- Best Practices for Vulnerability Management
- Implementing Effective Vulnerability Management Strategies
- Introduction: The Growing Importance of Vulnerability Management
- The Intricacies of Managing Vulnerability
- In-Depth Understanding of Vulnerability Management
- Topics Related to Best Practices for Vulnerability Management
- Delving Into Advanced Vulnerability Management Strategies
- Continuous Improvement in Vulnerability Management
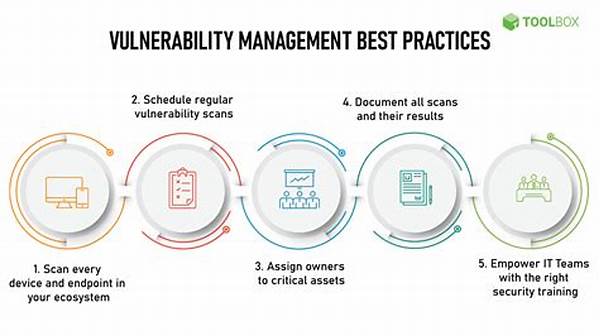
Best Practices for Vulnerability Management
In the digital age where every click can either build up a fortress or open a backdoor to your data, vulnerability management is akin to a knight guarding a kingdom. Picture this: A company bustling with innovation and creativity, producing technology that promises to reshape modern life. However, lurking in the digital shadows are vulnerabilities—unpatched software, glitches, or weak passwords—waiting to be exploited by cybercriminals. You don’t need to be battling dragons to recognize that safeguarding your digital assets is crucial. Welcome to the exciting world of vulnerability management, a strategic game where best practices are not just good guidelines but the very essence of survival!
Vulnerability management is not only about protecting your assets; it’s about maintaining client trust and upholding a reputation for resilience against cyber threats. A well-handled vulnerability means maintaining privacy, and often, avoiding monumental financial pitfalls. It’s providing the shield behind the exhilarating but perilous joust that is today’s digital communication. But what constitutes the best practices for vulnerability management that can allow a company not just to survive but thrive in this precarious environment?
Implementing best practices for vulnerability management involves a comprehensive, methodical approach. Start with proactive scanning, which enables organizations to identify vulnerabilities before they are exploited. Regular updates and patch management are also vital in ensuring the fortress walls remain unbreachable. With these tactics, your firm can maintain not just functionality and defense, but also the trust and loyalty of clients navigating this digital landscape.
Implementing Effective Vulnerability Management Strategies
Once the vulnerabilities are identified, prioritizing them based on the severity and potential impact is essential. This triaging allows organizations to allocate resources effectively, focusing on the most pressing threats first. Following this prioritization comes remediation, where the vulnerabilities are addressed and fixed. More than just a business imperative, this practice is a promise of security to your stakeholders, reassuring them that you are always a step ahead in safeguarding their interests.
—
Introduction: The Growing Importance of Vulnerability Management
In a world driven increasingly by complex systems and digital infrastructures, vulnerability management has surged in importance. Cyber-attacks have become more sophisticated, and as they do, the costs associated with breaches increase exponentially. Organizations today stand at a crossroads, where their integrity and success hinge on their capacity to identify, assess, and mitigate these vulnerabilities effectively. This makes understanding and applying best practices for vulnerability management not just an option, but a necessity for every business serious about safeguarding its future.
Vulnerability management is much like a meticulous game of chess. Each move requires foresight and strategy, where understanding your opponent’s potential moves can make the difference between success and vulnerability. The best practices for vulnerability management are crafted through lessons learned and the evolving landscape of cyber threats, much like a chess player refining their approach through countless matches played.
One might ask, what makes vulnerability management so critical today? Consider the increasing dependence on cloud computing and remote work environments, which have expanded the attack surface for cyber threats. Now, more than ever, the efficacy of a comprehensive vulnerability management program ensures that risks are mitigated and breaches are averted swiftly and smartly. Moreover, these practices are essential for compliance with regulatory requirements, which further underscores their significance.
Let’s delve deeper into understanding how one can implement best practices for vulnerability management to secure organizational infrastructure effectively. These practices not only enhance security postures but also demonstrate a commitment to technology stewardship, earning the trust of clients and partners alike. Equally essential is the aspect of continuous learning and adaptation—a practice integral to maintaining robust security measures over time.
The Intricacies of Managing Vulnerability
Implementing a successful vulnerability management plan requires a combination of technology, processes, and human expertise. A mixture of automated tools and human insight allows for a diligent approach, wherein vulnerabilities are managed regularly, consistently, and effectively. Best practices require keeping abreast of new vulnerabilities through industry bulletins, training sessions, and professional insights into emerging trends, making sure that no stone goes unturned in the defense of digital assets.
In-Depth Understanding of Vulnerability Management
Security culture is the cornerstone that supports the weight of comprehensive vulnerability management. Creating a culture that values security involves not only the right technology and protocols but also an organizational mindset where every member understands their role in the broader security picture. Making security awareness a staple part of training, and encouraging ongoing education about potential threats, peppered with real-world examples, can ensure that vulnerability management becomes second nature to every team member.
—
Topics Related to Best Practices for Vulnerability Management
Delving Into Advanced Vulnerability Management Strategies
In discussing best practices for vulnerability management, it’s crucial to understand that these strategies are not static. As the threat landscape evolves, so too must the methods we use to defend against it. Automated tools, machine learning, and artificial intelligence (AI) are transforming the way vulnerabilities are detected and managed. They enable organizations to advance from a reactive stance to a proactive one, identifying threats before they become crises.
Managing vulnerabilities effectively involves coordination across business units. IT departments are not solely responsible for securing an organization; rather, a culture of security must permeate every level of an organization. Bridging gaps between departments ensures everyone is aligned on security priorities and strategies.
Engaging external expertise can also be a game-changer in vulnerability management. Partnerships with security firms and regular penetration testing by third parties can unearth hidden vulnerabilities and offer new perspectives on how to address them. This provision of direct, action-oriented feedback allows organizations to bolster their defenses meaningfully.
Investment in robust, updated security solutions is imperative, but so is investing in people. Training employees to recognize phishing attempts and exposing them to simulated social engineering techniques can decrease an organization’s risk significantly. People are often the weakest link in the security chain, and empowering them with the right knowledge and tools is a critical defensive maneuver.
A culture that embraces change and innovation is one that can respond rapidly and effectively to the ever-evolving world of cyber threats. Continual learning and adaptation should be prioritized to build a resilient and responsive security foundation. This approach is not just about risk management; it’s a testament to an organization’s commitment to protect their data and that of their clients robustly and reliably.
Continuous Improvement in Vulnerability Management
Continual improvement in vulnerability management is paramount. Conducting regular reviews of past incidents and understanding where and how things went wrong can provide critical insights for future prevention. Documenting these learnings not only helps in refining existing processes but lays a knowledge foundation for new members joining the organization.
Organizations that treat vulnerability management as an ongoing, agile process, rather than a one-time project, are better equipped to handle future challenges. This dynamic approach ensures that they remain shielded in an unpredictable and ever-shifting technological landscape.