In today’s fast-paced digital world, safeguarding sensitive data and maintaining robust security protocols have become imperative. As cyber threats become increasingly sophisticated, organizations need to leverage innovative mechanisms such as cyber threat intelligence workflow automation to stay ahead of cybercriminals. This automation goes beyond mere protection—it streamlines the information gathering and threat analysis process, providing a proactive stance against potential breaches. By automating the workflow, security teams can filter through raw data efficiently, turning it into actionable intelligence while minimizing human error and maximizing efficiency. The convenience of automation helps to allocate resources strategically, allowing the skilled cybersecurity personnel to focus on critical thinking and problem-solving instead of repetitive tasks.
Organizations often face challenges like data overload, scattered threat intelligence sources, and rapid response demands. This creates a complicated terrain for security teams, who can easily become overwhelmed without proper tools and support. Automating these processes offers a lifeline, providing timely insights and enabling swift actions that could potentially save an organization from catastrophic breaches. It’s almost like having an assistant vigilant around the clock, continuously analyzing, learning, and adapting to new threats—ensuring security measures are not only responsive but anticipatory. The world of cybersecurity is ever-evolving, and so must be the strategies employed to secure the digital assets businesses rely on.
As tales of massive data breaches have shown, not having an advanced system like cyber threat intelligence workflow automation in place can cost corporations millions, damage reputations, and lead to loss of customer trust. Beyond the immediate financial implications, the long-term impacts on customer confidence and loyalty can be devastating. Thus, the question isn’t whether businesses should adopt cyber threat intelligence workflow automation; it’s about how swiftly they can implement these compelling system integrations to fortify their digital fortresses.
The Power of Automation in Cybersecurity
The integration of cyber threat intelligence workflow automation is revolutionizing how businesses approach cybersecurity. By dynamically aggregating threat data from different sources and automating the response mechanism, companies can ensure a robust defense system that not only shields but also learns and evolves. This adaptive nature of automated workflows positions companies to be one step ahead, making anticipatory decisions that circumvent risks even before they emerge as tangible threats.
—
The Benefits of Cyber Threat Intelligence Workflow Automation
Incorporating cyber threat intelligence workflow automation into your organization’s security framework is no longer a luxury; it’s a strategic necessity. Exploring the depths of its potential, this process does more than just push your defenses to the forefront; it cultivates a culture of proactive protection that encourages ongoing learning and adaptation. The beauty lies in its ability to bridge gaps between raw, scattered intelligence data and tailored, actionable insights that address specific threats tailored to an organization’s unique landscape.
With cybersecurity threats evolving at an unprecedented speed, it’s crucial to have an automated system that integrates seamlessly into existing infrastructures, providing continuous updates without stalling operations. This agility in adaptation not only enhances defense but also contributes to the resilience of the entire security architecture. By automating the workflow, you’re not just reacting to threats as they happen; you’re fortifying your defenses against future vulnerabilities, ensuring no stone is left unturned.
With a staggering increase in data breaches facing organizations of all sizes, automation is more than just a tool—it’s a lifeline. Those who have adopted cyber threat intelligence workflow automation can testify to the peace of mind it brings, allowing companies to dedicate their energies to growth rather than constantly putting out fires in the stormy realm of cyberspace. This strategy effectively mitigates risks while optimizing performance, reaffirming the importance of investing in advanced cybersecurity technologies.
As understudy to human officers, automation bridges the gap between inevitable human limitations and the growing complexity of cyber threats. It’s about redefining how businesses perceive and tackle cybersecurity issues by transforming tedious, error-prone processes into seamless, efficient operations. Adopting such cutting-edge technologies ensures not just survival but the thriving of businesses in the digital age.
—
Key Elements to Consider
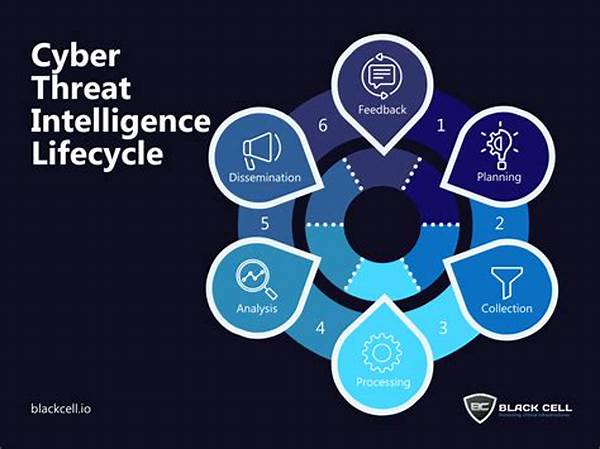
Understanding the pertinent elements in cyber threat intelligence workflow automation is fundamental to leveraging its full potential. The integration involves several core components—data collection, automated analysis, threat prioritization, and timely reporting. Each plays a pivotal role in managing and interpreting data, guiding organizations in making informed decisions. Impeccable analysis through automation results in prioritized threats that call for immediate attention, while low-level risks can be logged for routine checks, ensuring resources are effectively allocated.
