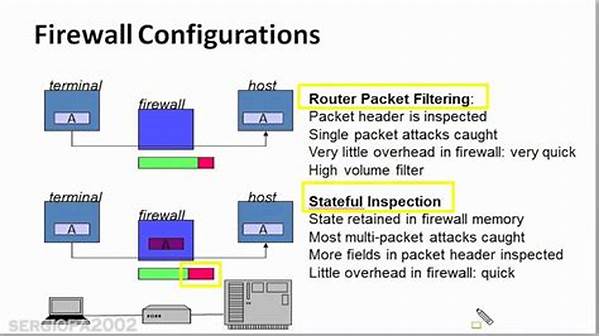
In today’s digital age, protecting our digital fortress with impeccable security measures isn’t just a fancy add-on—it’s a necessity. Imagine your network as a bustling fortress with countless entry gates; now picture these gates guarded not by medieval soldiers but by a vigilant firewall. It’s your knight in shining armor, your guardian of data and defender against cyber adversaries. But, like any good knight, your firewall requires regular maintenance and checks to remain formidable. Welcome to the pivotal “checklist for basic firewall security settings,” your blueprint for invulnerable digital security.
A staggering number of businesses have fallen prey to cyber-attacks simply because minor firewall settings were overlooked. It’s like forgetting to lock one door but securing all others, giving adversaries the opportunity to wreak havoc. This is not just a technical oversight; it’s a direct call to action for IT personnel and business leaders alike to embrace the discipline of regular and thorough inspections. The epitome of effective cybersecurity starts here, with a checklist that ensures no digital doorway is left unattended. From blocking unsolicited traffic to permitting secure passage, each setting is a piece of a larger puzzle designed to protect and preserve.
Don’t let the complexity of security settings daunt you. Think of it as mastering a game where victory belongs to those who strategize effectively. With a checklist in hand, the game of cybersecurity isn’t just winnable—it’s conquerable. Strengthen your defenses, adapt to emerging threats, and rest easy knowing you’ve taken proactive steps in safeguarding your digital kingdom.
Why A Firewall Checklist Matters
Every IT professional worth their salt understands that a secure network requires constant vigilance. The reason “checklist for basic firewall security settings” holds monumental significance is due to its role as a guiding star in navigating the labyrinth of cybersecurity. Without it, IT teams would be akin to sailors charting their course without a compass.
—
Introduction to Firewall Security
In a world where digital threats lurk at every corner, the task of safeguarding sensitive data and maintaining robust cybersecurity seems daunting, yet imperative. For businesses and individuals alike, understanding the “checklist for basic firewall security settings” is the first step towards erecting formidable defenses. Imagine stepping into a high-tech fortress, with each gate armed and inspected, ensuring only legitimate visitors gain passage while hostile forces are kept at bay.
Keeping a vigilant watch on network access is no longer just the domain of tech wizards, but rather a fundamental necessity for everyone who values their digital footprint. The checklist becomes your personal tour guide, leading you through the intricate corridors of security settings, ensuring every button and switch is precisely where it ought to be. It’s not just a protocol; it’s a trusted companion on your path to cybersecurity enlightenment.
Embracing the checklist is akin to drafting a blueprint for an impregnable stronghold, built not with bricks and mortar but with algorithms and access controls. The intricate dance of configuring, maintaining, and updating these settings is both an art and a science, requiring dedication and precision.
Essentials of Firewall Configuration
Every system administrator knows that setting up a firewall isn’t a one-time task but an ongoing commitment. Complacency is the enemy of security—a lesson often learned the hard way. The checklist becomes a steadfast ally, a roadmap to ensure nothing slips through the cracks. With careful adherence, network breaches can become a thing of the past, and peace of mind a present reality.
A comprehensive checklist includes multiple aspects: updating firmware, configuring inbound and outbound rules, and conducting regular audits. Each step, while seemingly ordinary, builds towards an extraordinary goal—an unyielding defense against ever-evolving threats. It’s a narrative not just of prevention, but of proactive management and continuous improvement.
The Importance of Regular Updates
In the digital realm, the only constant is change, and in keeping pace with it lies the crux of firewall efficacy. Regular updates, once mere recommendations, are now pivotal commandments embedded within the checklist for basic firewall security settings. These updates stand as the guardians against vulnerabilities, patching gaps before they are exploited.
—
Key Takeaways for Firewall Security
—
The Importance of a Secure Checklist
Security in the digital age is not merely a feature—it’s a requisite, one that demands adherence to a “checklist for basic firewall security settings.” Imagine this checklist as an invisible shield, guarding your sensitive data from the ever-present cyber threats. The importance this checklist holds cannot be overstated, serving as the cornerstone of your digital defensive strategy, ensuring that every potential breach is thwarted before it even begins.
Awareness of firewall settings marks the confluence of technology and vigilance; it’s where human intent meets technological prowess. By diligently following the checklist, organizations transform potential vulnerabilities into verified securities. It’s an artisan’s craft recreated in the digital era, where every setting is meticulously adjusted and every rule diligently enforced. The checklist does more than guide; it instills confidence—a peace of mind knowing that proactive steps have been taken to secure the network, the digital equivalent of installing locks on every window and door.
Routine Maintenance for Optimal Performance
Regular maintenance of these settings maintains the health and efficacy of your firewall. Think of it as regular check-ups to ensure every cog in the security machine is functioning seamlessly. Through routine checks, potential issues are swiftly identified and rectified, maintaining an optimal line of defense. For businesses, it’s not just about protecting data—it’s safeguarding reputation and customer trust.
As digital landscapes evolve, so too must our strategies for protection. This necessitates rigorous adherence to the checklist for basic firewall security settings, ensuring all potential loopholes are sealed impeccably. And in this consistent monitoring lies our greatest defense against the malice of digital adversaries.
Proactive Defense Strategies
Implementing proactive strategies is an integral element of firewall management. The checklist serves as a vessel, channeling efforts towards proactive defense mechanisms rather than reactive resolutions. By enforcing policies and maintaining awareness of emerging threats, the checklist transforms from a mere security tool into an empowering guide safeguarding your digital ecosystem.
Firewall Configuration Tips
By focusing on these fundamental areas, the “checklist for basic firewall security settings” offers organizations the chance to transition from a state of vulnerability to one of vigilance and protection.
—
In summary, embedding the “checklist for basic firewall security settings” into your organizational protocol can catalyze major improvements in your digital security paradigm. By staying one step ahead, employing strategic configurations, regular updates, and comprehensive audits, businesses can create a resilient and secure digital landscape, ensuring that sensitive data remains protected from would-be intruders.