H1: Cyber Threat Intelligence Automation
In a world that is increasingly driven by technology, the threat landscape is evolving at an unprecedented pace. Cybersecurity is no longer just an IT issue; it has ascended to boardroom agendas as organizations recognize the critical need to protect valuable assets. Enter “cyber threat intelligence automation”—a revolutionary approach that combines cutting-edge technology with strategic intelligence to proactively identify and mitigate cyber threats. Picture this: an automated system that works tirelessly round the clock, analyzing vast amounts of data, predicting potential threats, and neutralizing them before they become a menace. Intrigued yet? Well, hold on, because this is just the tip of the cybersecurity iceberg.
To put the power of cyber threat intelligence automation into perspective, we must first acknowledge the staggering amounts of data that security teams face. It’s like finding a needle in a haystack, with cybercriminals constantly sharpening their tools. Manually sifting through this data for potential vulnerabilities or threats is akin to chasing shadows in the dark—a daunting and often fruitless endeavor. But with automation, the needle practically jumps out of the haystack, demanding your attention. This technology allows organizations to focus on fortifying defenses rather than getting bogged down in the data deluge. It’s like having a dedicated detective on your team, one that never sleeps, never tires, and always gets the job done.
Cyber threat intelligence automation doesn’t just react to threats—it anticipates them. Imagine having the foresight to prevent a crime before it even happens. While cybersecurity systems were once primarily reactive, automation empowers them with a proactive edge. It provides actionable insights derived from analyzing patterns and trends, giving organizations the upper hand against cyber adversaries. The world of cyber threat intelligence automation is not just about protecting data; it’s about creating a resilient digital ecosystem. It’s about turning the tide and evolving from being mere spectators to becoming empowered protectors.
H2: The Power of Predictive Defense
Fast forward to a future where cyber attacks are thwarted before they even emerge, thanks to cyber threat intelligence automation. Exciting, right? This reactive shift in defense strategy is making waves in the cybersecurity landscape, changing the game from defense to prevention. Organizations that leverage this technology aren’t just protecting themselves—they’re setting a standard. They showcase a commitment to security, innovation, and forward-thinking, positioning themselves as leaders in a data-driven world. Businesses are no longer passively waiting for security breaches; they are actively averting them through a meticulously automated defense mechanism.
—Cyber Threat Intelligence Automation: Unlocking the Future of Cyber Defense
In today’s digital age, the mention of cybersecurity conjures images of tech-savvy criminals and elusive hackers creating havoc at the click of a button. With every technological advancement, the potential for cyber threats grows exponentially. Now, more than ever, organizations are turning to advanced solutions such as “cyber threat intelligence automation” to safeguard their assets. This transformative tool is not just a game-changer; it’s more like your digital guardian angel, with an eagle-eyed focus on threats that lurk in the cyber shadows.
H2: Understanding the Basics of Cyber Threat Intelligence
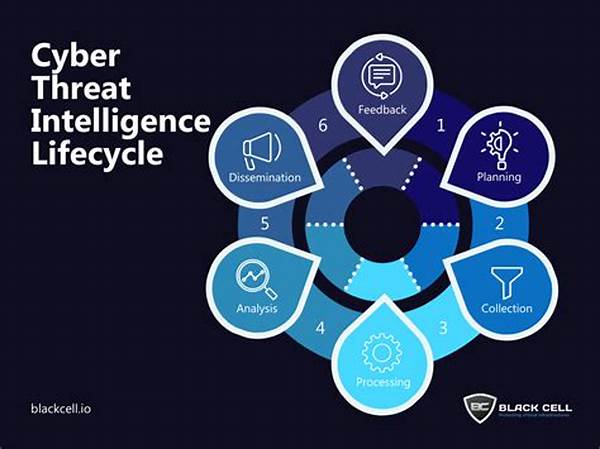
Cyber threat intelligence (CTI) is essentially the process of collecting and managing information about current and future cyber threats. It involves carefully analyzing data to understand the threat environment, providing the insights necessary to make informed security decisions. The primary goal of CTI is to prevent data breaches and mitigate risks, making it a critical component of modern cybersecurity strategies. And when automation is infused into the CTI framework, its potential turbocharges. Imagine replacing hours of manual threat assessments with an automated system that never misses a beat.
