- The Role of AI in Developing Effective Threat Intelligence Solutions
- Integrating Threat Intelligence in Business Operations
- Introduction to Developing Effective Threat Intelligence Solutions
- Analysis in Developing Effective Threat Intelligence Solutions
- Descriptive Overview
- Short Discussion on Developing Effective Threat Intelligence Solutions
In today’s digital age, where data breaches and cyber threats have become almost daily news, developing effective threat intelligence solutions is more critical than ever. It’s no longer a question of “if” but “when” an organization will face a cyber threat. The need for robust strategies to detect, prevent, and mitigate such threats has never been more pressing. The cyber landscape is continuously evolving, with hackers employing sophisticated methods and constantly changing their tactics. As a result, businesses need a proactive approach to cyber defense, which begins with understanding their enemies’ tactics, techniques, and procedures.
Knowing your adversary is half the battle. By anticipating the moves a hacker might make, a business can better prepare its defenses. The development of effective threat intelligence solutions involves gathering and analyzing data about potential or existing threats. This process includes pinpointing potential vulnerabilities and developing strategies to eliminate or reduce risks. However, implementing these solutions requires more than just software; it demands an intricate understanding of the hacker’s mindset and goals. Companies must invest in innovative solutions and skilled personnel to interpret and act upon the threat data accurately.
Creating an efficient threat intelligence system is akin to crafting a well-oiled machine. Each component, from data collection to analysis and action, must work seamlessly together, ensuring rapid and accurate responses to potential threats. Organizations need tools that not only identify threats but also recommend the best course of action. These systems need to be dynamic, adapting to the ever-changing threat landscape. Moreover, companies must cultivate a culture of awareness and continuous learning to stay ahead of potential attackers. This means regular training, threat simulations, and staying updated on the latest cyber threat trends.
Amidst this high-stakes game of cyber warfare, humor can be a surprisingly useful tool. Incorporating humor into training and awareness programs can make the often dry and technical content more engaging and memorable. Picture a mock-up phishing email allegedly sent by “The Notorious Phish,” complete with gangster-themed graphics. Such touches not only capture the employees’ attention but also reinforce key messages in an enjoyable manner. In this digital age, the ability to laugh while learning is invaluable, enabling teams to remember critical information under pressure.
The Role of AI in Developing Effective Threat Intelligence Solutions
Artificial Intelligence (AI) plays a pivotal role in enhancing the efficiency and effectiveness of threat intelligence solutions. By automating data analysis, AI systems can rapidly process vast amounts of threat data in ways unimaginable for human analysts. Machine learning algorithms can identify patterns and predict potential threats, enabling organizations to act before an attack occurs. Additionally, AI-driven solutions provide real-time updates, ensuring that security teams always have the latest information at their fingertips.
Crafting an effective threat intelligence framework involves an integrated approach that prioritizes precision and adaptability. This development hinges on understanding the dynamic threat landscape and deploying technologies that enhance threat detection and response.
Firstly, it’s crucial to define the objectives of the threat intelligence solutions. The goals should focus on identifying threats promptly, analyzing potential impacts, and offering actionable insights. Clear objectives provide a roadmap, ensuring every component of the threat intelligence operates in unison toward a single goal: robust defense.
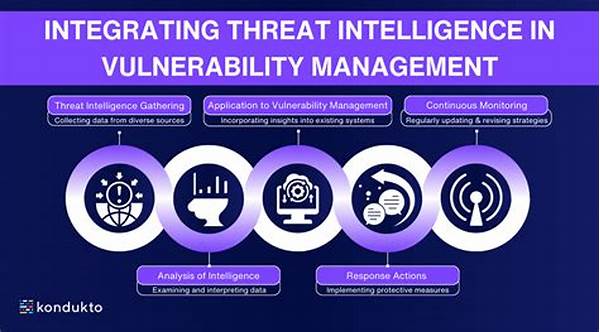
Data collection is the next step. Gathering accurate and relevant data from internal and external sources forms the backbone of threat intelligence. This data needs to be diverse, drawing from network logs, threat feeds, and even open-source intelligence. With a rich data pool, security teams can glean a comprehensive understanding of potential threats.
Integrating Threat Intelligence in Business Operations
Once the data collection systems are in place, the analysis phase begins. Here, tools like AI and machine learning become invaluable, processing large datasets to identify anomalies and patterns indicative of threats. Through integration with existing business operations, these insights can trigger automatic responses to potential threats, minimizing delays in mitigation.
Importance of Skilled Professionals
While technology is vital, human skills remain irreplaceable. Security analysts play a crucial role in interpreting data and deciding on the best course of action. Their expertise enables swift adaptation to new cyber threats and ensures that business strategies align with the evolving threat landscape.
Finally, continuously evaluating and updating the intelligence solutions is essential. The cyber world evolves rapidly, and intelligence solutions must evolve too, incorporating new technologies and strategies. Through regular reviews and updates, businesses ensure that their defenses remain robust and relevant.
