In today’s digital age, with the rapid evolution of technology and increasing reliance on digital platforms, the threat landscape is becoming more sophisticated. Cybersecurity is no longer a niche concern; it’s the backbone of safe, international connectivity. Companies and governments around the world are constantly innovating to stay ahead of cyber threats, and it’s here that cyber threat intelligence models come into the spotlight. These models are essential frameworks designed for understanding, predicting, and counteracting the multitude of ever-evolving cyber threats.
Read Now : Interconnecting Cloud And Chatbot Technologies
Imagine walking through a dense jungle without a guide, facing the invisible dangers lurking at every corner. Cyber threat intelligence models serve as that crucial guide for organizations, helping them navigate through the complex web of the internet with more safety and assurance. Utilizing advanced analytics and continuous scrutiny, these models curate significant data about potential threats, helping entities develop timely and efficient mitigation strategies. The stakes are undoubtedly high; a single data breach can result in millions of dollars in losses, impacting trust, brand reputation, and operational continuity.
To emphasize their importance, consider the emotional toll and the palpable apprehension when an organization discovers a cyber intrusion. It’s akin to a suspense thriller unfolding, where the bad actors are unidentified, yet their effects are visibly damaging. Cyber threat intelligence models act as the unsung heroes, a clandestine task force that works to publish a detailed script of possible threat scenarios, thus enabling organizations to prepare and strategize well in advance. The more one knows the enemy, the better one can combat it—this ancient principle finds a modern avatar in cyber threat intelligence models.
How Cyber Threat Intelligence Models Enhance Security
The relevance of cyber threat intelligence models is indisputable in the modern security landscape, offering a structured approach to threat analysis. Imagine a bustling city protected by unseen forces ensuring the safety of its inhabitants. These models dissect complex data, turning chaos into actionable insights, thus reinforcing cyber defenses. They identify potential attackers, their motives, and methods, drawing a comprehensive picture that empowers organizations to build robust strategies and safeguard their assets.
The beauty of these models lies in their versatility and adaptability. They’re not just tools for big corporations but are scalable solutions for businesses of all sizes. With evolving digital threats, there’s a pressing need for continuous learning and adaptation, driven by these models. As technology progresses, cybercriminals devise ingenious ways to infiltrate systems and manipulate vulnerabilities. Cyber threat intelligence models don’t just keep pace—they strive to stay a step ahead, pre-empting moves similar to an adept chess player predicting an opponent’s game.
Moreover, the role of cyber threat intelligence models extends beyond mere protection. They’re akin to detectives piecing together evidence to prevent future crimes. By analyzing patterns and anomalies, they anticipate potential breaches, suggesting preventive measures. This foresight is a priceless advantage in a world where data is as valuable as gold. Companies that leverage these models transform threat data into actionable intelligence, making informed decisions, minimizing risks, and ensuring the sanctity of their digital environment.
The modern organizational approach must embrace these models for comprehensive security architecture. The consequences of cyberattacks—financial, reputational, and operational—underscore the need for effective models. Through a combination of innovative analytics, community sharing, and precise threat detection, these models create a shield that translates complex data into comprehensible defense strategies. Ultimately, they illuminate the path to a safer digital future for any business or institution willing to invest in their potential.
—
Structure and Importance of Cyber Threat Intelligence Models
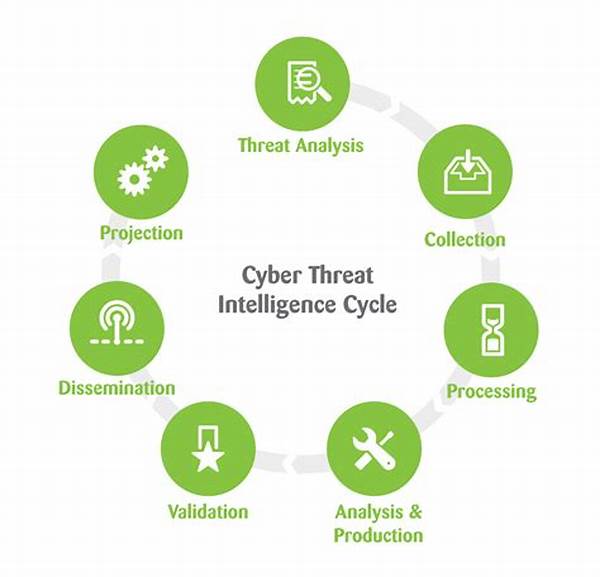
Cyber threat intelligence models are critical in providing structured frameworks for threat identification, analysis, and remediation. They operate by gathering vast amounts of data from various sources, such as open-source information, dark web activities, and even internal systems. By synthesizing this data, these models allow organizations to discern patterns and predict potential threats, offering a proactive rather than reactive approach to cybersecurity.
Components of Cyber Threat Intelligence Models
In order to fully harness the power of cyber threat intelligence models, one must understand their core components. Typically, these models comprise data collection, threat analysis, decision-making processes, and feedback loops. Each component plays a pivotal role in ensuring a comprehensive and cohesive threat-intelligence system.
—
- Utilize Threat Intelligence Platforms: Implement advanced platforms to manage and analyze threat data efficiently.
