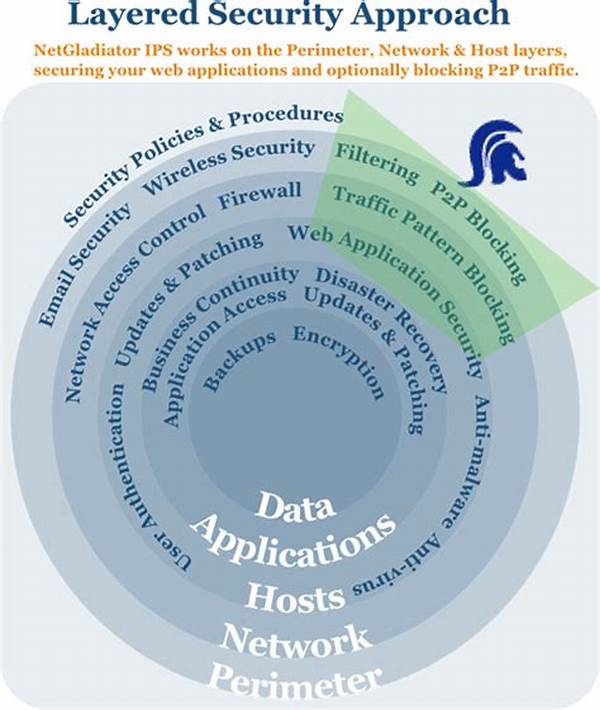
In today’s rapidly evolving digital landscape, security breaches remain a persistent and looming threat to businesses and individuals alike. Imagine waking up one day to find that your personal data has been compromised, or that your company’s sensitive information has been leaked to the public. This is not a distant possibility, but a reality that many have faced. Enter the layered security approach, a robust method designed to fend off such potential disasters by implementing multiple security measures at various levels.
At its core, the layered security approach, also known as defense in depth, is like a fortress with multiple levels of protection, akin to what you’d see in historical castles. Instead of relying on a single security solution, this approach stacks various methods one on top of the other. If one layer fails, others are there to keep you safe. From firewalls to antivirus and biometric authentication to encryption, this multifaceted strategy ensures that even if one gatekeeper falls asleep, there are others alert and ready to act. The unique selling point of this approach is its redundancy; it turns potential points of failure into reassurance.
Why is the layered security approach so compelling? For starters, it acknowledges the simple truth that no single solution can be wholly reliable in combating increasingly sophisticated cyber threats. In a world where hackers are growing more adept by the day, relying solely on antivirus software or a single firewall is as risky as sailing a ship without lifeboats. Therefore, businesses and savvy consumers alike should consider the benefits of layered security approach to safeguard their digital environments comprehensively.
Understanding the Benefits of Layered Security Approach
The first and foremost benefit of a layered security approach is enhanced protection. With multiple barriers in place, the likelihood of a single vulnerability being exploited is drastically reduced. Imagine a witty thief who somehow manages to crack the outermost door lock – they’re in for an unpleasant surprise when they encounter more locks, motion detectors, and perhaps a yappy digital watchdog. This layered defense strategy effectively deters intruders and increases the odds of detecting and neutralizing threats before they cause damage.
Moreover, by adopting this approach, your organization not only mitigates risk but also demonstrates a commitment to security that can elevate its market reputation. In today’s entangled web of networks, people want to know their data is safe. Businesses known for strong security practices often enjoy increased trust and loyalty from their customers. This isn’t just a feel-good story; it’s a tangible marketing strategy where benefits of layered security approach extend into profit margins as well.
Lastly, implementing a layered security approach offers flexibility and adaptability. As new threats emerge, additional layers can be incorporated and adapted as needed. If a newly discovered vulnerability arises, your team can address it at the specific layer required, minimizing disruption to the entire system. This flexibility makes the strategy both robust and agile, ensuring that your security measures are continually evolving to meet present and future threats.
—
Raising Awareness and Educating the Public
To understand the full benefits of layered security approach, public education is crucial. Much like a traffic system designed to reduce accidents, without public awareness and compliance, the system won’t function optimally. Educating employees, customers, and stakeholders about the importance and functionality of security layers not only enhances organizational safety but also empowers individuals to play an active role in maintaining their digital security. It emphasizes that this approach isn’t just for tech experts; it’s a collaborative effort to safeguard private information and assets.
Components and Their Synergy
Breaking down the layers, it’s essential to see how each component functions both independently and as part of an interconnected web of defense. From email filtering systems to robust password protocols and continuous network monitoring, each element contributes uniquely to the security posture. This synergistic operation ensures that potential breaches are caught at different stages, reflecting the diverse and ever-changing nature of cyber threats. Understanding these components further emphasizes the benefits of layered security approach in holistic protection.
The Road Ahead: Continuous Improvement
As technology evolves, so too must our approach to security. The benefits of layered security approach lie in its flexible nature—it’s not a set-it-and-forget-it solution, but an evolving strategy requiring regular updates and advancements. With cyber threats showing no signs of relenting, staying one step ahead means continually seeking improvements and innovations in security layers. By enacting continuous improvement practices, organizations can ensure they remain vigilant in the face of potential threats.
—