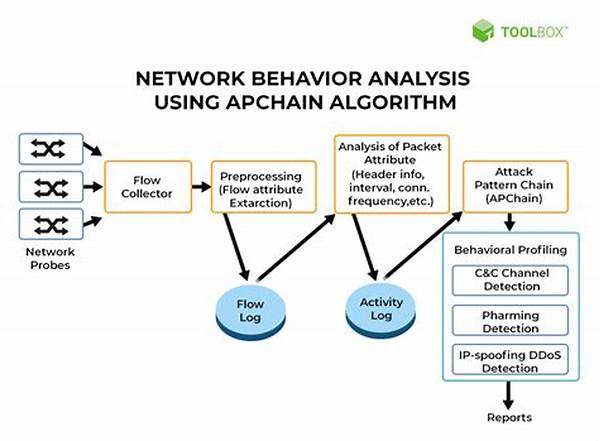
H1: Behavioural Analysis in Cybersecurity
In a world where digital threats lurk in every corner of the cyber universe, understanding user behavior has become the new frontier in cybersecurity. Picture this: cyber bandits plotting day and night to snatch your sensitive data. But what if you had a tool to predict their moves before they strike? Enter behavioural analysis in cybersecurity, a game-changing approach that is revolutionizing the way we safeguard our digital spaces. From enterprise-level systems to personal digital assistants, identifying and analyzing the patterns of user behavior can mean the difference between a major security breach and a peaceful night’s sleep.
Behavioral analysis in cybersecurity is akin to having your own Sherlock Holmes investigating patterns and deducing the odd one out in your digital persona. Imagine a world where your system automatically identifies a rogue insider by picking up strange patterns in their login times or flagging a peculiar data transfer that doesn’t adhere to the norm. This innovative technique utilizes artificial intelligence and machine learning algorithms to constantly monitor the behavior of users and systems. It flags anomalies, assesses threats, and adapts defenses in real-time. All that without the need to scroll through endless logs of data.
This method transcends traditional cybersecurity practices by proactively addressing potential threats. Instead of waiting for a breach to occur, behavioral analysis takes prevention to the next level. By identifying the telltale signs and flagging questionable behavior, organizations can fortify their defenses and nimbly thwart potential crises. With the increasing sophistication of cyber-attacks, relying solely on conventional signature-based defenses is more of a cyber risk than a relief.
The dynamic nature of behavioral analysis makes it a key player in the cybersecurity arena, offering not just a reactive but a preemptive solution. As we plunge deeper into a digitally driven era, the question isn’t if one will encounter cyber threats, but when. It’s stories like Jane, the IT manager, who discovered a breach in the nick of time using behavioral analysis, that drive home the crucial role it plays. As organizations large and small begin to embrace this technology, it’s shaping the cybersecurity narrative with a compelling offer: protection tailored not just to your systems, but to how your entities behave and interact.
H2: The Science Behind Behavioural Analysis in Cybersecurity
Behavioral analysis in cybersecurity is more than a buzzword; it’s a paradigm shift. Aided by technology, we’ve journeyed from reactive measures to proactive defenses. What makes behavioral analysis in cybersecurity stand out is its ability to learn and adapt. Just like our immune system learns from past infections to fend off future ones, behavioral analysis systems evolve by learning the patterns of users and devices involved.
In this evolving digital landscape, businesses that have adopted behavioral analysis are reaping the benefits. Linda, for example, an e-commerce giant executive, realized substantial improvements in their security posture when they integrated behavioral analysis into their decision-making processes. Instead of wading through security logs to detect threats, her team now leverages real-time data — a digital lighthouse in a sea of potential threats.
Let’s delve into how this cutting-edge tool functions. At its core, behavioral analysis in cybersecurity involves compiling vast amounts of data related to user behavior, network traffic, and system interactions. Sophisticated algorithms then process this data, searching for patterns and anomalies. When something stands out, it’s flagged for human investigation or automatically responded to if identified as a threat.
The beauty of this technology is the foresight it provides. It’s like having a digital intuition that senses when things are about to go awry. As threats continually evolve, static defense methods fall short. With behavioral analysis, though, each anomaly is an opportunity to evolve, to refine, and to build a more robust defense mechanism. In embracing the unpredictability of human behavior, this analysis overcomes the limitations of one-size-fits-all security solutions, offering customized protections that evolve as you do.
H2: Examples of Behavioural Analysis in Cybersecurity
Discussion
With behavioral analysis in cybersecurity, the conversation around digital protection is changing. Many organizations see it as the next evolutionary step in crafting a bulletproof cyber defense. But as we dive deeper into this discussion, one must ask: is this the only solution for modern cybersecurity threats? Behavioral analysis is undeniably powerful, providing insights and foresight that are unparalleled. However, its implementation does come with inherent challenges such as managing false positives and ensuring data privacy compliance.
Consider the story of a major corporation that implemented behavioral analysis software. Initially, the software flagged numerous legitimate actions as potential threats. While frustrating at first, it pushed the IT team to fine-tune the system, resulting in an optimized safety net that eventually saved them from a costly breach. It demonstrates the importance of teamwork between human analysts and advanced algorithms in bringing out the best of this technology.
Moreover, as valuable as behavioral analysis is, it ideally should be part of a multifaceted security strategy. Organizations must continue to invest in employee education to ensure they are not the weakest link, enforce strong password practices, and regularly update security protocols. Only then can businesses rest assured knowing they have employed a holistic approach to safeguarding their digital assets. As a result, embracing behavioral analysis becomes not just an option but a critical component of an all-encompassing cybersecurity narrative.
H2: The Role of Behavioral Analysis in Shaping Cybersecurity Strategies
As cybersecurity evolves, so does the need to integrate different methods and strategies. One crucial aspect often overlooked is how behavioral analysis can shape an organization’s cybersecurity strategy. This is not just a tale of identifying threats but crafting a comprehensive defense mechanism that’s responsive and adaptive to changing patterns.
In summary, behavioral analysis in cybersecurity isn’t just a trend; it’s an emerging cornerstone for crafting resilient security strategies. By providing insight into user behavior and potential threats, businesses can make informed decisions in real-time. As cyber threats grow more sophisticated, the emphasis on predictive, rather than reactive, measures becomes ever more critical. The takeaway? You can’t control the digital wild west, but with behavioral analysis, you can certainly patrol it with cyber flair.
H3: Empowering Cybersecurity Measures with Behavioral Analysis
As Steve Wozniak, co-founder of Apple, once said, “Never trust a computer you can’t throw out a window.” With behavioral analysis, you might not need to. Instead of aiming for the digital power button, you’ll find reassurance in detecting, analyzing, and responding to threats before they crawl through your digital windows. Therefore, deploying behavioral analysis isn’t just an enhancement; it’s a leap towards a safer digital tomorrow.