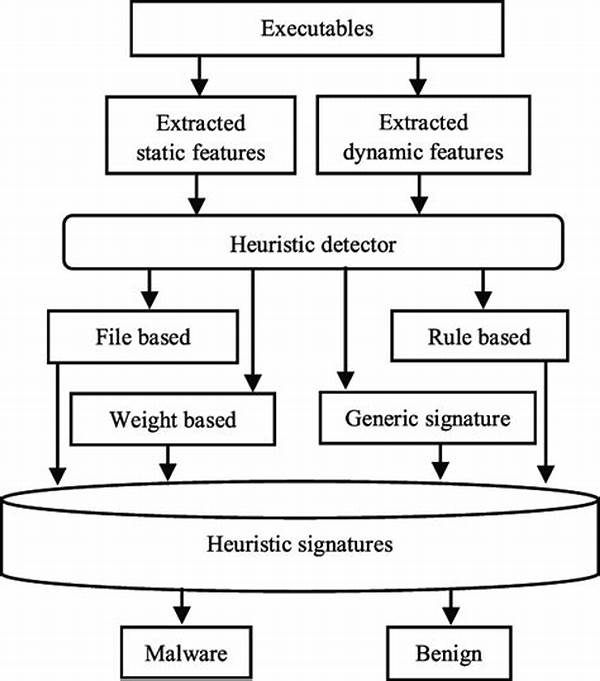
In an era dominated by technology, with a new application born every second, safeguarding our sensitive data is more crucial than ever. This is where heuristic-based malware detection techniques come into play. Imagine having a robust security blanket that evolves with threats and anticipates potential malicious activities, offering protection not just based on known vulnerabilities but by identifying unknown threats as well. Heuristic-based methods are your trusty digital detectives, examining software behavior in real-time to flag suspicious activity. While traditional anti-virus solutions rely on signature databases to catch known malware, heuristic techniques dive deeper, hunting for suspicious patterns and behaviors to unveil novel malware strains.
The beauty of heuristic-based malware detection techniques lies in their proactive nature. They don’t wait for an update to recognize new malware forms; they analyze the behavior and characteristics of files and applications to detect potential threats. It’s like having a sixth sense in the digital world. And while no system is infallible, these techniques hold a distinct edge over traditional methods by offering a dynamic approach to cybersecurity. Integrating heuristic detection tools into your cybersecurity plan might just be the winning formula against cyber threats.
In recent years, as cyber nuances continue to evolve, heuristic-based malware detection techniques have proven to be indispensable. Robust experimentation has shown they perform significantly well in zero-day threat scenarios. But what’s really captivating about these systems is their capability to learn. By adapting to the changing threat landscapes, heuristic techniques gain sophistication, identifying evolving malicious patterns far quicker than signature-based rollouts. As threats grow more complex, will your cybersecurity defenses rise to the occasion? This could be the secret ingredient you’ve been seeking in your digital safety recipe.
Employing these methods can be your digital fortress, especially in a world where approximately 350,000 new malware files are detected daily. This staggering statistic emphasizes the urgent need to keep up-to-date with innovative detection techniques. As users, we are often woefully unaware of potential threats lurking in our daily digital interactions. The adoption of heuristic-based malware detection techniques can bring peace of mind, providing a reliable first line of defense against unseen potential cyber-attacks. Choose to stay ahead in the cybersecurity game — embrace the inevitability of digital evolution today.
Understanding the Mechanism of Heuristic Malwares
Diving deeper into the realm of cybersecurity, heuristic-based malware detection techniques stand tall as stalwarts of digital protection. Their operation revolves around creating an environment where potential threats can be neutralized before taking root. Utilizing algorithms designed to evaluate software behavior, these techniques go beyond the mere scanning of code for matches with known threats, offering a dynamic and evolving line of defense.
—
Heuristic-Based Malware Detection Techniques: A New Age of Cybersecurity
When it comes to cybersecurity, the term “heuristic-based malware detection techniques” may sound complex, but the concept behind it is remarkably intuitive. Imagine having an intelligent surveillance guard that not only looks out for intruders based on past encounters but is smart enough to spot new types of suspicious behavior. These techniques are specially formulated to handle the ever-increasing volume of malware, which traditional signature-based methods might overlook.
Heuristic-based techniques evaluate the actions of programs rather than just their signatures or lists of known threats. This method of protection catches potential threats based on the behavior and properties seen in new malware types. For instance, if a new program suddenly starts encrypting files without permission or sends a boatload of requests to unknown servers, a heuristic-based system will spring into action, flagging it as a possible malware. This adaptability makes it a formidable tool in the fight against cybercrime.
Drawing the Line Between Heuristics and Traditional Methods
How do heuristic-based malware detection techniques compare to more traditional forms of malware detection? The answer lies in adaptability. While traditional methods employ databases of known threats—sort of like a most-wanted list of cyber villains—heuristic techniques evaluate the behavior of software, uncovering new threats by studying their activities. This proactive approach means that heuristic-based methods can tackle zero-day threats which have not yet been categorized or listed in databases.
