In the digital age, security is paramount. You’ve probably heard stories of cyber breaches costing companies millions, or about sensitive data being leaked, causing irreparable damage to reputations. But have you ever wondered how those incidents might have been prevented? Welcome to the world of “Defense in Depth Strategies”. It’s like the digital equivalent of a castle’s fortifications, layered with multiple strategic defenses. Imagine walls, moats, and watchtowers designed not just to deter attackers but to handle them at every stage of an assault. These strategies aren’t just for tech giants or government institutions; they are essential for any organization that values its data and its customers’ trust. Buckle up as we dive into the fascinating and crucial realm of Defense in Depth Strategies, exploring how these layered defenses can save your organization from potential disaster.
Why Defense in Depth is a Must
Defense in depth strategies offer a unique selling point by utilizing multiple layers of defense to protect data. Imagine a burger layered with all your favorite ingredients where each layer offers a different type of protection—one might repel spam, another detects intruders, and yet another encrypts data. This layered approach doesn’t just halt would-be cyber intruders; it confounds and frustrates them at every turn. The true genius of defense in depth strategies lies in how they blend the rational and emotional aspects of security, making it not just a tech necessity but a business asset. They are like a high-tech, expert security team ready to respond before you even know there’s a problem, thus securing not just systems but peace of mind.
So, whether you run a startup or a seasoned enterprise, adopting defense in depth strategies isn’t just smart; it’s essential to stay ahead of potential threats. Imagine being that savvy businessperson who foresaw security breaches and thwarted them with foresight and strategy. The demand for such prowess is high, and implementing these defense layers effectively positions your company as a fortress against the perils that lurk online.
Layers of Security: The Heart of Defense in Depth
Let’s break down the magic of this robust strategy. At its core, defense in depth strategies feature multiple layers of security measures. Each layer is unique and serves its purpose, from firewalls and intrusion detection systems to encryption and two-factor authentication. But they all converge into a single goal—to deter, detect, delay, and respond. This strategy works as much as a deterrent as a countermeasure. The modular nature of these layers allows organizations to customize solutions that best fit their needs, making it not just a one-size-fits-all security blanket but a bespoke armor.
Employing these strategies is like having a superpower in the business world, allowing organizations to anticipate threats and adapt accordingly—like a fashionista constantly updating their wardrobe based on the latest trends, only in this case, the ‘trend’ is evolving cyber threats. Simply put, defense in depth strategies aren’t just about defense. They represent a proactive, comprehensive approach to organizational security, blending creativity with cutting-edge technology. Whether you’re a budding startup or an established giant, you owe it to yourself to consider these strategies.
The Future of Defense in Depth: Adaptation and Innovation
Looking forward with defense in depth strategies, we see a necessity for adaptation and innovation. As cyber threats evolve, so must our defenses. Like an ever-changing video game, every level presents new challenges requiring novel solutions. Advances in artificial intelligence and machine learning promise exciting enhancements to defense in depth strategies, offering organizations quicker predictions and a more agile response to cyber threats.
Furthermore, embracing cloud computing and the Internet of Things does not mean forsaking security; it’s about evolving our strategies to cover these new vectors. It’s about staying one step ahead of cybercriminals who thrive on exploiting new technology—and who, spoiler alert, never rest. Defense in depth strategies are not just evolving but are becoming smarter, more intuitive, and more critical than ever.
—
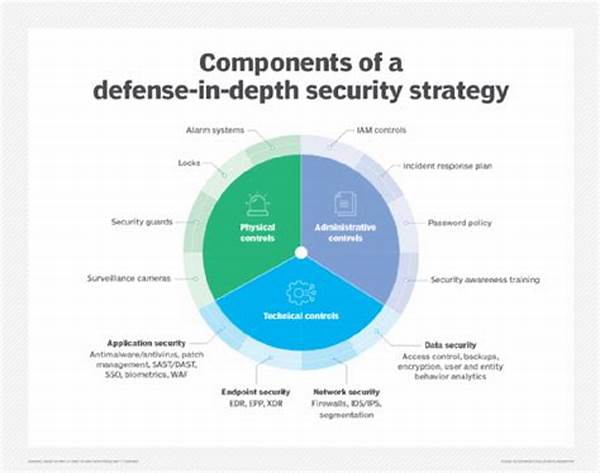
Understanding Defense Layers
Understanding the specific layers within a defense in depth strategy allows organizations to critically analyze and customize their security posture.
Physical Security
Physical security refers to the foundational layer against cyber threats. This involves traditional security measures like locked doors, surveillance cameras, and secured access points to physically protect hardware and data centers.
Network Security
Network security mechanisms such as firewalls and anti-virus software are essential for defending against unauthorized access and exploitation.
Host Security
This layer focuses on protecting individual devices with measures like endpoint detection and system hardening to prevent unauthorized access and maintain system integrity.
Application Security
Application security ensures that software applications are secure from design through deployment, including using secure coding practices and performing regular security audits.
Data Security
Data security involves encryption and access controls to ensure that sensitive information is safeguarded against unauthorized access and breaches.
User Hygiene
Training employees about security best practices is a crucial yet often underestimated layer in defense in depth strategies. This includes phishing awareness and safe browsing habits.
Incident Response
Having a solid incident response plan, which includes regular drills and defined roles, ensures preparedness and swift action in the event of a breach.
Governance and Compliance
Ensuring that your organization adheres to industry standards and regulations boosts your defense in depth strategies by holding all layers accountable and continuously improving them.
Continuous Monitoring and Improvement
Lastly, it’s crucial to regularly monitor security measures and adapt them as necessary, using analytics and threat intelligence to stay ahead of potential cyber threats.
—
Exploring Defense Mechanisms
By understanding these layers, organizations can create a robust defense against threats, ensuring a proactive stance in an ever-evolving cyber ecosystem.