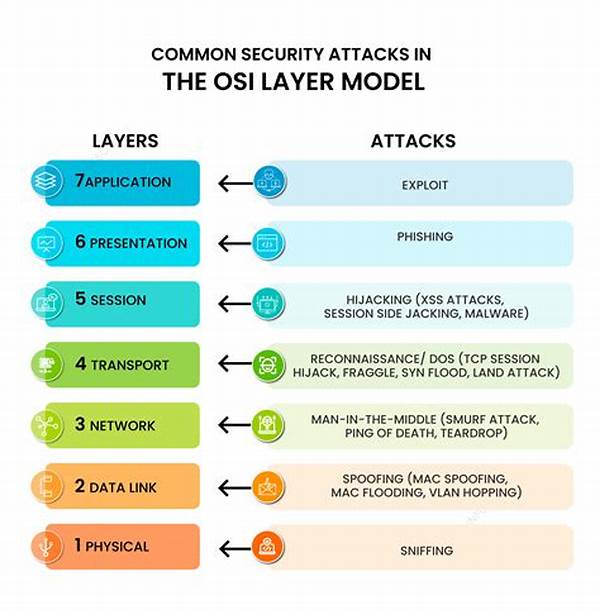
As we delve into the digital age, implementing layered security has become a buzzword in both tech forums and boardrooms. Imagine trying to safeguard your fortress while threats lurk like shadows, both seen and unseen—this is the reality that organizations face today. The term “layered security” might sound like a defensive strategy from a medieval battleground, but in the realm of cybersecurity, it’s a sophisticated, multi-faceted approach designed to protect data and infrastructure from evolving threats.
The crux of this idea is to set up multiple layers of security measures, each forming its own line of defense against cyberattacks. But why is this so crucial? Picture yourself in a film where the hero faces multiple challenges before reaching the climax; each obstacle is like a layer of security, delaying and weakening the antagonist. In our world, the antagonist is the cyber threat—be it malware, phishing, or a data breach. Yet, while the concept seems ironclad, the actual implementation of these layers can be fraught with difficulties.
Whether it’s integrating new systems with legacy architectures or ensuring compliance with ever-changing regulations, the challenges in implementing layered security are abundant and complex. Not to mention budget constraints—let’s face it, not all organizations can afford to deploy the most cutting-edge technologies in their security arsenal. As we unfold this narrative, let’s consider the technical, financial, and human hurdles which companies must scale to safeguard their digital domains.
The Challenges Unraveled
Given the rapidly evolving landscape of cybersecurity threats, the task of implementing layered security can often feel overwhelming. One major challenge is the seamless integration of multiple security solutions. Each layer must function harmoniously with the others, yet many organizations find themselves tangled in a web of disparate systems that refuse to gel together.
Moreover, there’s the perennial issue of keeping up with the sophistication of modern cyber threats. Hackers are like artists, perpetually refining their craft to outmaneuver the latest defenses. Organizations are in a perpetual race to update their security measures. Lastly, human factors cannot be ignored—from insider threats to skill shortages in the cybersecurity workforce; these human elements pose significant risks in the effectiveness of layered security strategies.
Navigating the Complexities
Layered security requires a strategic approach that involves meticulous planning and expert execution. Organizations must first conduct thorough assessments to understand potential vulnerabilities and the unique challenges of their respective industries. These initial steps demand concerted effort but will pay off by providing a solid framework upon which further security measures can be built.
Furthermore, organizations should consider partnering with cybersecurity experts who can offer nuanced insights and state-of-the-art solutions tailored to specific needs. Rising to the challenges in implementing layered security is not just a matter of employing technology but also of fostering a culture of security awareness within the organization. Empowering employees through training and establishing protocols for potential threats can significantly bolster the multi-layered defense shield, turning the challenge into an opportunity for resilience and growth.
—
Understanding the Components of Layered Security
A comprehensive layered security strategy involves a combination of technologies, processes, and employee training. Each component plays a vital role in strengthening the overall security posture.
Critical Areas to Focus On
Conclusion
Successfully navigating the challenges in implementing layered security can position organizations not only to safeguard their assets but to gain a competitive edge in the marketplace. By adopting a multi-layered defense approach with careful planning and execution, businesses can transform security challenges into opportunities for business resiliency.
—
By prioritizing a proactive approach to cybersecurity—one that includes rigorous training and state-of-the-art technologies—organizations can meet these challenges head-on. Not only will they defend against current threats, but they will also set a solid foundation to counteract future cyber adversities. With continual education, assessment, and adaptation, the seemingly daunting task of implementing layered security becomes a manageable and rewarding endeavor.