H1: AI-Powered Intrusion Detection Systems
In the ever-evolving world of cybersecurity, AI-powered intrusion detection systems have emerged as game-changers. Imagine a security guard who never sleeps, learns continuously, and can predict intrusion attempts before they happen. These systems are equipped with cutting-edge artificial intelligence designed to identify unusual patterns that may indicate a potential security breach. With traditional security systems being increasingly overwhelmed by sophisticated cyber threats, AI-powered solutions have stepped in to revolutionize the industry. The promise of these systems lies in their ability to tirelessly safeguard against digital intruders while minimizing human error, thereby saving businesses from potentially catastrophic data breaches.
These systems leverage machine learning and deep learning algorithms to comb through vast amounts of data at lightning speed. They not only detect threats but evolve with each new piece of information, making them smarter and more efficient over time. Companies employing AI-powered intrusion detection systems often find themselves a step ahead of cybercriminals, as their systems don’t just react to threats—they predict and neutralize them proactively. Whether you’re a tech-savvy millennial or just someone who acknowledges the necessity of robust security in a digital age, these AI wonders are worth every dime.
But let’s not kid ourselves—implementing such advanced technology is not without its challenges. From initial investment costs to the complexity of integration with existing infrastructure, the path to enhanced cybersecurity requires careful planning and execution. Yet, the testimonials from businesses who’ve adopted AI-powered intrusion detection systems often highlight the significant peace of mind they gained, knowing their digital assets are in capable virtual hands. As the saying goes, better safe than sorry; and with cyber threats lurking around every corner, AI may just be the ally you need to sleep soundly at night.
H2: How AI-Powered Intrusion Detection Systems Work
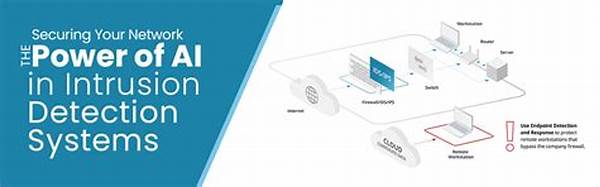
The AI-powered intrusion detection systems work by continuously analyzing network traffic and user behavior to detect anomalies that deviate from established norms. These powerful tools are divided into two main categories: signature-based and anomaly-based detection systems. Signature-based systems rely on a pre-defined set of known threat signatures while anomaly-based systems look for unusual patterns or behaviors. But what sets AI systems apart is their ability to incorporate both approaches, thus providing a 360-degree shield against potential breaches.
—
Purpose of AI-Powered Intrusion Detection Systems
H2: Why AI Matters in Cybersecurity
The necessity of AI in cybersecurity isn’t just about staying trendy—it’s about survival in an increasingly hostile online world. Cyber threats grow more advanced by the day, transcending the capabilities of traditional detection systems. Enter AI-powered intrusion detection systems, the knights in digital armor poised to defend your cyber kingdom. They operate with a level of efficiency and foresight unattainable by human operators, making them indispensable assets for any organization prioritizing digital security.
Imagine your business as an ancient fortress under constant threat from invaders. The cyber landscape is complex, with every nook and cranny of your digital fortress vulnerable to attack. AI-powered systems act as vigilant sentinels, combing through network data effortlessly, flagging potential threats before they breach your walls. These systems use machine learning algorithms to recognize and adapt to new threats, ensuring they are one step ahead of cyber criminals at all times.
H3: The AI Edge: Seamless Integration and Learning
One remarkable feature of AI-powered intrusion detection systems is their ability to integrate seamlessly into existing security infrastructures. This is no small feat, given the diverse array of cybersecurity tools and protocols employed by most organizations. The ability for AI systems to operate harmoniously with these varied systems is part of what makes them so effective. Moreover, as they gather and analyze more data, these systems become increasingly adept at recognizing potential threats, delivering notifications, and suggesting counteractions tailored to your unique security needs.
From a marketing perspective, the unique selling point of AI-powered intrusion detection systems is clear: they offer unparalleled protection while reducing the workload on human analysts. Businesses can redirect their security personnel to tackle more critical issues, knowing that AI systems are diligently overseeing the day-to-day monitoring. Testimonials often highlight not only the increased security but the cost-efficiency realized by businesses over time.
Recent statistics underscore the rising trend toward AI integration in cybersecurity practices, with an increasing number of companies reporting reduced breach incidents after adopting these advanced systems. This isn’t mere hype driven by tech companies but rather a reflection of the tangible benefits organizations experience firsthand. As adoption rates rise, it becomes evident that AI-powered intrusion detection systems are not just a luxury but a vital component of any robust cybersecurity strategy.
In conclusion, it’s imperative for modern businesses to recognize the role AI-powered intrusion detection systems play in safeguarding digital assets. The time to act is now—embrace the technological revolution and ensure that your organizational infrastructure is as secure as possible, leveraging AI’s unmatched capabilities as your front-line defense.
Examples of AI-Powered Intrusion Detection Systems
H2: The Evolution of AI-Powered Security
In a twist of irony, the rapid progression of technology, while intended to make life easier, has simultaneously paved the way for increased cybersecurity threats. This paradox has kept AI researchers and developers on their toes, constantly innovating new strategies to outmaneuver cybercriminals. The evolution of AI-powered intrusion detection systems stands as a testament to this ongoing battle—a relentless journey towards achieving ultimate cyber defense.
As these systems become more sophisticated, they offer unparalleled potential for strategic offense. Picture a chessboard where pieces are constantly rerouting, adapting, and outthinking an opponent. AI-fueled detection systems analyze countless scenarios rapidly, maintaining a vigilant posture that can both predict and deter intrusions before they manifest. The critical factor in their success hinges on continuous learning—an ability only made feasible through advancing AI technologies.
H3: Future Prospects and Potential Challenges
Creating a seamless interface between humans and AI in cybersecurity efforts will be a defining challenge as we look ahead. Though smart machine counterparts are undeniably beneficial, maintaining this synergy requires constant updates and training to remain ahead of emerging threats. This ongoing relationship is likened to having a vigilant partner who knows all the backdoors, hidden alleys, and best strategies for tackling digital adversaries. However, with rapid development comes the cost of implementation and the necessity of adapting current systems to accommodate these fresh technologies.
Envision a future where the terms “cyber breach” and “data loss” fade into oblivion, replaced by a heightened focus on innovation and growth. Businesses adopting AI-powered intrusion detection systems early will lead this shift, setting a standard for accountability and preparedness. As enterprises continue to build on AI-platform decisions, an era is ushered in where AI-driven security becomes commonplace, securing a safer digital frontier for all.
With the continuous ascent of AI in cybersecurity, there lies an important strategic service to align with: educating stakeholders on its overarching benefits while addressing potential hesitations. When presented effectively, such insight can redefine how businesses perceive and invest in security measures, ultimately ensuring secure advancements for future generations.
Illustrations of AI-Powered Intrusion Detection Systems
Understanding AI Integration in Cybersecurity
AI-powered intrusion detection systems are pioneering forces, revolutionizing how organizations across the globe defend against evolving cyber threats. These advanced systems don’t merely react to threats—they predict with precision, safeguarding business operations and digital integrity uniquely. Automatically logging critical events and maintaining detailed behavior records, they deliver vital insights, enhancing both transparency and security. As businesses continue to grow more digital and interconnected, an adoption of AI-powered solutions isn’t just recommended—it’s a pressing necessity. Choose to secure your operations today with AI’s advanced armory, ensuring tomorrow’s safety.