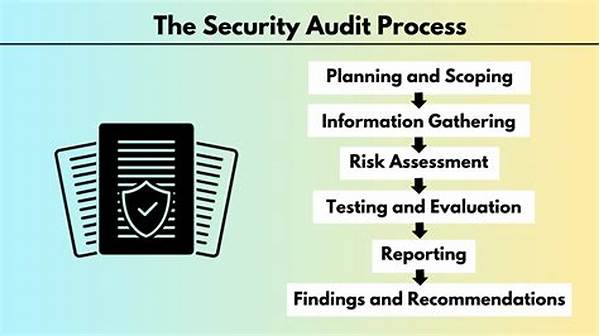
H1: Comprehensive Security Auditing Processes
In the digital age, the safety and security of information are paramount. With the ever-increasing sophistication of cyber-attacks, organizations can no longer afford to overlook weak spots in their systems. Enter comprehensive security auditing processes—an essential practice to ensure your data remains secure and your systems robust against potential breaches. Imagine a world where your business operations are constantly monitored and safeguarded. Doesn’t that sound like a weight lifted off your shoulders? That’s the promise comprehensive security auditing processes deliver. They are not just about identifying vulnerabilities but about transforming systems into fortified fortresses.
The journey of securing an organization begins with recognizing the latent vulnerabilities sprawled across various components of an IT infrastructure. Comprehensive security auditing processes delve into these vulnerabilities, offering a detailed analysis of potential risks. For many companies, understanding the importance of these audits can be the difference between proactive protection and reactive damage control. When implemented correctly, these processes provide an exhaustive blueprint of security weaknesses, guiding organizations in strengthening their defenses.
The magic of comprehensive security auditing processes is in their ability to adapt and evolve. With every technological advancement, they reinvent methodologies, ensuring that they address emerging threats in real-time. Businesses today must perennially tighten their grips on cybersecurity. But it’s not just about protection—it’s about trust. Clients and stakeholders expect their data to be in safe hands, and these processes serve as a testament to an organization’s commitment to securing sensitive information. They create an environment where stakeholders feel secure, thus bolstering business reputations and client relationships.
In an era where data is as precious as gold, comprehensive security auditing processes are not just services—they are investments. They keep you two steps ahead of cyber culprits, allowing you to conduct business without the omnipresent fear of breach. So, if peace of mind and business continuity are on your priority list, consider security audits as your loyal guardians. As they say in the cybersecurity realm, it’s always better to be safe than sorry. This could not be truer when it comes to protecting digital assets. Comprehensive security auditing processes offer that safety net, ensuring your operations are always one step ahead.
H2: The Importance of Security Audits in a Digital World—
Introducing Comprehensive Security Auditing Processes
In today’s fast-paced digital era, organizations face increasingly sophisticated cybersecurity threats. Understanding and implementing comprehensive security auditing processes are now more crucial than ever. These audits aren’t just mere checklists. They serve as an investigative journey into the heart of an organization’s IT framework, uncovering potential vulnerabilities that could compromise data integrity and security. At first glance, it might seem overwhelming, but that’s where the magic lies. These processes act as both magnifying glass and shield, meticulously examining each layer of your infrastructure while fortifying it against potential threats.
Security audits provide a unique selling proposition for businesses craving peace of mind. Imagine knowing that your customers’ sensitive information remains protected, even against the most cunning cyber adversaries. With comprehensive security auditing processes, organizations can exude an air of trustworthiness, enticing more clients and stakeholders with their unequivocal commitment to data safety. After all, security is not just about locking doors—it’s about reassuring those who trust you with their data.
H2: Key Components of Security Auditing
Unlike traditional methods that don’t hold up against today’s advanced threats, comprehensive security auditing processes incorporate several critical components. First, they foster a culture of awareness, ensuring all staff members understand the importance of cybersecurity. When each team member is vigilant, the overall security posture of the company strengthens. Second, these audits embrace a systematic approach, ensuring no stone is left unturned. They involve a detailed assessment of an organization’s security controls, identifying weak points that could be exploited by cybercriminals.
But it’s not just about the technical aspects. Security audits also delve into compliance with regulatory standards. As regulations tighten globally, ensuring adherence becomes critical to avoid hefty fines. Comprehensive security auditing processes don’t just help you comply—they guide you through the maze of regulatory requirements, providing an edge over competitors who struggle to keep up. This multifaceted approach underscores why these audits are not just an operational procedure but a strategic necessity.
H3: Why You Shouldn’t Ignore Security Audits
Dismissing the need for comprehensive security auditing processes could spell disaster. With cyber threats evolving at an unprecedented pace, relying on outdated security measures equates to welcoming breaches with open arms. Consider the tangible and intangible costs of a data breach—financial losses, reputational damage, and client distrust can cripple even the mightiest of organizations. Implementing regular security audits can act as a preventive measure, ensuring potential issues are addressed before leading to catastrophic outcomes.
The power of comprehensive security auditing processes lies in their adaptability and foresight. They are designed to anticipate and respond to emerging threats, ensuring your operations remain uninterrupted. Imagine running a marathon without preparing—you’re bound to falter. Similarly, navigating the digital landscape without the safety net of security audits is a risky endeavor. Don’t just take my word for it; industry leaders prioritize and vouch for the effectiveness of these audits in fortifying their systems and enhancing client trust. By integrating comprehensive security auditing processes, you’re not just enhancing security; you’re building a legacy of trust, innovation, and resilience.