H3: Why Automate? A Case for Efficiency
The decision to automate threat intelligence processes lies in the sheer efficiency that automation brings. Cyber threat intelligence automation ensures that no stone is left unturned—it meticulously analyzes every blip and glitch across vast data streams, producing intelligence richer and faster than any human could. The eleventh hour becomes a thing of the past because automation doesn’t wait for the threat to escalate. It addresses challenges head-on and in real-time, acting like a seasoned chess master who anticipates the opponent’s moves long before they’re made.
Automation elevates cybersecurity from reactive defense into proactive offense. Sophisticated algorithms and machine learning systems work round the clock, transforming raw data into actionable insights. Cyber professionals can now focus on strategic decision-making, harnessing the power of curated intelligence provided by automated systems. The result? A remarkable improvement in threat detection, response times, and overall cybersecurity posture.
Benefits of Cyber Threat Intelligence Automation
—Empowering Cyber Defense with Intelligence and Automation
The marriage of intelligence and automation in the cybersecurity realm is like a dynamic duo orchestrating the ultimate defense opera. This new era of cyber defense unravels unprecedented potential, instilled with wisdom drawn from the past and the predictive prowess of artificial intelligence. Cyber threat intelligence automation encompasses data collection, threat analysis, and the automated distribution of relevant alerts and notifications. It’s the full package that empowers cybersecurity teams to evolve from mere cyber sentinels to highly strategic cyber warriors.
H2: The Role of Automation in Modern Cybersecurity
Automation in cybersecurity is more than just a tool—it’s a strategic necessity. With increasing volumes and complexities of threats, the human factor alone cannot suffice in ensuring optimal protection. Cyber threat intelligence automation comes as a revolution, addressing the perennial challenges crippling many security operations centers. It efficiently identifies threats by dissecting and analyzing large datasets, which would otherwise be overwhelming through manual labor alone.
As businesses expand globally and adopt multi-cloud environments, the complexity of cybersecurity increases. Threat landscapes shift and mutate rapidly, demanding an agile response system capable of evolving just as swiftly. Automation is essential to navigate these evolving threats and deliver precision in identification, mitigation, and response strategies.
The Automation Journey: Challenges and Possibilities
Deploying cyber threat intelligence automation is not devoid of challenges. Integrating it into existing frameworks requires careful consideration and planning. Yet, the possibilities it unlocks are profound. It transcends conventional approaches, providing unparalleled insights and amplifying organizational resilience against evolving threats. With steady progress and technological advancements, overcoming these challenges leads to automation’s seamless integration into modern cybersecurity arsenals, reaping its countless rewards.
Cybersecurity automation’s ripple effect extends beyond IT departments, invoking a transformative phase in organizational culture. It encourages a proactive security stance, infusing confidence among stakeholders and enhancing overall trust in business operations. As more entities embrace this change, it fosters a secure and resilient digital environment, positioning businesses to thrive in an era defined by technological prowess and innovation.
Illustrations of Cyber Threat Intelligence Automation
The dawn of cyber threat intelligence automation has heralded a refreshing perspective on monitoring and guarding against cyber threats. To envisage its profound impact, consider how these illustrations streamline existing processes, rendering them more efficient and effective in the long haul.
A New Era of Cybersecurity Awaits
With such connectivity comes responsibility—and a degree of vulnerability. The introduction of cyber threat intelligence automation is indeed the knight in shining armor in today’s high-stakes cyberspace. It is the definitive tool that not only shores up our defense through advanced intelligence but also ensures we stay one step ahead of looming threats. As we plunge further into a digital future, embracing automation becomes an essential fortification, equipping organizations with the confidence to navigate the ever-evolving cyber terrain.