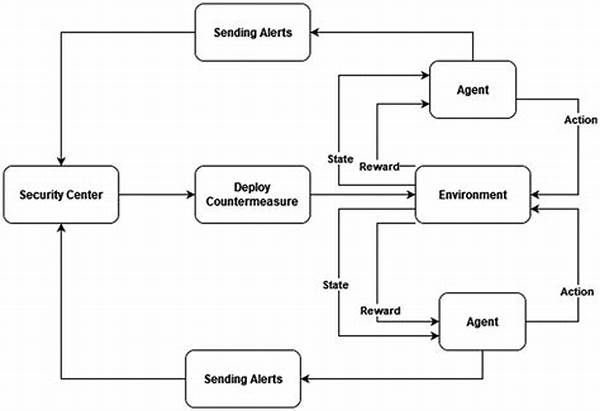
In today’s hyper-connected world, cyber threats are evolving at an alarming rate. Businesses, regardless of size, are faced with the daunting task of protecting their digital assets and sensitive information from cybercriminals. Cyber attacks can lead to significant financial loss, reputational damage, and operational disruption. It is not just antivirus software or firewalls that will save the day; what’s required is in-depth, comprehensive cyber defense reinforcement strategies. These strategies allow companies to prepare, respond, and recover from cyber incidents effectively.
Imagine waking up one morning to discover your business’s data has been compromised. The chaos, the sheer panic! Cybersecurity breaches lead not only to financial setbacks but also damage to your brand reputation that may take years to rebuild. With the right cyber defense reinforcement strategies, such nightmares can be prevented. From training employees about phishing scams to deploying advanced threat detection systems, the plan needs to be multifaceted. This not only entails the installation of security tools but also cultivating a cybersecurity-aware culture that empowers your workforce to become the first line of defense against cyber threats.
Incorporating these strategies into your organization isn’t simply about protecting today. It’s about laying the groundwork for a secure digital future. Here, we delve into detailed methodologies that can shield your business from cyber catastrophes, setting a robust foundation for trust and resilience.
Implementation of Cyber Defense Strategies
The cyber threat landscape is unpredictable, making it crucial for organizations to focus on the continuous assessment and enhancement of their cybersecurity measures. While the digital age offers extensive opportunities for innovation, it simultaneously poses risks that need proactive management. By emphasizing strong cyber defense reinforcement strategies, companies can navigate these challenges with confidence. Bridging technology and human elements is key to fortifying defenses against cyber adversaries.
—
The Essence of Cyber Defense Reinforcement Strategies
In the fast-paced digital world, businesses can no longer rely on traditional methods to tackle cybersecurity threats. Constant adaptation and reinforcement of strategies are necessary to stay ahead of cyber criminals who continuously devise new attack techniques. Cyber defense reinforcement strategies encompass a spectrum of measures aimed at bolstering an organization’s cyber resilience.
First and foremost, businesses must recognize the value of employee awareness and training. Cybersecurity isn’t just an IT issue; it’s a company-wide concern. Employees are often the first line of defense, and equipping them with the knowledge to identify and report threats can drastically reduce the risk of breaches. Through interactive training sessions and simulated phishing attacks, organizations can cultivate a vigilant workforce that plays an active role in safeguarding critical data.
Another integral component of cyber defense reinforcement strategies is the deployment of cutting-edge technology. The implementation of AI-driven threat detection and response systems allows businesses to automatically identify and mitigate threats in real-time. Additionally, regular audits and penetration testing aid in identifying vulnerabilities, providing invaluable insights to fortify defenses. Ensuring that all software and systems are up-to-date with the latest security patches is a fundamental yet often overlooked measure in the defense strategy.
Key Features of Effective Cyber Defense
Recognizing the importance of cyber defense reinforcement strategies is crucial. By leveraging advanced tools and fostering a security-conscious culture, businesses can transform potential vulnerabilities into strong points of defense, ensuring the safety of their digital assets and maintaining trust with clients and stakeholders.
—
Exploring the Sphere of Cyber Defense
As cyber threats loom large over digital ecosystems, defense mechanisms must evolve in tandem. Cyber defense reinforcement strategies form the backbone of an organization’s cybersecurity infrastructure by focusing on the prevention, detection, and response to malicious activities. These strategies are not static; they must be continuously refined to address emerging threats.
A key aspect of these strategies is fostering collaboration. By encouraging open communication between IT experts, employees, and management, an organization can cultivate a unified front against potential cyber incidents. Furthermore, establishing partnerships with cybersecurity vendors and participating in industry forums grant access to real-time intelligence and best practices that can be instrumental in combating hyper-evolving cyber threats.
