In a world where digitalization leads the future, securing data has become paramount. Imagine your data as a grand mansion filled with valuable paintings, rare gems, and memories of yesteryears. Now, would you leave the doors wide open for everyone to casually stroll in, or would you have a sophisticated lock system to keep the unwelcome at bay? Welcome to the world of Access Control List Implementation — the master key to your data’s security.
Read Now : “advanced Virtualization Techniques For Data Centers”
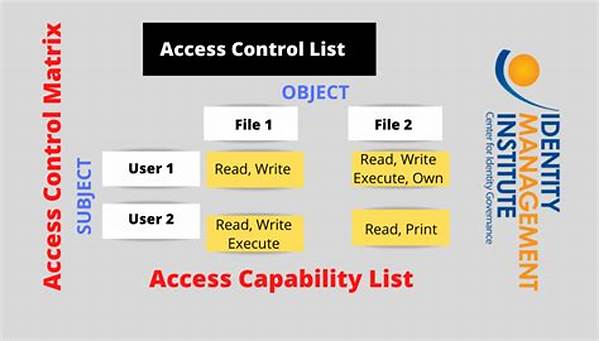
Access Control Lists (ACLs) provide a way to enforce permissions in computer systems, determining who is allowed entry to specific objects and what actions they may perform. Indeed, ACLs play the role of a digital butler, offering the highest level of exclusivity, as only those on the list are granted access. Think of it as the VIP list for your IT infrastructure. The meticulous implementation of ACLs involves specifying who can view, modify, or delete information on your systems. This is not just a luxury, but a requisite — especially for businesses aiming to protect sensitive information from threats that lurk in the digital shadows.
With humor and a dash of wit, imagine an office space where employees bob their heads to tunes of cyber jargons, yet who really holds the keys to each digital room? It’s the magic of Access Control List Implementation. Not all superheroes wear capes; some wear glasses and work tirelessly to ensure that Alan from marketing doesn’t accidentally delete the entire company’s financial records. With ACLs, you can customize security levels unique to each user, ensuring each ‘door’ in your digital workspace opens only for the right ‘key holders’.
Why Access Control List Implementation Matters
The significance of access control list implementation is underscored by statistics revealing that around 60% of data breaches are due to internal threats or simple human error. Having a stringent ACL system in place can eliminate these prevailing risks by setting precise controls on who can or cannot access certain data within a network.
—
Description of Access Control List Implementation
Picture this: a blogger writing humor-infused posts late into the night, a coffee mug their only companion. Suddenly, a pop-up crashes their flow — security alert! They gasp, feeling like a protagonist in a thriller novel. This could have been prevented with effective access control list implementation. In a digital landscape where security threats abound, having a well-thought-out ACL is akin to having a trusty sidekick in a comic book saga.
ACL implementation involves defining permissions and control settings across various digital environments, from cloud computing to local networks. At its core, it’s about authorizing who can read, write, or execute certain aspects of your system. This reliable framework doesn’t operate on whims but is grounded in strategic planning and business insights, aligning security measures with organizational goals.
Benefits of Access Control List Implementation
Smart executives know this: data is gold, and just like any valuable, it deserves top-tier security. When ACLs are meticulously implemented, they thwart unauthorized access with the deftness of a ninja, ensuring peace of mind for stakeholders. Companies can shield themselves from the menace of cyber-attacks, protecting not just their reputations, but their bottom lines.
The process of access control list implementation is akin to crafting a fortified fortress, equipped with state-of-the-art surveillance. It is crucial for organizations to engage in regular evaluation and updates, fortifying ACLs against evolving threats. Just like every trendy gadget needs its periodic updates, your ACL too requires regular finetuning to remain effective.
Delving Deeper: Layers of Access Control List Implementation
Access control isn’t a snazzy coat you wear occasionally. It’s the enduring armor that shields your digital ecosystem day in and day out. Ensuring your ACL implementation is robust requires the adoption of best practices, from encryption to two-factor authentication. Careful monitoring and constant vigilance empower businesses with the readiness to respond swiftly to potential security threats.
Read Now : Free Ai Software Collections
Strategies for Access Control List Implementation
Consider a renowned chef concocting a recipe that’s an amalgamation of several exotic ingredients, each adding a unique flavor to the dish. Similarly, creating a robust ACL involves integrating a variety of security measures that bolster the overall system efficacy. Automating processes, performing regular audits, and training employees on security protocols can further amplify the protective shield ACLs offer.
—
Steps for Successful Access Control List Implementation
The process of access control list implementation is dynamic and requires continual attention. It demands an investigative mindset, exploring deficiencies, and iterating improvements. When successfully executed, ACLs can serve as your digital kingdom’s most trusted sentries, ensuring your treasures are comprehensively safeguarded.
Understanding Access Control List Implementation
For the enthusiast, or the security-conscious business leader wishing to understand access control lists on a deeper level, think of ACLs as a customizable shield. Craft a security system that is not just effective but capable of evolving with the ever-changing threat landscape. ACLs are not just about restricting access, but they are a fundamental component of a holistic cybersecurity strategy.
The Future of Access Control List Implementation
As technology evolves, so does the sophistication of cyber threats. Staying ahead necessitates a proactive approach, incorporating the latest advancements in ACL implementation. From AI-driven security solutions to leveraging big data analytics, the potential enhancements to ACL systems are a testament to how integral they are in the present and future context of data security.
By adhering to these insights and implementing sound ACL practices, the likelihood of unauthorized access is minimized, transforming your digital environment into an impregnable fortress. Businesses and individuals alike can sleep soundly knowing their cherished data is under the vigilant watch of a system as robust as access control list implementation.