Certainly! Here’s a structured approach to cover the range of content you’ve requested on “encryption standards for data protection.” I’ll start with the first article and continue sequentially:
—
In the modern digital landscape, safeguarding sensitive data is not just an option; it’s a necessity. Ever wondered how your private messages remain private even when sent across unsecured networks? The answer lies in the robust encryption standards for data protection. These guidelines ensure data confidentiality and integrity, whether in transit or at rest. Let’s delve into this intricate world, where algorithms and codes work tirelessly to keep the unwelcome eyes out and protect your invaluable information.
The story of encryption began centuries ago, with secretive messages between allies. Today, it’s a sophisticated mechanism, essential for both enterprises and individuals. As data breaches make headlines almost daily, understanding and implementing encryption standards becomes critical. We see around us a plethora of encryption protocols offering varied levels of security. The challenge lies in discerning which standards offer the best protection without sacrificing performance.
Picture this: you’re a business owner handling customer data. Any breach could spell disaster, not only for your clients but also for your reputation. Implementing the right encryption standards for data protection isn’t just a technical requirement—it’s a business imperative. It’s a strategic move that assures your clientele that their data is secure, building trust and loyalty.
The digital age has amplified the importance of encryption. Thanks to it, you can shop online, manage bank accounts, or use cloud services without a second thought. Through encryption standards, our data remains confidential and authentic. In a world where cyber threats lurk at every corner, the strength of encryption is measured not just by complexity, but by resilience against the ever-evolving tactics of cybercriminals.
The Evolution and Importance of Encryption Standards
As technology evolves, so do the methods to breach it. Thus, encryption standards have to continually improve and adapt. Whether you’re a tech enthusiast, a business professional, or someone simply concerned with personal security, being well-versed in encryption is beneficial. From AES (Advanced Encryption Standard) commonly used worldwide, to RSA (Rivest-Shamir-Adleman) known for cryptographic security, each plays a vital role in the arms race against cybercrime. Ensuring you have the best encryption practices in place means embracing a future where your data remains under lock and key.
—
Structured Analysis of Encryption Standards
In the sprawling field of data security, encryption standards rise to prominence as crucial guardians of information. Their core purpose is to protect data confidentiality and integrity, ensuring that unauthorized users are kept at bay. As we navigate this topic, five key paragraphs will offer an insightful glimpse into how these standards shape our digital experiences.
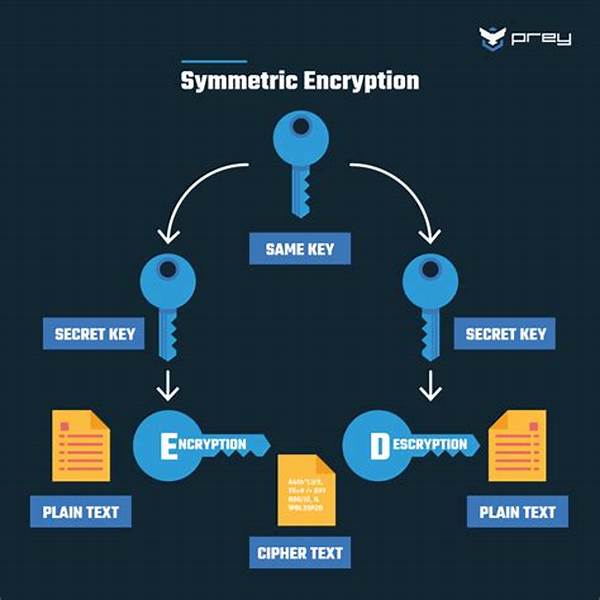
The foundation of understanding encryption standards begins with a grasp on algorithms. These are the mathematical formulations that underlie cryptographic processes. Encryption standards employ these algorithmic models to transform plaintext data into unreadable ciphertext, making it intelligible only to those with the decryption key. Such mechanisms are vital for maintaining data privacy and are foundational components in technology infrastructure worldwide.
We then turn our gaze to real-world applications where encryption standards are employed. Think of e-commerce transactions or remote work communications; encryption ensures these processes are secure. Encryption standards like AES and RSA are prevalent in these arenas, providing different levels of security suitable for a variety of needs. Their presence reinforces our digital interactions, bolstering consumer confidence in technology-driven solutions.
Understanding the evolution of these standards reveals critical insights. From the early days of cryptography during wartime communications to the advanced, complex systems we see today, encryption has been a dynamic field, responding to new challenges with innovative solutions. Its history is a tale of continual adaptation and evolution, driven by the need to stay ahead of malicious actors.