Additionally, adopting a “Zero Trust” policy complements traditional cybersecurity measures. This model revolves around assuming that threats could come from both inside and outside the organization, thereby enforcing strict verification for every access request. By integrating zero trust principles into everyday operations, companies can create impregnable defenses that are adaptive to new cyber landscapes.
A Closer Look at Technological Innovations
Staying at the forefront of technology can be a game-changer in the realm of cyber defense reinforcement strategies. The integration of machine learning and AI is revolutionizing how businesses manage and respond to threats. Unlike traditional anti-virus software, these systems learn from patterns and behaviors, allowing them to anticipate and counteract attacks before they infiltrate the system. This predictive capability renders them indispensable allies in the pursuit of cybersecurity.
Moreover, cloud security has become an integral part of cyber defense strategies, with more businesses transitioning to cloud-based solutions. Employing a robust cloud security framework not only ensures data safety but also enables scalable, real-time threat monitoring. Businesses must invest in cloud services designed with security at their core to better protect sensitive data.
In conclusion, the necessity to implement dynamic cyber defense reinforcement strategies has never been more pressing. By intelligently blending human vigilance and advanced technology, businesses can create a stronghold that protects against the ever-present threat of cyber adversaries. Such proactive measures promise not just security but also the continuity and success of any digital enterprise.
—
Tips to Enhance Your Cyber Defense
Strengthening your cyber defense posture requires a multi-faceted approach, as illustrated by the array of strategies discussed. Nowadays, the digital frontier demands nothing short of robust, innovative, and adaptive measures to outsmart cyber adversaries. Businesses must prioritize their cyber defense reinforcement strategies, not only to protect critical assets but to thrive in an increasingly interconnected world. Embracing a proactive and comprehensive defense plan today ensures resilience and success in the face of future cyber challenges.
—
Comprehensive Cybersecurity Tactics
As the digital era surges forward at an unprecedented pace, so too do the threats lurking in cyberspace. Cyber defense reinforcement strategies are the cornerstone of any robust cybersecurity program, ensuring that organizations can not only protect sensitive data but also safeguard their reputation and operational efficiency. The effectiveness of these strategies hinges on how well they address both technological and human aspects of security.
For a robust cybersecurity framework, companies must prioritize continuous training and education. Employees are the lifelines of any organization, often serving as the first bulwark against cyber threats. By conducting regular workshops, seminars, and cybersecurity drills, businesses can keep their teams informed and adept at recognizing phishing attempts and other malicious activities. Gamified training approaches, such as cybersecurity escape rooms, can offer an engaging and memorable learning experience, fostering a culture of vigilance across the organization.
Implementing sophisticated cybersecurity technologies is equally important. Advanced threat detection systems that incorporate machine learning and AI can sift through massive amounts of data to pinpoint anomalies indicative of potential threats. This proactive approach enables companies to fend off cyberattacks before they can cause harm. Moreover, integrating these technologies with existing IT infrastructure can enhance visibility and control over network traffic, mitigating risks from external and internal sources.
The Role of Collaboration
Collaboration is often overlooked but is a vital element of cyber defense reinforcement strategies. In a world where threats are becoming increasingly complex and international, no organization can afford to operate in isolation. Cybersecurity alliances and information-sharing networks enable companies to stay ahead of emerging threats by pooling resources and expertise. Engaging in collaborative cybersecurity efforts not only strengthens defenses but also fosters trust and cooperation across industries.
Furthermore, partnering with reputable cybersecurity vendors can bring heightened vigilance and specialty services into play. These partnerships allow organizations to tap into specialized expertise and cutting-edge technologies that may otherwise be out of reach. By leveraging external capabilities alongside in-house skills, companies can customize their defense strategies to more accurately reflect their unique threat landscape.
Embracing a Proactive Stance
One crucial aspect of successful cyber defense reinforcement strategies is the shift from a reactive to a proactive stance. In an era where data breaches often make headlines, organizations cannot afford to wait and see. Proactivity involves ongoing risk assessments, security posture evaluations, and a readiness to adapt strategies as new threats arise. Regular reviews and updates to security policies ensure that they remain relevant and effective amidst shifting threats.
To be proactive, businesses should also invest in a comprehensive incident response plan. Such a plan outlines specific actions to be taken in the event of a breach, minimizing damage and ensuring a swift return to stability. Regularly testing this plan through simulations and mock drills can refine procedures, ensuring that when an actual threat arises, the response is not only prompt but also efficient.
—
By focusing on diverse aspects of cyber defense reinforcement strategies, organizations not only protect their own assets but contribute towards a safer digital landscape globally. As cyber threats continue to evolve, the adaptability and comprehensiveness of these strategies will determine a company’s ability to face challenges and succeed in an interconnected era.