Advancements in Cyber Threat Intelligence Integration
In the digital age, where every click can lead to a potential cyberattack, advancements in Cyber Threat Intelligence (CTI) integration have never been more crucial. As companies and individuals become increasingly connected, they also become more susceptible to sophisticated cyber threats that move at lightning speed. Imagine a world where, instead of merely reacting to these threats, we anticipate and neutralize them before they can wreak havoc. This world is not only imaginable but increasingly achievable thanks to the latest developments in cyber threat intelligence integration.
Traditionally, organizations treated cyber threats with a reactive stance rather than a proactive one. This meant they would often only act after a threat had penetrated their systems, leading to data breaches, financial losses, and damaged reputations. However, the tide is shifting as advancements in cyber threat intelligence integration allow businesses to anticipate, understand, and outmaneuver threats before they cause harm. By leveraging sophisticated algorithms and enhanced data sharing across networks, companies can now predict potential threats with a level of accuracy that was previously inconceivable.
But why stop at enhanced prediction? The new wave of CTI integration means more than just identification ahead of time—it includes an entire ecosystem designed to identify, analyze, and mitigate threats efficiently. From machine learning to AI-driven analytics, the tools at our disposal have evolved, offering not just speed but precision in dealing with cyber threats. Organizations are finding themselves not at the mercy of cybercriminals, but increasingly prepared and armed to protect their digital territories in unprecedented ways.
Evolution of Cyber Threat Intelligence Solutions
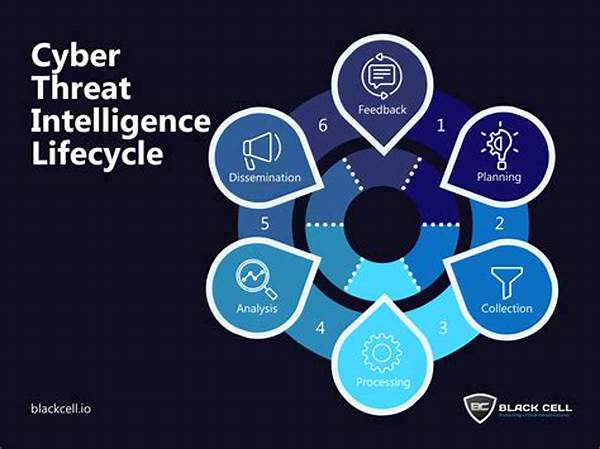
With advancements in cyber threat intelligence integration, solutions have also evolved to meet the growing demands posed by cyber threats. Today’s CTI platforms offer real-time threat intelligence processing, seamless data synchronization, and collaborative frameworks that allow for an exchange of vital threat data across different sectors. These enhancements not only bolster an organization’s defense but also empower them to launch countermeasures in real-time effectively. It’s not just about having information at hand—it’s about having the right information at the right time and knowing precisely what to do with it.
Now imagine your organization harnessing this power. Picture having a digital security system so robust, it’s like having a wily cyber detective on your team, always working to keep you out of harm’s way. This is the new reality ushered in by advancements in cyber threat intelligence integration—a reality businesses can no longer afford to ignore.
—Descriptions and More
In understanding advancements in cyber threat intelligence integration, it’s critical to unravel the significant benefits these integrations bring. As businesses navigate the complex digital landscape, the blending of various threat intelligence capabilities aids in proactive threat management, minimizing vulnerabilities, and providing comprehensive security coverage. This narrative isn’t just cheery optimism—it’s backed by statistics and real-world applications showcasing substantial improvements in threat detection and response times.
Benefits of Integration
Key advantages emerging from cyber threat intelligence integration include heightened accuracy in threat identification, reduced incident response times, and enhanced collaborative defense strategies. By amalgamating data from multiple sources, organizations gain a holistic view of potential threats and the methods bad actors might employ. According to research, companies implementing integrated threat intelligence systems report a 40% improvement in identifying threats before they cause damage.
Strategic Implementation
Strategic implementation of CTI can make all the difference. For instance, companies can now opt for customized threat intelligence solutions tailored to their specific needs, utilizing platforms that offer deep insights and analytics. This bespoke approach enables firms to prioritize threats that are most likely to affect their operations, ensuring resources are not wasted on low-level concerns.
Enhanced Detection Capabilities
Integration doesn’t just offer intelligence—it provides upgraded detection capabilities. This enhancement allows for rapid identification of unusual activities that may indicate a security breach. Organizations benefit from automated alerts and reports, giving them the much-needed head start to counter looming threats.
Real-World Applications
As evidenced by recent case studies, sectors like finance and healthcare, which hold critical user information, have significantly reduced their risk exposure by adopting advanced threat intelligence solutions. This reduction translates not only to fewer security incidents but also to increased trust among customers and stakeholders.
Immediate Call to Action
Companies are encouraged to assess their existing cyber threat frameworks and consider integrating advanced cyber threat intelligence solutions. Investing in these technologies becomes a formidable asset, promising robust protection against an evolving range of cyber threats.
Collaborative Efforts
In promoting cyber resilience, collaboration between private sectors, government bodies, and threat intelligence providers becomes indispensable. As cyber threats grow in complexity, so must our collective efforts in sharing threat intelligence and best practices to fortify defenses across industries.
—Topics Related to Advancements in Cyber Threat Intelligence Integration
—Exploring Key Elements
Organizations are increasingly investing in advancements in cyber threat intelligence integration, seeing it as an essential part of their strategic security portfolio. The demand stems from an urgent need to stay ahead of cybercriminals’ tactics which are becoming more refined and damaging. Companies understand that filling gaps in their cyber defenses isn’t just a game of odds but a calculated strategy based on robust intelligence gathering and swift response initiatives.
One of the remarkable aspects of this integration is its ability to cross traditional boundaries with seamless international collaboration over threat data. Cyber threats recognize no borders, and neither do the responses needed to counter them. This global connectivity has turned the tide significantly as networks and enterprises work together to thwart malicious attacks from multiple vectors.
Furthermore, advancements in CTI make room for innovation in developing more adaptive algorithms and intuitive interfaces. These advancements cater not only to IT professionals but are now more accessible to business leaders and decision-makers who require real-time data feedback to make swift organizational decisions.
The combination of automation and human expertise leads to stronger defense mechanisms across digital networks, paving the way for a future where cybersecurity is well-integrated, not a separate afterthought. This integration has solidified its place in robust cybersecurity frameworks, promising ongoing developments and innovation in the field.
—5 Tips for Advancements in Cyber Threat Intelligence Integration
In taking these steps, businesses and organizations can prioritize their cybersecurity efforts effectively, guard against potential threats with greater efficiency, and create a more secure digital environment. These practices reinforce the idea that advancements in cyber threat intelligence integration are not just beneficial but necessary in today’s rapidly evolving threat landscape. By committing to these strategies, organizations can actively protect their digital assets, customer data, and ultimately, their reputations.