- Conduct Regular Threat Assessments: Schedule frequent assessments to update security measures and protocols.
- Collaborate with Cybersecurity Community: Engage with other organizations to share intelligence for collective threat preparedness.
- Invest in Employee Training: Educate employees about cyber threats to enhance overall organizational security.
- Leverage AI and Machine Learning: Use AI-driven tools for more accurate threat prediction and detection.
The landscape of cybersecurity is ever-expanding, demanding vigilance and innovation. One of the most remarkable developments in this field has been the emergence of cyber threat intelligence models. At its core, these models are crafted to enhance the preventive capabilities of an organization’s cybersecurity strategy, acting as a crystal ball in the cybersecurity realm. By turning threat data into valuable intelligence, they help foresee potential cyber threats before they can cause irreparable damage.
With the acronyms and buzzwords thrown around in discussions of cybersecurity, it’s easy for many to feel out of their depth. However, embracing cyber threat intelligence models can turn a complex web of data into actionable insights. These models synthesize various data points, providing organizations with a well-rounded understanding of potential threats. Think of them as the scout in a medieval army, always ahead of the battalion, aware of possible threats and challenges.
The application of these models is vast. They aren’t confined to major corporations; small businesses, institutions, and even individuals benefit from their predictive abilities. By leveraging the model’s insights, organizations can create tailored defense mechanisms, minimizing vulnerabilities and enhancing their resilience. In a fast-paced digital world, understanding threats and acting swiftly is imperative, and these models offer that much-needed edge.
Read Now : Legal Risk Management With Ai
In conclusion, as cyber threats continue to evolve, the need for a structured approach like cyber threat intelligence models becomes critical. By illuminating potential challenges and offering solutions proactively, they ensure that organizations don’t merely react to threats but anticipate them. This strategic foresight is invaluable in preserving data integrity, protecting operational continuity, and maintaining public trust.
—
Key Features of Cyber Threat Intelligence Models
- Data-Driven Insight: Aggregating and analyzing vast data streams to glean actionable intelligence.
- Predictive Analytics: Using historical and current data to anticipate future threats.
- Cross-Industry Collaboration: Sharing information across sectors to bolster collective defense.
- Flexibility and Scalability: Adapting to organizations of all sizes and industries.
- Continuous Learning: Updating intelligence models based on emerging threats.
- Automated Threat Detection: Employing AI and machine learning for real-time threat identification.
- Human Expertise Integration: Combining automated tools with expert analysis for holistic security.
Cyber threat intelligence models are acclaimed for their comprehensive approach to combating cyber risks. They offer data-driven insights, blending historical and real-time threat data to provide organizations with accurate and timely intelligence. This predictive prowess is akin to having a security guard with heightened senses, constantly scanning for anything amiss. By foreseeing cyber threats, organizations can avert disastrous intrusions, maintaining operational continuity and safeguarding valuable assets.
The beauty of these models is their adaptability. Regardless of the organization’s size or industry, they provide scalable solutions tailored to meet specific needs. Their versatility extends to various sectors, ensuring collective security through cross-industry collaboration. Sharing insights enhances the models’ efficacy, fostering a unified defense mechanism among businesses and educational institutions, governments, and NGOs alike.
Moreover, they integrate seamlessly with modern technology, using AI and machine learning for automated threat detection. This rapid-response capability ensures that potential risks are mitigated before they materialize. Yet, the human element remains integral; these models are designed to work alongside cybersecurity experts, blending artificial intelligence with human intuition for a holistic approach to security. In a world where threats loom large, cyber threat intelligence models stand as formidable defenders, offering peace of mind to businesses of all scales.
—
Exploring the Dynamics of Cyber Threat Intelligence Models
Cyber threat intelligence models are indispensable tools in today’s cybersecurity landscape. They provide the structured frameworks necessary for analyzing, identifying, and mitigating potential threats before such threats can manifest into devastating attacks. The intelligence gathered is not just data—it is actionable insight that allows organizations to protect their most valuable assets, from sensitive data to capital resources.
The Interplay of Technology and Expertise
Cyber threat intelligence models operate at the intersection of cutting-edge technology and human expertise. Through a combination of AI-driven data analysis and the nuanced understanding of cybersecurity experts, these models can process vast volumes of data, identify anomalies, and forecast potential threats with a high degree of accuracy. There’s a certain elegance in how these models bring together automated precision with seasoned insight, creating a robust defense against the myriad cyber risks modern organizations face.
The Future of Cyber Threat Intelligence Models
Looking ahead, the evolution of cyber threat intelligence models promises even greater efficiency and effectiveness. As technology advances, so too will the sophistication of these models. They’re expected to integrate deeper with AI and machine learning, continuously learning and adapting to new threat landscapes. This proactive evolution ensures that these models will remain at the forefront of cybersecurity, providing a dependable shield against evolving cyber threats. Organizations of all sizes must recognize the essential role these models play in safeguarding their digital futures and invest accordingly.
In conclusion, cyber threat intelligence models are not merely tools but strategic allies in an organization’s battle to secure its digital infrastructure. By leveraging the power of technology and human expertise, they transform raw data into strategic insights, allowing proactive defense against cyber threats—a necessity in today’s digital age.