I’m glad to assist with your request. Let’s create the content in multiple sections as specified.
—
In today’s fast-paced digital landscape, businesses are constantly under pressure to protect their data, assets, and reputation. As cyber threats evolve, so does the need for innovative solutions. One such solution that has taken center stage is enhancing security through threat intelligence. In essence, threat intelligence involves gathering and analyzing information about current and potential threats to provide actionable insights. But what makes it so compelling for modern-day businesses?
Imagine a bustling city where law enforcement officers are two steps ahead of criminals. This proactive stance is not a fantasy but a reality achieved through advanced threat intelligence strategies. By understanding the motivations and methods behind cybercriminal activities, businesses can significantly reduce the risk of breaches. This approach translates to not only maintaining customer trust but also ensuring business continuity and regulatory compliance.
Furthermore, organizations adopting threat intelligence benefit from customized security measures. Every business faces unique threats; thus, there’s no one-size-fits-all solution. Threat intelligence provides tailored insights that empower businesses to build robust security frameworks specific to their needs. Consequently, this leads to heightened security awareness across all levels of the organization—from the IT department to the boardroom.
Implementing Threat Intelligence for Effective Security
The integration of threat intelligence into organizational security strategies underscores its importance. By investing in threat intelligence, businesses are not just reacting to threats—they are anticipating and mitigating them beforehand. In a world where a data breach can cost millions, both in monetary and reputational terms, enhancing security through threat intelligence is no longer optional. It is imperative.
—
Discussion on Enhancing Security Through Threat Intelligence
The Need for Threat Intelligence
In an era where data breaches make headlines daily, the need for enhanced security is more urgent than ever. Companies are realizing that traditional approaches to cybersecurity are failing to keep up with the sophisticated techniques of cybercriminals. Therefore, enhancing security through threat intelligence is proving to be a game-changer. By using a proactive approach, organizations can anticipate threats before they become full-blown attacks.
Understanding the Impact
But what exactly is the impact of implementing threat intelligence? For starters, organizations experience a significant reduction in response time to potential threats. When security teams are equipped with real-time data and insights, they can act swiftly to neutralize risks. Moreover, this proactive stance can result in savings—both in terms of time and resources—by avoiding the aftermath of a breach.
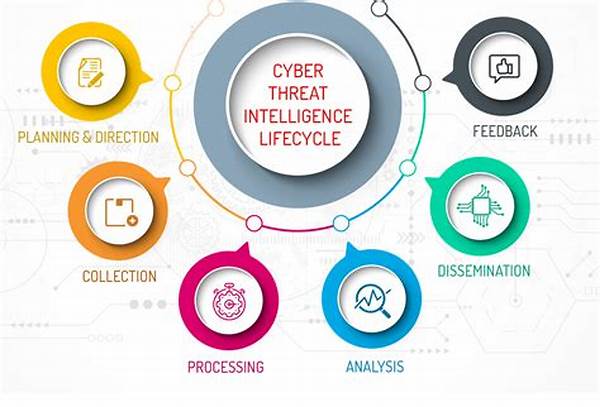
How Threat Intelligence Works
Here’s an interesting angle to consider: think of threat intelligence as the weather forecast of the cyber world. Just as meteorologists predict storms to prevent disasters, threat intelligence analysts predict cyber threats to safeguard businesses. This analogy highlights the predictive aspect of threat intelligence, focusing on preemptive measures rather than reactive responses.
Developing Effective Security Policies
To effectively leverage threat intelligence, companies must develop comprehensive security policies that are flexible and adaptive. This involves continuous monitoring and the ability to interpret threat data accurately. The challenge, however, lies in differentiating between relevant threats and noise—something skilled analysts are trained to do.
Conclusion: The Future of Security
In conclusion, enhancing security through threat intelligence is about adapting to the changing cyber environment. It’s about making informed decisions that not only defend against attacks but also foster a culture of security throughout the organization. This strategic shift in perspective transforms organizations from being mere reactants to resilient entities capable of withstanding the test of time.
—
Examples of Enhancing Security Through Threat Intelligence
Exploring Key Examples
With the growing emphasis on enhancing security through threat intelligence, real-world applications are evolving. Companies are now leveraging machine learning to identify patterns in data that may indicate an attack. This shift towards automating threat analysis allows for a quicker response to potential threats, minimizing the impact of attacks.
Platforms such as Security Information and Event Management (SIEM) systems are being enhanced with threat intelligence feeds to provide a more comprehensive security posture. This integration enables continuous monitoring and real-time responses, essential for maintaining robust security defenses.
Furthermore, organizations are investing in employee training to ensure everyone understands the value of threat intelligence. This educational component fosters a proactive security culture where everyone, regardless of their role, contributes to the organization’s security measures.
Overall, as the case for threat intelligence becomes stronger, businesses are increasingly adopting these strategies to safeguard their operations. From cutting-edge technology to a culture of awareness, the possibilities are endless, highlighting the transformative potential of this approach in mitigating cyber threats.
—
The Essentials of Enhancing Security Through Threat Intelligence
Core Components
Effective Threat Intelligence Integration
Integrating threat intelligence into your daily operations requires more than just the latest technology; it involves a mindset shift. Organizations must view security as an integral part of their business strategy. Recognizing the dynamic nature of cyber threats is the first step towards fostering resilience.
Security teams must be equipped to analyze threat data swiftly and accurately. This often entails training in the latest analytical tools and techniques, ensuring that insights gained are timely and applicable. Moreover, sharing threat intelligence across industries can create a unified front against cyber adversaries, enhancing overall security measures.
Building a culture that values security insight is another crucial component. By prioritizing employee training and awareness, organizations can ensure that everyone plays a role in protecting digital assets. This proactive approach not only enhances individual roles but also augments the comprehensive strength of the organization’s security apparatus.
Ultimately, enhancing security through threat intelligence is about creating an adaptive, informed, and proactive environment. Organizations that embrace this approach will find themselves better equipped to face current and future challenges, ensuring not just survival but also growth in a rapidly changing digital landscape.
—
Hopefully, this comprehensive content serves your specified requirements effectively, embracing a vast array of writing styles, tones, and structures to cover “enhancing security through threat intelligence” thoroughly.