. This system acts as a guardian angel in the cyber realm, ensuring that your digital ecosystem remains untainted by external disruptions.
First and foremost, implementing continuous security risk management is about being preemptive. Businesses are no longer waiting for a cyber threat to occur; they are preparing in advance to thwart it. This forward-thinking approach maintains not only operational flow but also boosts customer confidence. It’s the modern-day insurance policy, ensuring that a company’s most valuable assets are shielded from unforeseen calamities.
The Evolution of Risk Management Practices
Traditionally, risk management involved periodic reviews and assessments. However, the landscape has drastically shifted with the emergence of continuous security strategies. The earlier method was akin to looking in the rear-view mirror, whereas continuous security risk management is like having a 360-degree radar, offering real-time surveillance. This transformative approach ensures that nothing flies under the radar, much like a diligent watchdog patrolling the digital premises.
Engaging in continuous security risk management means investing in peace of mind. This methodology stands at the intersection of technology and innovation, harnessing advanced tools such as artificial intelligence and machine learning to predict and combat potential cyber threats. It’s the digital shield that modern-day businesses didn’t know they needed but can’t operate without.
Long-term Benefits of Continuous Implementation
Over time, the sustained practice of implementing continuous security risk management renders undeniable long-term benefits. For starters, it optimizes resource allocation by reducing the necessity for emergency fixes. Companies can redirect their focus and finances towards growth strategies as opposed to damage control.
Moreover, a strategically enforced continuous security framework aligns with regulatory compliances and standards, thus mitigating risks of legal repercussions. This compliance not only safeguards finances but also enhances brand reputation in such a way that clients and stakeholders view the organization as a trusted partner.
The Ripple Effect of Continuous Security
When companies commit to implementing continuous security risk management, the positive effects ripple through their entire operation. Employees work with heightened assurance, stakeholders feel secure in their investments, and clients receive consistent, uncompromised service. It’s a comprehensive win-win situation, amplifying the company’s growth trajectory and fortifying its market position.
The dynamic digital ecosystem requires a dynamic solution, and that’s precisely what continuous security risk management offers. It’s not just a service; it’s an evolution in the way we perceive and handle security threats, transforming businesses into resilient digital fortresses, robust against even the most formidable cyber adversaries.
—
Key Aspects of Continuous Security Risk Management
Unbreakable Bonds: Security and Trust
Implementing continuous security risk management is more than a necessity; it’s a commitment to maintaining unbreakable bonds of security and trust. This approach ensures that as businesses climb the technological ladder, they are safeguarded against potential falls. By making security an ongoing priority, companies can focus on innovation and delivering exceptional value to their consumers.
—
Implementing Continuous Security Risk Management: A Deep Dive
The Significance of a Continuous Approach
In the bustling world of business, implementing continuous security risk management is like having an ever-vigilant lifeguard stationed at the pool of your company’s data. Modern enterprises operate in an environment where the stakes are high, and data breaches can lead to catastrophic losses. Hence, a continuous approach to security isn’t merely important; it’s indispensable. We’ve moved beyond reactive measures to a more nuanced, proactive stance.
Proactivity as a Defense Strategy
Continuous security risk management isn’t just a barrier against external threats; it functions as your company’s own immune system. By remaining vigilant, identifying potential threats, and neutralizing them before they become issues, your organization is always a step ahead. Imagine a futuristic shield surrounding your data, defending against every malware and cyber-attack attempting to penetrate. Now that’s a comforting thought, isn’t it?
Embedding security deeply into the culture of your organization fosters a proactive mindset. Such a culture encourages employees to be more conscious of security and nurtures an atmosphere where vigilance is part of the job description. Implementing continuous security risk management transforms every team member into a stakeholder in maintaining your company’s fortress.
The Art and Science of Risk Management
The art of implementing continuous security risk management lies in its seamless integration into everyday operations. It’s not a burdensome add-on but an enabler of business efficiency. By coupling intuitive risk assessment tools with cutting-edge technology, you can create a security apparatus that is as intelligent as it is invisible.
The science behind it involves utilizing artificial intelligence and machine learning. These technologies incessantly scan networks, delve into analytics, and provide insights into possible vulnerabilities faster than any human could. Your business’s heartbeat becomes less susceptible to irregular rhythms, thanks to this robust infrastructure.
Empowering Your Workforce
A crucial component of continuous security risk management is empowering your workforce. Training programs tailored to different roles ensure that everyone, from intern to CEO, is equipped to identify threats and respond appropriately. But let’s keep it light and engaging! A sprinkle of humor, interactive sessions, and gamified modules can transform this necessity into an enjoyable part of the company culture.
Building a Future-Ready Organization
By implementing continuous security risk management, you’re setting the stage for sustainable growth. Not only does this practice protect current assets, but it also enables your organization to adapt and thrive amid evolving technological landscapes. The foresight to invest in thorough security measures today could well be the differentiator that positions your enterprise as an industry leader tomorrow.
In conclusion, there’s no denying the integral role of continuous security in today’s digital landscape. It’s the silent guardian, the watchful protector, standing by to ensure a secure future. By making this strategic investment, you’re not just safeguarding your organization; you’re building a legacy of resilience and trust.
—
Essential Elements of Continuous Security Risk Management
A Comprehensive Strategy for Modern Challenges
In today’s world, implementing continuous security risk management is a strategic imperative, providing businesses the resilience needed to face modern challenges head-on, securing not just data, but the trust of clients, partners, and stakeholders alike. By adopting this approach, organizations are not only securing their assets but are also paving the way for sustained success and innovation.