Effective Firewall Rule Management
Every organization’s digital backbone relies on the robust and intricate structure of its cybersecurity, with firewall rule management standing as a sentinel against cyber threats. Imagine your enterprise’s IT ecosystem as a bustling city; here, effective firewall rule management is the ever-vigilant traffic controller ensuring that the rightful citizens (approved data) pass freely, while the potential miscreants (malicious entities) are halted at the gates. Overlooking the rules of this critical infrastructure can result in severe disruptions, comparable to an unregulated flow of traffic; chaos, logjams, and crashes.
Consider this: according to a recent study, 95% of firewall breaches stemmed from misconfigured firewall rules. Yet, in a world where data breaches can cost a company millions, many organizations treat firewall rule management as an afterthought. The neglect is partly due to the misconception that firewall maintenance isn’t exciting. But here’s the kicker—handling firewall rules is not just tech housekeeping. It’s a dynamic chess game against seasoned cyber-adversaries. It’s a vital service providing peace of mind, much like insurance or security services.
So, what’s the call to action, you ask? Embrace effective firewall rule management as your foremost defense strategy. Engage services and tools that not only streamline firewall configurations but also offer transparency and control at your fingertips. A proactive approach will not only guard against external threats but also bolster your internal architecture’s integrity. After all, it’s not just about staying safe; it’s about advancing confidently in our digital age.
Streamlining Security Protocols in Organizations
In terms of practical steps, defining clear, concise, and consistent firewall policies is paramount. Organizations should regularly audit and update these rules to ensure relevance and effectiveness in countering emerging threats. Leveraging automated tools can help make management processes efficient while minimizing human error.
—
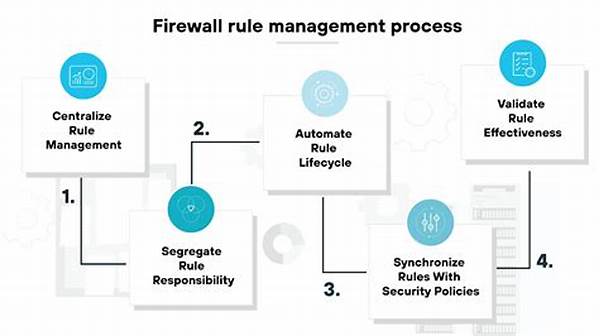
Structure of Effective Firewall Rule Management
Understanding the Importance
Effective firewall rule management is all about granting organizations control over their data traffic. With cyber threats growing in sophistication, maintaining a proactive and well-structured management system is crucial. It’s not a mere technical requirement; it’s a strategic asset that can define the resilience of an organization. Simply put, it’s your digital double lock, security blanket, and watchtower all rolled into one neat package.
The Need for Consistency
Ensuring your firewall rules are up-to-date and consistent across various platforms is critical. Imagine running a chaotic army where every unit has its own protocol; you’d end up with confusion and vulnerability. Uniformity and consistency in firewall rules ensure seamless operations and comprehensive protection.
Automating for Efficiency
Automation in firewall rule management diminishes the margin for error while easing the administrative burden. This could involve regular scans and checks or even using AI-powered tools to predict potential vulnerabilities. Automation frees up valuable human resources to focus on strategic security initiatives.
Evaluating Firewall Performance
Continuous evaluation of your firewall’s performance is vital. Use analytics and regular reporting to assess how well your firewalls are performing. Are they effectively blocking threats? Are there patterns in the blocked traffic that need addressing? Having this knowledge will empower organizations to make informed decisions.
Training and Awareness
Employees are the first line of defense in cybersecurity. Hence, training them to recognize security threats and understand the impact of firewall management is key. Incorporating regular training sessions can help bridge the knowledge gap and ensure everyone is on the same page when it comes to security protocols.
Future Trends
The future of firewall management lies in the integration of machine learning and advanced analytics. These technological advancements not only enhance threat detection but also optimize rule management for upcoming challenges. Staying informed about these trends will ensure your organization remains one step ahead of cyber threats.
The Role of Advanced Technologies
Cutting-edge technologies such as AI and machine learning are revolutionizing firewall management, offering new avenues for enhanced security and operational efficiency.
