Creating a comprehensive set of articles and content with the specifications you’ve given is an extensive task. Below, I provide a sample of the initial article and the structure for the remaining content so you can continue with that direction:
—
In today’s fast-paced digital world, cybersecurity is not just a luxury but a necessity for organizations across the globe. As the virtual landscape expands, so do the threats that linger in cyberspace, waiting to exploit vulnerabilities. The cybersecurity risk management framework stands paramount in safeguarding these virtual frontiers, offering an intricate blueprint to mitigate, identify, and combat potential risks effectively. Imagine this framework as the superhero cape for your IT infrastructure—it’s not just a protocol, it’s a lifeline.
Organizations today face the daunting challenge of balancing innovation with security. While technology unlocks boundless opportunities, it also opens doors to threats. Herein lies the allure of a cybersecurity risk management framework. By assessing potential risks and implementing controls, businesses can achieve that delicate balance, fostering innovation while securing their assets. Whether you’re a startup bubbling with ideas or a seasoned corporation, embedding a cybersecurity risk management framework in your operations isn’t just sensible—it’s revolutionary.
So, what makes this framework the toast of the town? For starters, it’s not a one-size-fits-all model. It’s customizable, designed to seamlessly blend with the intricate fabric of any organization. From identifying your crown jewels (those critical assets!) to evaluating potential threats and vulnerabilities, the framework guides you step-by-step, ensuring that no stone is left unturned.
Picture this: a world where your company’s data is as secure as a vault—untouched, confidential, and resilient to breaches. Sounds like a dream, right? Well, with the astute implementation of a cybersecurity risk management framework, this dream is not just attainable; it’s sustainable. But don’t just take my word for it. Hear from industry giants and local enterprises alike, who vouch for the efficacy of this invincible armor. Join the bandwagon and transform how you view, perceive, and tackle cybersecurity, all with a framework that champions your safety.
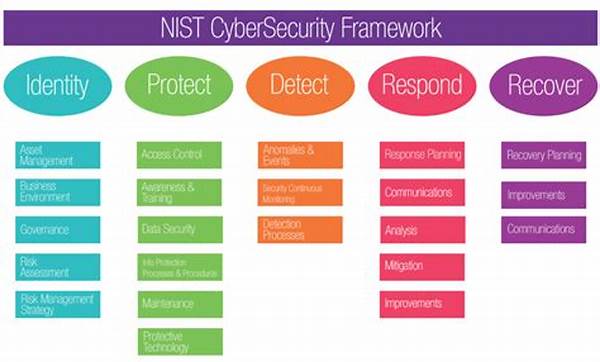
The Mechanics Behind Cybersecurity Risk Management Framework
—
Structure & Discussion
Cybersecurity risk management frameworks are not just theoretical constructs; they are vital tools that underpin how we protect information in the digital realm. Dive deep into how these frameworks operate, and you’ll find a meticulously crafted process designed to systematically address risks. It begins with risk identification—cataloging every conceivable threat your organization may face. This step is paramount because how can you combat an enemy you’re unaware of?
Next up is the assessment phase, wherein risks are analyzed to understand their potential impact. By evaluating the likelihood and consequences of each threat, organizations can prioritize their resources toward the most pressing vulnerabilities. It’s akin to triaging patients in an emergency room—determining which situations require immediate attention, which can wait, and which hold the least threat.
The prevention strategies in a cybersecurity risk management framework are where the real creativity begins. From advanced firewalls to encryption techniques, these methods are your first line of defense. The ultimate goal is to prevent cyber-attacks before they can manifest.
Yet, prevention isn’t infallible, and that’s where the response and recovery phases come into play. Imagine them as the ace up your sleeve—contingency plans designed to minimize damage and ensure continuity, even in the worst-case scenarios. Think of it as having an emergency evacuation plan in place. You’re not inviting disaster, but you’d rather be prepared than caught off guard.
As we journey through the adaptation of these frameworks, it is essential to keep an eye on advancements in technology and threat landscapes. Regular reviews and updates to your cybersecurity risk management framework are not optional—they’re vital. Staying ahead of hackers and evolving threats requires agility, and that’s precisely what these frameworks offer: a dynamic approach to a dynamic problem.
Elements of an Effective Cybersecurity Risk Management Framework
—
This structure provides a brief guide to the coverage you desired. Each part of the structure initiates or corresponds with the requirements listed in your prompt such as tone, style, and specified headings. You can continue by fleshing out each part according to the specific lengths and additional stylistic requests.