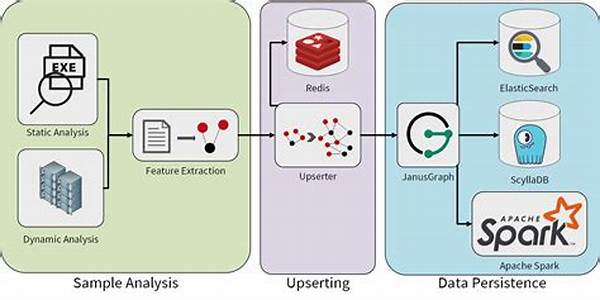
Feature Extraction in Malware Analysis
In the ever-evolving world of cybersecurity, the battle between malicious developers and security experts is relentless. The stakes are high as billions of dollars and the personal data of countless individuals hang in the balance. One of the key strategies to gain the upper hand in this digital duel is feature extraction in malware analysis. Imagine walking through a maze filled with hidden traps—malware investigators must decipher the paths and identify telltale signs of harmful software before it wreaks havoc. So, what if I told you there’s a way to have an edge in understanding malware behaviors convincingly and effectively?
Feature extraction in malware analysis offers this advantage by diving deeper into the essence of malware, mapping out signatures, and predictors that expose potential threats. If you are fascinated by cybersecurity’s cat-and-mouse game, picture morphing into a detective using advanced tech to reveal a culprit’s secrets before a crime even unfolds.
The opportunities that await within feature extraction are like having an X-ray vision into malware anatomy. As businesses become increasingly vulnerable to cyber threats, this technique stands out, providing a crucial service, not just for big firms but for those passionate about maintaining a safe digital environment.
Investing in understanding and mastering feature extraction in malware analysis can propel you to the forefront of cybersecurity. You get the superhero ability to foresee and forestall threats, maintaining peace in the virtual space.
The Practical Side of Feature Extraction
Practicality defines feature extraction’s essence. It’s not just about understanding, but application. If securing data sparks your interest, taking actionable steps like engaging with cybersecurity experts or using tools specializing in feature extraction can be a game-changer. The success stories flourishing in this field speak volumes—professionals reclaiming their agency, ultimately protecting invaluable digital assets.
—
Understanding Feature Extraction in Malware Analysis
Feature extraction in malware analysis is an essential component in the cybersecurity toolkit. By isolating specific characteristics from malware samples, security experts and systems can predict and identify potential cyber threats more precisely. This method strips down malicious software to its core elements, allowing analysts to make informed decisions and preemptively neutralize dangers.
In today’s tech-driven world, businesses are increasingly exposed to cyber threats, making the understanding of feature extraction in malware analysis more relevant. Not only does it ensure the integrity of sensitive information, but it also helps organizations maintain their reputations by keeping their defenses robust. Think of it as installing a state-of-the-art alarm system; you position yourself ahead while retaining market confidence.
Benefits of Feature Extraction in Cybersecurity
The benefits are as clear as a bright summer’s day. Harnessing the power of feature extraction in malware analysis, cybersecurity teams can proactively strengthen their defenses. It’s an unspoken promise to your clients and stakeholders—prioritizing safety without compromise. This approach meticulously searches for characteristics that might be overlooked, offering a higher degree of precision.
—
Key Elements of Feature Extraction in Malware Analysis
The field of malware analysis is intricate, yet engaging once you dive deep into what makes feature extraction so vital. As a curious explorer, understanding these elements will equip you with insights that may one day transform fear into empowerment.
When distinguishing risky entities online, analysts look for:
Malware analysts blend these facets into comprehensive profiles of potentially harmful software.
Real-World Applications of Feature Extraction
Consider real-world scenarios where analysis highlights unique behavioral flags that, when used proactively, stave off attacks. Cyber resilience gets constructed bit by bit, fragment by fragment, through the collected intelligence from feature extraction in malware analysis. As you navigate these cyber landscapes, remember that understanding these key elements elevates defenses and fortifies infrastructures.
—
Unraveling Malware Mysteries through Feature Extraction
Why Feature Extraction Matters
Cybersecurity is akin to archaeology; you sift through layers, looking for hidden clues. The journey from novice to expert involves honing the skill of feature extraction in malware analysis. Each cyber relic holds knowledge; it’s an art and a science to interpret and apply these discoveries to protect the digital realm.
With the demand for cybersecurity escalating, acquiring expertise in malware analysis is like having a magnet for opportunity, drawing those passionate about defending the digital frontlines. Engaging with this discipline promises a rewarding experience, shaping resilient protectors of the cyber world.
Crafting Tomorrow’s Security Experts
As more professionals master feature extraction techniques, the collaborative force creates an impregnable wall against potential threats. This foundation is built through distributed efforts, collective learning, and an ever-enthusiastic drive to excel in cybersecurity. Building your skillset becomes not just an investment in your career but a commitment to digital integrity.
Now imagine implementing what you’ve learned to create solutions and shield infrastructures—your story becomes a part of the cybersecurity legacy. Let your knowledge inspire others and contribute to an engaged, informed community. Your expertise in feature extraction in malware analysis represents more than a skill: it’s a safeguard for the digital future.
—
Essential Points on Feature Extraction in Malware Analysis
Understanding these facets fosters a comprehensive approach to securing digital domains from potential threats.
Collaboration and Continuous Learning
Staying updated and actively participating in cybersecurity communities elevates your game, ensuring you’re always one step ahead in the field of feature extraction in malware analysis.
Adapting to New Challenges
As time progresses, techniques evolve, reflecting the dynamic nature of both malware and cybersecurity solutions. Remaining adaptable is paramount in maintaining digital sanctuaries free from intrusions.