Automation in Vulnerability Management
In today’s fast-paced digital world, staying ahead of cyber threats requires more than just quick reflexes. Organizations are increasingly turning to automation in vulnerability management as a strategic approach to ensure their systems are secure, scalable, and resilient. Incorporating this technology isn’t just about protecting data; it’s about revolutionizing security protocols, streamlining processes, and ultimately saving time and resources. As businesses grapple with an ever-increasing number of vulnerabilities, automation allows IT teams to prioritize and tackle threats more efficiently. So, what makes automation in this context not only desirable but essential? Let’s dive deep.
Unlike traditional methods where vulnerability assessments are conducted periodically, automated systems provide continuous monitoring. This proactive approach drastically reduces the window of opportunity for cyber-attacks, making businesses less susceptible to breaches. Furthermore, automation minimizes human error – an often-overlooked factor accounting for a significant chunk of cybersecurity incidents. By streamlining tasks such as scanning, data analysis, and reporting, automation enables security teams to focus on more critical threats rather than being bogged down by mundane tasks.
Imagine a system that not only identifies weaknesses but also recommends remediation strategies in real-time. That’s precisely what automation in vulnerability management offers. The ability to integrate advanced analytics allows for more precise detection of threats and ensures that the most pertinent vulnerabilities are addressed first. With this enhanced decision-making capability, businesses can achieve a significant competitive edge while maintaining customer trust and regulatory compliance.
Moreover, in a world where resources are scarce, and expertise even more so, automation serves as a force multiplier. The ability to do more with less means that even small teams can have a significant impact. This democratization of security efforts ensures that companies of all sizes can maintain strong defenses without exorbitant costs. It’s not just a solution; it’s a revolution in how we approach cybersecurity.
Efficiency in Vulnerability Management
Moving towards efficiency in vulnerability management isn’t just a shift in tools but a revolution in mindset. As systems become more complex, the need for automation in vulnerability management becomes undeniable. Advanced technologies help organizations assess risks more accurately, prioritize threats, and respond effectively. The narrative of evolving alongside technology begins here, redefining how we guard digital realms.
—Structure Article
To fully grasp the significance of automation in the landscape of vulnerability management, we must delve into its building blocks. First, understanding how this process transforms typical vulnerability management is vital. Let’s break this down into a structured narrative that unveils what automation truly means for security.
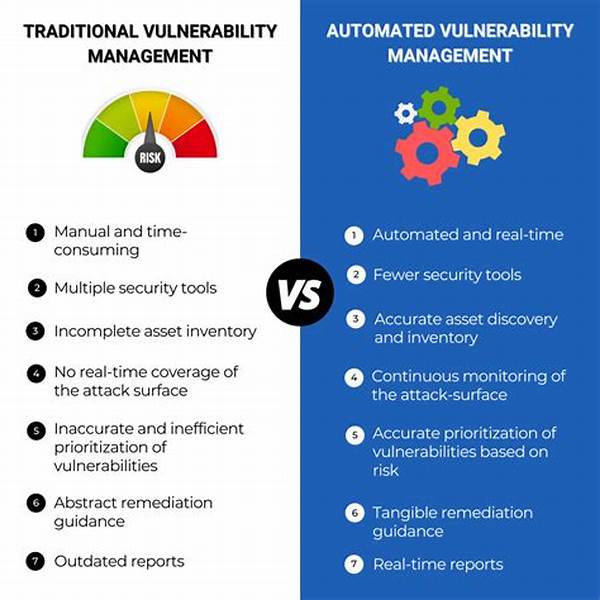
The Traditional Vulnerability Management Approach
Traditional vulnerability management was a labor-intensive and often reactive method. It involved manual scanning, triaging, and patching, which took a significant amount of time and resources. This approach left organizations vulnerable to zero-day exploits as they struggled to keep up with the ever-evolving threat landscape.
Transformative Power of Automation
Enter automation in vulnerability management. Automation allows for continuous scanning and real-time data analysis, significantly reducing the time between vulnerability discovery and remediation. This transformation repositions teams from reactivity to proactivity, allowing them to anticipate, prioritize, and rectify vulnerabilities before they can be exploited.