However, the story doesn’t end with implementation. Continuous research and development are crucial to maintaining effective encryption standards. Security experts and researchers invest considerable effort in analyzing and improving these standards, ensuring they can withstand the barrage of sophisticated cyberattacks. It’s a field defined by relentless innovation and forward-thinking strategies.
Challenges and Future Directions in Encryption
The journey of encryption standards is far from over. As we look to the future, emerging technologies like quantum computing pose new challenges. These advancements could render current encryption methods obsolete, necessitating the development of post-quantum cryptography strategies. Staying ahead in this arena demands vigilance and proactive strategies, ensuring that encryption standards for data protection remain robust and relevant in an ever-changing digital world.
—
- AES (Advanced Encryption Standard): Adopted by the U.S. government, AES is renowned for its high level of security and efficiency.
- RSA (Rivest-Shamir-Adleman): Widely used for secure data transmission, RSA provides robust public key encryption.
- SSL/TLS Protocols: Secure Sockets Layer and Transport Layer Security are staples for securing internet communications.
- Elliptic Curve Cryptography (ECC): Known for its efficiency in resource-constrained environments, ECC offers a favorable security-per-bit ratio.
- Quantum Cryptography: An emerging field, focusing on quantum key distribution for potentially unbreakable encryption.
- DES (Data Encryption Standard): A former standard, now largely obsolete due to advances in computing power and cryptanalysis techniques.
- PGP (Pretty Good Privacy): Often used for securing emails, PGP offers end-to-end encryption, ensuring message confidentiality.
Discussing Encryption’s Role
Encryption standards for data protection are more than just technical specifications; they are fundamental in securing our digital life. As technology progresses, the deployment of sophisticated encryption techniques becomes even more critical. With the rise of cyberattacks, breaches, and identity thefts, encryption standards are our first line of defense. These standards work tirelessly, often behind the scenes, safeguarding sensitive personal and business information from falling into wrong hands.
Encryption standards encompass a range of technologies, from block ciphers like AES to public key systems like RSA. Each plays a distinct role in data protection strategies across various sectors, including finance, healthcare, and government. Their efficiencies not only prevent unauthorized access but also provide assurances of data integrity and authenticity. This functionality is indispensable in environments requiring rigorous security measures.
Advancements in technology present both opportunities and challenges for encryption standards. For instance, while quantum computing could render existing encryption protocols less effective, it also opens doors to developing more sophisticated algorithms. In this landscape, continual innovation and adaptation are essential. Active collaboration between researchers and industry experts is crucial in developing new security paradigms that address the evolving nature of cyber threats.
Ultimately, encryption standards are not just about encryption itself but about fostering trust in digital interactions. They assure users that their online engagements are private, secure, and reliable. By understanding and implementing these standards, both individuals and organizations can navigate the digital age with confidence. As the cyber world grows, so must our commitment to innovative and resilient encryption solutions.
—
The Future of Encryption in a Digital World
Encryption standards for data protection are foundational pillars in our digital ecosystem. These protocols not only secure our information but empower us to interact online with confidence and peace of mind. As cyber threats evolve, so do these standards, striving to offer robust solutions tailored to emerging challenges.
A keen understanding of encryption standards provides a significant advantage in today’s tech-centric world. These standards are not merely tools; they are key strategies in building secure systems. From personal data protection on smartphones to securing large-scale enterprise networks, encryption is everywhere, universally working behind the curtains.
Innovations and Emerging Trends in Encryption
The world of encryption is ever-changing. We are now witnessing an era of exciting advancements like homomorphic encryption, which allows data to be processed without being decrypted. Such innovations could redefine our approach to data security entirely, offering unprecedented privacy safeguards.
Emerging fields like quantum cryptography hold promise for unbreakable encryption in the future. Researchers around the globe are actively exploring this domain, aspiring to achieve next-level security standards that safeguard against even the most advanced computing technologies.
In roundtable discussions and industry events, experts frequently emphasize the importance of investing in research and development for encryption technologies. As threats continue to grow in sophistication, staying ahead necessitates a proactive and forward-thinking approach in developing encryption standards for data protection.
Finally, adopting these next-gen encryption standards can transform how we perceive and manage digital security. By embracing advancements and continuously updating our knowledge base, we can arm ourselves against relentless cyber threats, ensuring that our data remains in safe hands now and in the future.
—
Eight Insights into Encryption Standards
- Comprehensive Security: Encryption standards form the bedrock of digital security by securing data from unauthorized access.