In today’s digital age, relying solely on past data isn’t an option. Cyber threats are continuously evolving, reminiscent of a game of cat-and-mouse. At one moment, you might think you’ve outsmarted cybercriminals by updating your antivirus software, only to find that a new threat has emerged just as your guard is down. This is precisely where the strength of heuristic-based malware detection techniques shines. It adapts, learns, and counters new threats in real time.
If you’re wondering how heuristic-based malware detection techniques perform this seemingly magical feat, the answer lies in their design. By examining the context and behavior of programs, these methods are better prepared to identify the more subtle signs of intrusion. This dynamic analysis allows for detection of advanced persistent threats and malicious codes that might slip through conventional detection methods. By integrating heuristic evaluations, users can bolster their cyber defenses significantly.
Join fellow tech enthusiasts and digital safety advocates in embracing these cutting-edge techniques and prepare to navigate this technological landscape more confidently. By harnessing the transformative power of heuristic-based malware detection techniques, you can ensure your digital world remains secure, robust, and ready to face the cybersecurity challenges that lie ahead.
—
Tags Related to Heuristic-Based Malware Detection Techniques
Discover a new wave of cybersecurity with heuristic-based malware detection techniques. Designed to be agile and adaptive, these methods redefine what it means to protect data in an ever-evolving digital landscape. Traditional methods often fall short when facing zero-day threats, but heuristic-based methods excel by detecting unknown threats through behavior analysis. If you’re passionate about remaining one step ahead of cyber threats and ensuring peace of mind in a tumultuous digital environment, exploring these advanced detection techniques is well worth your time. Join the ranks of proactive internet users safeguarding their data like never before!
—
Navigating the Future of Cybersecurity with Heuristic Techniques
In the ever-expanding realm of cyberspace, adopting innovative approaches to safeguard information has become imperative. Among the most discussed of these is the heuristic-based malware detection techniques. This modern approach redefines the cybersecurity landscape by focusing on behaviors rather than just known data signatures. To delve deeper into these mechanisms, it’s essential to explore their core functionality.
Heuristic techniques operate using algorithms that mimic the problem-solving abilities of a human being. Instead of relying solely on pre-existing patterns, they are designed to make educated guesses about the potential of a new program being malicious. This is akin to a seasoned detective using intuition and experience to solve a crime before it occurs. For businesses and individuals alike, adopting these sophisticated methods translates to an extra layer of cybersecurity that is not only efficient but also proactive.
What’s exceptionally intriguing about heuristic-based malware detection techniques is their capability to uncover lurking threats that traditional methods might miss. This dynamic forward-thinking approach is a game-changer, especially in cases pertinent to unknown malware, which has yet to be classified by traditional methods. Therefore, as cyber threats become more sophisticated, the tools needed to combat them must evolve as well.
The benefits of employing these heuristic techniques stand out starkly when examining cybersecurity reports. Companies and individual users who’ve adopted them often discover malware in their systems at an unprecedented rate, long before potential damage is done. This means that rather than dealing with theft or data loss after it happens, potential crises are mitigated ahead of time, saving significant resources in crisis management.
Embrace this digital revolution with open arms and consider incorporating heuristic-based measures into your cybersecurity arsenal. They’re like having a cybersecurity analyst constantly monitoring your systems, reducing false positives and increasing threat detection rates.
Understanding these sophisticated techniques is similar to catching a glimpse of the future of cybersecurity; they represent hours of research and development dedicated to one cause — securing the digital landscapes that define our modern lives.
Future of Heuristic Techniques in Cybersecurity
As the digital scene transforms, heuristic-based malware detection techniques continue to spearhead advancements in cybersecurity innovation. These tenacious approaches to threat detection are designed to react swiftly to digital anomalies, leading the way for even more intelligent systems in the future.
Deploying Heuristic-Based Malware Detection Techniques
In today’s digital world, protecting sensitive data is at the top of every organization’s priority list. Therefore, companies need cutting-edge methods that can outpace potential cyber threats, and heuristic-based malware detection techniques offer just that. The techniques use advanced algorithms to identify potential threats in real-time. Unlike traditional signature-based detection that relies on existing malware databases, heuristic detection identifies new threats by evaluating the behavior and characteristics of malware.
What’s impressive about heuristic detection is its ability to adapt and learn over time. As cyber threats become more advanced, heuristic methods evolve to counter these threats more effectively than ever before. Thanks to artificial intelligence’s rising influence, heuristic techniques continue to carve out a transformative path in cybersecurity. They provide a powerful, proactive shield against malware unlike any other.
With approximately 230,000 new malware samples produced daily, businesses cannot afford to rely on outdated methods. Heuristic-based malware detection techniques provide a much-needed solution, evolving alongside rising threats in a way that signature-based approaches simply cannot. By detecting threats before traditional methods, companies can better protect themselves from data breaches and other cyber intrusions. Heuristic detection’s adaptability makes it a crucial part of modern-day cybersecurity strategies.
Employing these techniques can lead to reduced false positives, maximized efficiency, and a more robust defense strategy against cyber threats. As technology advances, so too will the sophistication of these heuristics, ensuring continued relevance and effectiveness. By embracing heuristic methods, organizations can future-proof their cybersecurity defenses and maintain peace of mind in an ever-shifting digital landscape.