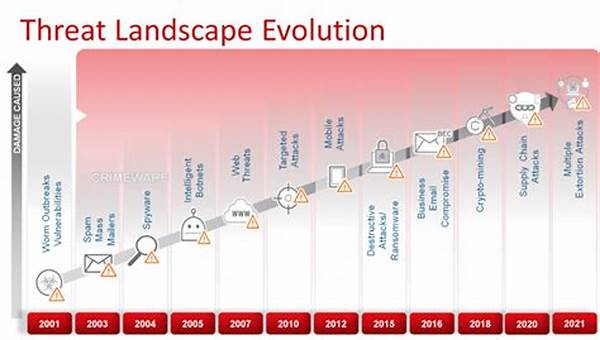
The digital age has ushered in a new era of convenience and connectivity, but with it comes a treacherous byproduct: cybersecurity threats that are evolving faster than ever. Imagine a bustling city where every inhabitant relies on technology for their daily lives. Suddenly, a shadowy figure appears, picking locks and sneaking into homes undetected. This is the reality in the virtual world today. Cybercriminals are getting stealthier, smarter, and more sophisticated, turning the cybersecurity threat landscape evolution into a complex battleground.
With each step of technological advancement, cyber threats evolve, resembling a high-stakes chess game where the digital pawns are data, identities, and financial assets. Every move they make requires creative counter-moves to fortify defenses. According to recent statistics, cybercrime will cost the global economy over $10 trillion by 2025. Hence, understanding the cybersecurity threat landscape evolution is no longer an option; it’s a necessity to protect what you cherish.
Businesses, whether a small town bakery or a multinational corporation, are on the frontlines. With humor and wit, they must navigate this digital battlefield, integrating pristine security practices and staying one step ahead of these virtual villains. But it’s not all doom and gloom; there’s a rewarding career in becoming a cybersecurity expert who can dismantle these threats like a seasoned detective.
The Rise of AI and Its Role in Security
In the riveting saga that is cybersecurity threat landscape evolution, Artificial Intelligence (AI) is the stunning protagonist. Once a mere sci-fi trope, AI is now the knight in shining armor safeguarding our digital frontier. By leveraging AI and machine learning, organizations can predict and act upon threats faster than the cyber villains can say “breach.”
However, it’s a double-edged sword. While AI enables us to create robust defense mechanisms, it also equips cybercriminals with tools to enhance their nefarious missions. The challenge lies in not just adopting AI but mastering it, ensuring that it acts as a guardian rather than a Trojan horse in disguise. AI isn’t simply a tool; it’s an ever-evolving teammate in the battle of cybersecurity threat landscape evolution.
—
Decoding the Modern Cyber Menace
In the grand tapestry of cybersecurity threat landscape evolution, understanding the protagonist and antagonist is key. The modern cyber menace isn’t just your average hacker — it’s a network of sophisticated entities using advanced tools. Cyber threats today range from ransomware attacks to supply chain compromises, each a strategic move to enact havoc.
For instance, ransomware has evolved dramatically. Originally a blunt instrument demanding direct payments, it’s now a cunning fox offering “double extortion”: stealing data before encryption to demand two payouts. Embrace the humor here — it’s like being pick-pocketed twice by the same thief and still managing to have your shoe laces stolen.
Yet, the comedy turns serious when data shows that over 60% of businesses reported experiencing some form of cyber attack in 2022. This stark statistic underscores the gravity of the cybersecurity threat landscape evolution and the importance of being prepared for the unseen and the unprecedented.
The Defensive Innovations
Amidst the storm of cyber threats, businesses are not helpless ships tossed at sea. With increasing awareness and innovation, effective strategies are emerging that promise smoother sailing. From zero-trust architectures to blockchain verification, the arsenal in this digital arms race is expanding.
Zero-trust — imagine an office where everyone wears ID cards. Without the badge, no one enters or accesses sensitive data, and every action is monitored. It’s a strategic stance that assumes every entity within and outside the perimeter is potential threats until verified trustworthy. It’s a bit of tech-jargon mixed with common sense — never trust, always verify.
The Human Factor
Let’s face it, human error is the comedic relief in the cybersecurity threat landscape evolution. Studies indicate that social engineering attacks like phishing are designed to exploit human psychological triggers. People love free stuff and the idea of winning that elusive prize; cybercriminals know this and deploy cunning ruses to have users click on malicious links.
But there’s hope! Organizations are recognizing the need for cybersecurity awareness training, educating employees to spot and report phishing attempts. The investment is worth it as it transforms the weakest link into the strongest defense. It is like teaching the gag-prone guards how to spot the mischievous figure before they swipe your imaginary keys.
—
Victories Amidst Chaos
Although the threats seem insurmountable, there are shining examples of cybersecurity triumphs that deserve recognition. It’s not just about the bad guys; it’s also about the heroes who have turned potential disasters into victory stories. Take the case of a resilient European bank that recently thwarted an elaborate supply chain attack, saving millions and setting a new standard for security protocols.
Or consider a renowned multinational that enhanced its digital security posture radically after an embarrassingly public breach, emerging stronger and more resilient. These tales of success serve as a testament to the fact that despite the evolution of threats, resilience and readiness can write a narrative that ends on a high note.
In a fun twist, a security team tricked an entire cybercrime cohort by feeding them misleading information, causing significant disruption in their operations. It reads like a spy novel and reminds us that intelligence, wit, and courage can sometimes catch the fox in its own trap.
The Map Forward
In this exhilarating and, at times, exhausting journey through the cybersecurity threat landscape evolution, what’s clear is the need for a proactive roadmap. Organizations must invest in technology, but equally important is investing in people and processes. Collaboration among industry partners, government agencies, and academia is paramount in mapping the world where every node is a trusted link.
Together, as tech evolves and cyber threats adapt, a community of informed and agile defenders can ensure a safer cyberspace for all. The times may be uncertain, but with the right precautions, the future doesn’t have to be. Press onward, digital warriors — the journey through the cybersecurity threat landscape evolution is ripe with challenge and opportunity.
—
Bringing the Story to Life
Visual aids are powerful allies in storytelling, especially in the multifaceted world of cybersecurity. Each illustration is a beacon, illuminating complex ideas with clarity and creativity. Imagine a vibrant poster plastered in an office, humorously portraying phishing attempts with a quirky character named “Phishy Pete” — a simple yet effective tool in increasing awareness and employee engagement.
Or visualize an animated story that maps out the sophisticated nature of a ransomware attack, journeying from initial infection to data recovery. It’s storytelling at its finest, relaying the critical stages plainly without losing the audience in technical jargon. By depicting the chaos visually, the path to understanding becomes smoother, ensuring everyone, from the tech-savvy to the beginner, comprehends the implications of the cybersecurity threat landscape evolution.
But remember, each stroke of artwork leaves an imprint. It educates, informs, and at times entertains, portraying the digital dance between security and threat not as a somber affair but as an adventure that, with the right lens, is engaging, captivating, and, ultimately, hopeful.