- Industry Adoption: Wide adoption across industries, from finance to healthcare, speaks to the trust placed in encryption standards.
- Scalable Solutions: These standards offer scalable solutions adaptable to different organizational needs.
- Resilient Protocols: Constant updates ensure encryption protocols remain resilient against evolving cyber threats.
- Consumer Trust: Encryption fosters trust, encouraging users to share sensitive data knowing it’s protected.
- Cross-Platform Protection: Ensures protection across diverse platforms, from web applications to mobile systems.
- Data Integrity: Maintains integrity, ensuring data has not been altered during transmission or storage.
- Regulatory Compliance: Abiding by these standards helps organizations meet various security regulations and compliance mandates.
Encryption standards for data protection aren’t just buzzwords thrown around in tech circles; they are crucial elements that secure our digital identities. By encrypting sensitive information, these standards ensure that only authorized persons can access critical data, preventing unauthorized intrusions and data breaches.
The spectrum of encryption methods available allows for tailored solutions to match specific security needs. Whether securing communications between devices or encrypting data stored in the cloud, these standards provide a robust framework for data security across varying platforms and applications.
With continued technological advancements, the importance of adapting and strengthening encryption protocols remains paramount. Discussions revolve not only around the threats posed by potential breaches but also the opportunities for advancement through research and innovation. Aligning business practices with strong encryption standards isn’t just about compliance; it’s about demonstrating a commitment to security and fostering a culture of trust and reliability.
—
Exploring Encryption and Its Impact
In today’s digital age, understanding encryption standards for data protection is not just advisable—it’s imperative. The significance of these standards cannot be overstated, as they are instrumental in safeguarding sensitive information from myriad cyber threats. Encryption transforms readable data into a coded format, accessible only to those with the right keys. As we dissect the importance and functionality of these standards, we’ll see just how crucial they are in maintaining digital privacy and security.
Consider the vast array of personal data shared online, from banking details to social media interactions. Encryption standards ensure that this data remains confidential and protected against malicious access. As cyberattacks grow more sophisticated, the need for robust encryption mechanisms becomes ever more pressing. Staying up to date with the latest advancements in this field helps both individuals and businesses protect their digital assets effectively.
The Role of Encryption in Consumer Protection
Encryption is a cornerstone of consumer protection online. It secures transactions, ensuring that sensitive information like credit card details are transmitted safely. Encryption standards like SSL/TLS provide the backbone for secure online transactions, cultivating an environment of trust between consumers and service providers. By employing robust encryption, businesses not only comply with regulations but also assure their customers of their commitment to data security.
Moreover, as regulatory landscapes evolve, adhering to encryption standards becomes critical. Compliance with data protection laws often hinges on the use of approved encryption protocols. Failing to implement these standards can lead to significant legal repercussions and loss of consumer trust. The stakes are high, and businesses must invest in effective encryption solutions to keep abreast of regulatory requirements and safeguard their reputation.
Progressing Toward Future-Ready Encryption
As we look towards the future, the role of encryption in securing data continues to expand. Emerging technologies like the Internet of Things (IoT) and 5G connections demand encryption approaches that are both robust and efficient. The challenge lies in balancing the need for security with the necessity for speed and performance. Innovations in encryption protocols strive to address these demands, creating solutions that are both resilient and practical.
Encryption standards for data protection are the defense line against unauthorized access and data exfiltration. They form an essential part of the global strategy to combat cybercrime, working silently yet effectively to protect the sensitive personal and business data housed on digital platforms worldwide. Remaining informed about these standards is crucial for anyone engaged in the digital ecosystems.
Engaging with the Encryption Community
One of the most effective ways to keep encryption standards at the forefront of data protection is through active engagement with the broader encryption community. Forums, conferences, and collaborative projects provide invaluable opportunities to share knowledge, strategies, and insights. Through this collective approach, the industry can continue to innovate, address challenges, and develop robust solutions that tackle emerging threats head-on.
By promoting the benefits and necessity of encryption standards, businesses and individuals alike can contribute to a more secure digital world. Whether through educational initiatives or direct implementation, embracing encryption technologies not only protects data but also builds a foundation of trust and reliability in an increasingly interconnected world.
Harnessing the potential of encryption standards for data protection requires concerted effort and collaboration across the technology sector. As we adapt to new challenges, these standards remain a vital component in the toolkit for digital security, ensuring confidentiality, integrity, and accessibility across the modern information landscape.
—
I hope this comprehensive content meets your expectations! Let me know if there’s anything else you need assistance with.