Benefits Beyond Security
While security is the priority, the benefits of automation extend beyond it. Efficiency gains mean faster turnaround times, improved compliance, and reduced operational costs. Automation provides a comprehensive view of vulnerabilities, enhancing risk management strategies and ensuring that resources are allocated to where they are needed most.
Overcoming Challenges with Automation
While automation significantly enhances security, its implementation is not without challenges. Customizing solutions to fit unique business environments and ensuring seamless integration with existing systems are common hurdles. However, once these challenges are addressed, the path to robust security is clear.
Adapting to the Future
An organization’s digital survival hinges on its ability to adapt and integrate new technologies. Automation in vulnerability management isn’t just the future; it’s the now. Organizations that embrace this technology prepare themselves for unforeseen threats, setting benchmarks in security efficiency and effectiveness.
Conclusion and Call to Action
In conclusion, embracing automation in vulnerability management is no longer optional; it’s essential. The advantages of rapid response, cost efficiency, and enhanced security are undeniable. For businesses yet to embark on this journey, the time is now. Integrate, adapt, and secure your future.
—Discussion: Exploring Automation in Vulnerability Management
The discussion around automation in vulnerability management isn’t just theoretical – it’s a necessity in our ever-evolving digital landscape. As cyber threats grow in number and sophistication, so too must our methods of combating them. Groundbreaking technologies have paved the way for an era where security processes are not only more efficient but also more effective. Companies can no longer afford to rely solely on human intervention for cybersecurity; the margin for error is simply too great. Instead, automation offers a structured and precise approach, ensuring vulnerabilities are identified and mitigated with unmatched efficiency.
Consider the fact that humans are fallible. They overlook details, succumb to fatigue, and their error margins can prove costly in a cybersecurity context. Automation drastically reduces these risks by performing tasks with the accuracy and speed that humans often cannot match. The narrative woven by automation in vulnerability management is one of empowerment, of allowing organizations to anticipate threats rather than merely reacting to them.
Barriers and Solutions in Automation
Despite its advantages, integrating automation in vulnerability management poses its own set of challenges. Companies must ensure that their automated systems are not just efficient but also secure in their operations. Misconfigurations or improper management can lead to vulnerabilities within the automated systems themselves. Hence, ongoing oversight and updates are crucial to ensure these tools are both current and secure. The solution lies in treating automation as a dynamic element of your security strategy, adapting as threats evolve and ensuring it remains as reliable as intended.
Effective Automation Implementation
Incorporating automation into vulnerability management ensures not only immediate security benefits but also long-term resilience. As digital ecosystems grow and evolve, automation provides a scalable solution, adapting quickly to new environments and threats. It’s imperative for cybersecurity teams to embrace this technology and optimize its use across their organizations. Whether addressing current threats or anticipating future ones, automation is a vital element of a robust cybersecurity strategy.
—10 Tips for Optimizing Automation in Vulnerability Management
1. Evaluate Your Current Infrastructure
Understand your existing systems to identify where automation can be integrated seamlessly.
2. Prioritize Key Vulnerabilities
Use automation to focus on high-risk areas that need urgent attention.
3. Leverage Advanced Analytics
Employ machine learning for smarter and more precise threat detection.
4. Implement Continuous Monitoring
Ensure that your systems are constantly scanned and analyzed for vulnerabilities.
5. Customize Solutions
Tailor automation tools to fit the unique needs of your business environment.
6. Integrate with Existing Systems
Ensure new automation tools work alongside current software without disrupting operations.
7. Stay Updated
Regularly update your automated systems to handle new and emerging threats.
8. Focus on User Training
Train your teams to effectively use and oversee automated systems.
9. Measure and Improve
Regularly assess the effectiveness of your automation strategies and make necessary adjustments.
10. Ensure Compliance
Use automation to streamline your compliance processes with various global standards.
Automation isn’t a fleeting trend but a paradigm shift in vulnerability management. By harnessing its full potential, organizations can protect their digital assets more robustly than ever before, ensuring that the promise of a secure future becomes a reality today.