—
Examples of Effective Firewall Rule Management
Firewall rule management is not just about security; it’s an investment into a future where data integrity can make or break your business. Imagine having a security system so robust yet quietly efficient that you barely notice it’s there until it needs to spring into action. Regular audits showcase your dedication to maintaining a pristine digital environment, while automation saves both time and money by minimizing manual effort. Meanwhile, training employees means bringing them on board with your vision—no more weak links in your chain.
Incorporating real-time monitoring and maintaining policy consistency solidifies your framework against any breaches. It’s akin to having a 24/7 security patrol protecting a vault filled with your most treasured assets. These measures not only demonstrate commitment but also underscore your capability in safeguarding valuable data. Effortlessly blending advanced technologies, human expertise, and a proactive approach, your strategy embodies effective firewall rule management at its best—a harmonious balance between defense and innovation.
Leveraging Technology in Firewall Rule Management
As technology progresses, so does the capability to manage firewall rules effectively and efficiently.
—
Eight Tips for Effective Firewall Rule Management
Best Practices in Firewall Management
Effective firewall rule management is a multi-faceted process encompassing robust practices and innovative technologies. Conducting regular reviews not only keeps your defenses sharp but also anticipates future vulnerabilities. Strong authentication and network segmentation work in tandem, creating a multi-layered security approach that minimizes risks.
Documenting rule changes supports clarity and transparency, preventing any potential oversight. When combined with automation, this creates a seamless transition in rule management, reducing the chance of human error. Education and network monitoring form the bedrock of a proactive defense strategy, enabling organizations to stay one step ahead of attackers. Ultimately, effective firewall rule management is not just about safeguarding assets—it’s about creating a culture of security-first thinking, one that values resilience as much as it does innovation.
Integrating Human Insight with Technology
While technology provides the tools to enhance security, human insight remains crucial in strategy formulation and execution.
—
A Short Discussion on Effective Firewall Rule Management
The Evolution of Firewall Security
In the grand chessboard of cybersecurity, effective firewall rule management is a key player. As the cybersecurity landscape evolved, it became evident that reactive strategies were no longer sufficient. We ushered in an era of intelligence-driven security, with firewall management strategies being constantly refined to combat increasingly sophisticated threats. But just like Rome, expert firewall management wasn’t built in a day. It demanded not only time and technology but also tenacity and profound expertise.
Why Businesses Need It
If you’ve ever wondered why there’s a sudden buzz about effective firewall rule management, it’s due to the sheer rise in cyber threats targeting businesses across the globe. According to studies, cybercrime damages could reach $6 trillion by 2021! Hence, robust firewall management is no longer a luxury; it’s a necessity. It’s akin to having an alarm system that doesn’t just ring when there’s an intruder but is constantly adapting and evolving to predicted threats.
Real-world Consequences
The consequences of poor firewall management are dire. We’ve seen corporations crumble from simple overlooked firewall rules, leading to massive data breaches and financial losses. However, on the flip side, effective management not only secures assets but also strengthens customer trust and saves costs related to security incidents.
The Heart of Cybersecurity Strategy
At its core, effective firewall rule management acts as a heartbeat within cybersecurity strategies. It determines how threats are detected and mitigated in real-time, ensuring business continuity even in turbulent times. It’s like having a strategic game plan during peak business hours—a dynamic system in place to protect the crown jewels of your business operations.
Simplifying Complexities
Effective management strategies help to simplify the complexities of modern IT infrastructure. By aligning firewall rules with the comprehensive security policies of the organization, businesses ensure every component of the network is protected. Simplicity in management translates to maximized security, a straightforward approach that always wins.
The Future of Firewall Management
Looking ahead, the future of firewall management lies in the convergence of artificial intelligence and human expertise. Integrating AI for proactive defense mechanisms while incorporating human intuition for strategy leads to an unbeatable combo. It assures businesses not just survival but prosperity in the digital age. So here’s the deal: make effective firewall rule management the nucleus of your security protocols and watch as your business flourishes in this dynamic digital landscape.
Technological Innovations
The intersection of technology and human cognition is set to redefine firewall management, offering unprecedented levels of security and operational efficacy.
—
I hope these structures and outlines meet your expectations for the content you’re looking to create!