—
Exploring Comprehensive Security Auditing Processes
Introduction
In an era dominated by technology, ensuring the security of digital assets has become a non-negotiable priority. Comprehensive security auditing processes offer a beacon of hope, guiding organizations through the dense forest of cybersecurity threats. Engineered to unmask vulnerabilities, these audits are not just tools—they’re companions in your cybersecurity journey. Let’s face it: no one wants to be the star of a “data breach” headline. Adopting comprehensive security auditing processes can keep you well ahead of cybercriminals, allowing you to bask in the glory of uninterrupted business success.
Seeing security breaches skyrocket isn’t just a concern; it’s a wake-up call. Organizations that underestimate their vulnerabilities are akin to leaving their digital doors wide open for cyber thieves. Comprehensive security auditing processes act like a security system, equipped with alarms and motion sensors, alerting you before the threat can proliferate. They offer an unmatched level of scrutiny, meticulously investigating every nook and cranny of your IT systems.
H2: Critical Aspects of Security Auditing
In an industry where changes are constant, comprehensive security auditing processes stand out as a hallmark of adaptability. They are intricately designed to transcend traditional boundaries, evolving in tandem with the threats they face. Unlike obsolete methods that fail to catch up, these audits are always a step ahead, ready and poised to thwart any unforeseen cyber onslaught. By embracing technological advancements and regulatory updates, comprehensive security auditing processes ensure that your fortress remains impenetrable.
H3: Testimonials from Industry Leaders
Prominent businesses worldwide swear by the efficacy of comprehensive security auditing processes. Don’t just take our word for it—revel in the endorsements from top-tier companies that have fortified their defenses through these strategic audits. “Since adopting regular security audits, our vulnerability reports have dwindled immensely,” notes the CTO of a renowned tech firm. Such testimonials resonate with authenticity, showcasing the transformative role audits play in securing an organization’s digital landscape. Let these success stories be the catalyst that propels you towards safeguarding your organization’s future.
—H2: Eight Essential Tips for Comprehensive Security Auditing Processes
Description
Navigating the intricacies of cybersecurity demands a strategic approach—enter comprehensive security auditing processes. These audits do more than spotlight vulnerabilities; they provide actionable insights and solutions. Imagine embarking on a voyage without a map. The risk of going astray is high. Similarly, operating without regular security audits can throw businesses into a tailspin of potential threats. By implementing these audits, organizations can illuminate hidden dangers and fortify their security measures.
In an ever-evolving digital landscape, relying on outdated practices is akin to navigating with a defunct compass. Comprehensive security auditing processes ensure you’re aligned with the latest in cybersecurity trends, shielding your organization from cyber predators. Their adaptability allows businesses to remain agile, preempting potential threats even before they materialize. But it’s not just about security; it’s about instilling confidence among stakeholders. By showcasing commitment to robust security measures, organizations bolster their reputation, attracting more clients and fostering trust.
Finally, adopting comprehensive security auditing processes is an investment in the sustainability of a business’s digital ecosystem. They serve as a harbinger of future-proof operations, ensuring business continuity amidst a backdrop of pervasive digital threats. Say goodbye to sleepless nights worrying about vulnerabilities, and embrace the peace of mind that comprehensive security auditing brings. With your digital realm secure, focus on what you do best—steering your business towards unparalleled success and stability.
—H2: The Future of Comprehensive Security Auditing ProcessesH3: Innovations and Strategies
As businesses grapple with the complexities of digital threats, comprehensive security auditing processes have risen as essential arbiters of cybersecurity. These processes are no longer optional—they are critical lifelines ensuring organizations remain insulated from cyber assaults. Picture this scenario: a hidden vulnerability lurks within your IT system, ready to wreak havoc. Without regular auditing, it sneaks by unnoticed, lying in wait for the opportune moment to strike. But with comprehensive security auditing processes, such threats are identified and neutralized with precision, safeguarding your operations and reputation.
These processes excel in tailoring solutions to unique business needs. They are an amalgamation of cutting-edge technology and strategic foresight, ensuring each audit delves deep into the specifics of an organization’s ecosystem. It’s like having a customized defense mechanism that’s agile, versatile, and ever-vigilant. The era of one-size-fits-all security solutions is over; now, it’s about dynamic defenses that mirror the complexities of modern threats.
Innovations in security auditing have revolutionized the way organizations perceive cybersecurity. New technologies, such as AI-driven analytics and machine learning, significantly enhance the efficacy of audits, allowing for real-time threat detection and mitigation. By incorporating these technologies, comprehensive security auditing processes become formidable defenders, capable of outpacing even the most complex cyber adversaries. It’s as if these processes have transitioned from static barriers to intelligent digests, constantly learning and adapting to provide unmatched protection.
In conclusion, embracing comprehensive security auditing processes isn’t merely a choice—it’s a necessity. As digital threats become more sophisticated, businesses must rise to the occasion, arming themselves with the best defense mechanisms available. By adopting these robust auditing processes, organizations not only secure their digital assets but also pave the way for a resilient, reputable, and reliable future. The message is crystal clear: invest in comprehensive security auditing processes now, and safeguard your legacy against the relentless tide of cyber threats.