Introduction to Developing Effective Threat Intelligence Solutions
In the ever-expanding digital universe, the specter of cyber threats looms large. It’s more than just the intricate dance of code and data; it’s a battlefield where every byte counts. Developing effective threat intelligence solutions offers a shield in this cyber wilderness. But what makes these solutions tick? It’s more than just algorithms and firewalls; it’s the human touch behind the systems. Every click, every decision, that’s where the magic happens.
Imagine your company as a medieval castle. Developing effective threat intelligence solutions is akin to having the sharpest archers and the most vigilant watchmen. They see the enemy before it reaches the gate, sounding the alarm, ensuring your kingdom remains unbreached. It’s about seeing the unseen, predicting the unpredictable. With these solutions in place, you’re not just defending — you’re anticipating. You’re stepping into the future of cybersecurity, armed and ready for whatever comes your way.
Analysis in Developing Effective Threat Intelligence Solutions
In the intricate realm of cybersecurity, the significance of developing effective threat intelligence solutions cannot be overstated. The need for such solutions stems from the evolving nature of cyber threats, which are becoming increasingly sophisticated. Addressing these threats requires a comprehensive strategy that integrates both technology and human expertise.
The Functionality of Threat Intelligence Solutions
At the core of these solutions is the capability to analyze vast datasets quickly. With real-time data processing, organizations can identify and isolate potential threats before they manifest into full-blown attacks. However, the strength of threat intelligence lies not only in its predictive capabilities but also in its adaptability — the ability to learn and evolve from every interaction, making future threats easier to manage.
This adaptability is crucial when considering the varied nature of threats faced by organizations today. From phishing scams to advanced persistent threats (APTs), the spectrum is broad and requires a nuanced approach to threat intelligence. Solutions must be tailored to the specific needs of an organization, offering customizable features that align with business goals and risk appetites.
Furthermore, fostering a culture of cybersecurity within the organization amplifies the effectiveness of these solutions. Training and awareness initiatives ensure that every team member is equipped with the knowledge to recognize and respond to potential threats, forming the first line of defense against cyberattacks.
Descriptive Overview
Developing effective threat intelligence solutions is akin to crafting a master strategy in a game of chess. Every move must be thought out, considering the potential response of the adversary. This is not just a reactive approach but a proactive stance, embedding intelligence at every level of the organization. The intelligence derived is not just data but actionable insights that guide the organization’s security posture.
At its core, threat intelligence serves as a crucial component of an organization’s defense mechanisms. By harnessing it effectively, companies can shift from a reactive stance to a proactive one, preemptively addressing threats before they evolve. This proactive approach not only mitigates risks but also significantly reduces potential financial and reputational damages associated with cyberattacks.
Short Discussion on Developing Effective Threat Intelligence Solutions
The world of cybersecurity is as treacherous as it is intriguing. Developing effective threat intelligence solutions stands as a beacon of hope amid this tumultuous landscape. The essence of these solutions lies in their ability not only to detect and neutralize threats but also to predict them, thereby keeping organizations one step ahead of cybercriminals. This foresight is invaluable in an era where data is the new currency, and one breach can spell disaster.
Central to threat intelligence solutions is the synthesis of data into actionable insights. It’s like turning raw iron into a sharp sword, ready to defend against the cunning foes lurking in the digital shadows. Each byte of data can be a clue, revealing patterns and anomalies that skilled analysts can turn into countermeasures against prospective attacks. This blend of technology and human ingenuity is the cornerstone of any robust cybersecurity framework.
The Impact of Cyber Threats
Even the mention of a cyberattack can cause anxiety in the boardroom. It’s not just the immediate financial implications but the long-lasting reputational damage that organizations fear. Developing effective threat intelligence solutions eases these fears by providing a comprehensive security blanket. Through automation and AI-augmented analysis, these solutions reduce the response time, enabling organizations to fend off attacks promptly and efficiently.
The implementation of threat intelligence is an investment in resilience. It’s about constructing a digital fortress that’s equipped to push back against any threat, ensuring the safety and integrity of organizational data. A successful threat intelligence solution is not an expense but a strategic asset, paving the way for business continuity and innovation in a secured environment.
Developing effective threat intelligence solutions is an ongoing journey. It’s about staying vigilant in the face of evolving threats and continuously enhancing capabilities. With cyber threats showing no signs of slowing down, the need for innovative and adaptable measures is clear. Through sophisticated intelligence solutions, businesses can not only defend against cybercriminals but also thrive in the digital age.
In essence, crafting a robust threat intelligence framework requires a multi-faceted approach. From leveraging cutting-edge technology to fostering a culture of awareness and collaboration, the pieces must fit together seamlessly to form an unyielding defense. As cyber threats become more complex, the role of threat intelligence in maintaining digital security cannot be overstated.