The technological underpinnings of automation facilitate seamless cross-departmental coordination. It encourages communication between various team members across different departments, fortifying collective efforts in threat mitigation. This holistic approach enhances threat visibility and comprehension, which is crucial not only for immediate responses but also for long-term security strategy planning. Automation’s impact extends to providing historical analytics that informs future cybersecurity policies and infrastructure developments.
As automation tools become more sophisticated, they’re interwoven with machine learning and AI algorithms that enhance predictive analysis, detecting anomalies with higher precision and fewer false positives. By doing so, organizations enable themselves to detect and disentangle threats before they manifest, reaching an unparalleled level of preemption in cybersecurity. The strategic application of automation empowers decision-makers to act swiftly, demonstrating a proactive culture immersed in cybersecurity awareness.
Investing in cyber threat intelligence workflow automation is a testament to a company’s commitment to security excellence. By merging emerging technologies with traditional defensive measures, businesses garner a competitive edge—embracing advancement while fortifying through unparalleled security provisions. The journey of cybersecurity resilience starts with understanding the nuances and values embedded within cyber threat intelligence workflow automation, creating an armor that stands resilient against evolving cyber threats.
10 Examples of Cyber Threat Intelligence Workflow Automation
Exploring Practical Applications
The landscape of cyber threat intelligence workflow automation is filled with practical applications that invigorate security frameworks. Take, for example, phishing threat analysis automation, designed to streamline the process of identifying, categorizing, and mitigating phishing attacks. This not only reduces the burden on human resources but also significantly lowers the risk of an attack slipping through unnoticed.
Similarly, machine learning algorithms are revolutionizing the way companies predict and prepare for potential data breaches. By analyzing vast amounts of data captured from various sources, these algorithms can spot patterns indicative of potential threats, offering an additional layer of security and foresight. This intelligent prediction ability represents a monumental leap forward in preemptive cybersecurity measures.
Integrated automated threat reporting dashboards provide real-time alerts that empower organizations to act swiftly, addressing threats as they appear on the horizon. This instantaneous communication and response capability are crucial, especially considering the fast-paced nature of the digital threats they face today. Moreover, deploying automated endpoint detection and response systems adds a robust shield to network security, enhancing anomaly detection and intervention processes.
In the spirit of comprehensive security, automation enables the centralization of threat data from disparate sources, offering a singular, coherent picture of the security landscape. This synthesis of intelligence not only guides proactive strategies but also enhances retrospective analysis, paving the way for continuous improvement and adaptation in cybersecurity tactics. Embracing these technologies and methodologies grants businesses the agility and resilience needed to manage and thrive amid the escalating threat of cyber adversaries.
10 Illustrations of Cyber Threat Intelligence Workflow Automation
—
Deploying Automation for Robust Security
Deploying cyber threat intelligence workflow automation is not just a trend but an essential strategy for any modern business striving to protect its digital assets. One standout example of this is the automated process for examining email threats. A detailed flow chart can graphically represent how automation streamlines the verification process, mitigating the time spent on manual oversight while enhancing accuracy. This not only speeds up the threat detection process but also reduces the incidence of false positives that could otherwise disrupt business operations.
Visual materials, like algorithmic neural network illustrations, serve to clarify the mechanisms behind real-time threat detection. These tools provide a visual synthesis of complex processes, aiding stakeholders in comprehending the intricacies involved in automating cybersecurity tasks. By distilling complicated data into accessible formats, organizations can foster a greater degree of transparency and understanding within the team.
Furthermore, informative infographics about the benefits of automated threat intelligence processing provide invaluable insights, underlining key advantages such as efficiency, accuracy, and adaptability. They demonstrate how automation aggregates data from multiple intelligence sources into a unified, coherent threat picture. This visual aid complements the strategic implementation of automated processes, combining aesthetics with functionality to communicate essential security information effectively.
Such visual engagement promotes a culture of cybersecurity awareness and readiness that surpasses the boundaries of conventional safety measures. They emphasize the holistic nature of cyber threat intelligence workflow automation, ensuring that every layer of the organization is aligned with cutting-edge threat detection and mitigation strategies. By incorporating such illustrations and visual aids, organizations can fortify their educational and strategic objectives, ensuring robust security measures are maintained across all operational facets.
—
Driving Security Innovation
In the ever-changing landscape of cybersecurity, maintaining a proactive approach to threat intelligence is imperative. Incorporating automation is more than just a technical improvement—it’s a commitment to driving security innovation and fostering an environment that’s resilient against current and emerging threats. The strategic deployment of cyber threat intelligence workflow automation offers organizations the means to harness comprehensive security intelligence, turning potential vulnerabilities into controlled and contingitable situations.
Automation is the launchpad that propels companies from mere reactive stances into proactive resilience. By leveraging it, security teams are empowered to anticipate, mitigate, and nullify threats with a level of efficiency that manual processes simply can’t match. It’s about crafting fortifications that not only withstand attacks but also outsmart the adversarial tactics lurking in the digital shadows.
A culture committed to employing forward-thinking technologies is one that thrives amid the chaos of cyber threats. As businesses continue to navigate these turbulent waters, the strategic use of cyber threat intelligence workflow automation stands as the beacon of security innovation—guiding the way to an era of unprecedented cybersecurity efficiency and effectiveness.