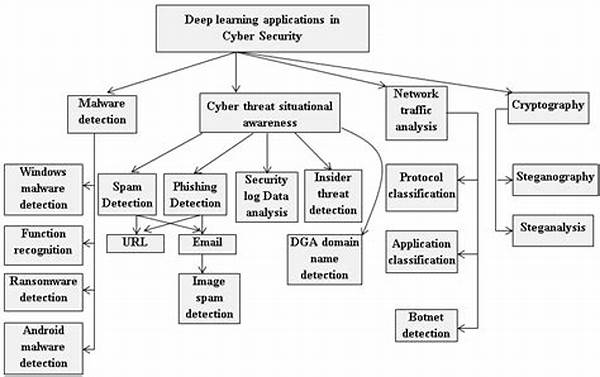
Deep Learning Techniques in Network Security
In the ever-evolving digital landscape, network security remains paramount as cyber threats become increasingly sophisticated. One of the most exciting advancements in combating these threats is the application of deep learning techniques in network security. Deep learning, a subset of artificial intelligence, is transforming the way we approach network protection, making it more resilient, efficient, and proactive. The appeal of deep learning lies in its ability to learn from vast amounts of data, recognize patterns, and make intelligent predictions, mimicking the way humans learn. This is particularly useful in network security, where the dataset can be extensive and complex, with threats varying greatly in nature and intensity.
Delving deeper, deep learning techniques in network security are now being deployed to detect anomalies, identify malware, and respond to breaches rapidly. With the rise of connected devices and cloud computing, traditional security measures are often not enough to counteract cyberattacks. Here, deep learning models play a crucial role, as their capacity to handle diverse datasets allows for the identification of previously unknown threats, traditionally termed as zero-day threats. These threats can be detected quickly, allowing for swift action that can save a network from potential damage.
Moreover, the implementation of these deep learning techniques is not only enhancing existing security frameworks but is also revolutionizing threat response strategies. The real-time processing capabilities have led to the development of Intrusion Detection Systems (IDS) that can operate autonomously, learning and adapting to new cyber threats without constant human intervention. Thus, businesses seeking to safeguard their digital assets should consider integrating deep learning techniques in network security to stay one step ahead of cybercriminals.
The Role of Deep Learning in Network Defense
As we delve into the world of network security, leveraging deep learning techniques in network security has become a game-changer. These techniques provide a robust solution to the ever-increasing sophistication of cyber threats. But how exactly are these techniques reshaping the landscape of network security?
Discussing Deep Learning Techniques in Network Security
In today’s digital era, network security has become a critical concern for organizations worldwide. With the advent of deep learning, the capabilities of network defense mechanisms have reached unprecedented levels. This section will delve into the intricacies of deep learning techniques in network security, exploring their roles, challenges, and future potential.
Firstly, it is essential to comprehend how deep learning techniques work in the context of network security. At the core, these techniques involve using neural networks that mimic human brain functions, analyzing data, recognizing patterns, and predicting outcomes. In network security, these capabilities are used to identify anomalies, filter incoming data packets, and discern potential threats in real-time. This forward-thinking approach allows organizations to preemptively counteract potential cyber threats.
Despite its effectiveness, deploying deep learning techniques in network security is not without challenges. One of the primary concerns is the requirement for large datasets to train the neural networks effectively. The larger and more diverse the dataset, the more accurate the predictions and detections. Moreover, the computational power needed to process this data at scale can be significant, highlighting the necessity for high-performance infrastructure. However, these challenges are mere roadblocks in the broader scope of fortifying network security with advanced AI techniques.
As we look to the future, the continuous evolution of deep learning techniques offers promising potential. These advancements are paving the path for even more sophisticated systems capable of adapting to ever-changing threat landscapes. With ongoing research and development, future systems will likely boast improved accuracy, speed, and learning efficiency. For any organization aiming to stay ahead in the cybersecurity arena, incorporating these cutting-edge solutions is not just advantageous; it’s a necessity.
Implementing Deep Learning Techniques in Modern Cybersecurity Practices
The current era of cybersecurity is dominated by advancements in artificial intelligence, with deep learning techniques in network security at the forefront. By integrating AI, businesses seek to enhance the robustness of their security measures. But what makes these technologies indispensable to modern cybersecurity practices?
One critical aspect is the precision and swiftness that deep learning models bring to the table. Traditional systems can often be reactive, identifying threats only after they manifest. In contrast, deep learning enables a more proactive stance with predictive analytics, enabling organizations to address vulnerabilities before they can be exploited. Additionally, deep learning thrives on anomaly detection—a key feature that alerts security personnel to unusual activities, potentially indicating threats that would otherwise remain unnoticed.
Despite the revolutionary benefits, businesses must also navigate the complexities that come with the deployment of these technologies. Establishing a deep learning-powered cybersecurity framework requires substantial investment in both financial and human resources. The training and development of these models necessitate expertise that transcends traditional IT skills, often requiring data scientists and AI specialists to ensure optimal functionality.
With these insights in mind, deep learning techniques in network security are more than just a trend—they are shaping the future of how we protect digital infrastructures. As cyber threats evolve, so must our approaches to combating them. By investing in and embracing these cutting-edge solutions, organizations can not only safeguard their assets but also gain a competitive edge in digital resilience.
Potential Topics Related to Deep Learning Techniques in Network Security
Deep learning techniques in network security offer unparalleled promise in revolutionizing how we handle cyber threats. The technology is undoubtedly complex, yet the benefits it delivers are worth the investment. For organizations willing to embrace this new era of cybersecurity, the journey toward heightened digital protection has already begun. But the pertinent question remains: Are we prepared for the challenges involved, and what strategies can we employ to overcome them?
One of the primary considerations involves acquiring the right expertise and technology to deploy these systems effectively. The models must be trained on suitable datasets, which require substantial resources and planning. Additionally, businesses must foster a culture that encourages continuous learning and adaptation to stay ahead of evolving threats. While these tasks may seem daunting, the potential rewards in terms of security and resilience are immense.
Ultimately, deep learning techniques in network security represent a bridge to a safer, more secure digital future. Embracing these innovations is not merely an option but an imperative for organizations intent on securing their assets. As we navigate this exciting frontier, taking actionable steps today will pave the way for a more robust cybersecurity defense tomorrow.