Vulnerability Assessment and Management: Securing Your Digital Frontier
In a world where digital interaction is the norm, protecting sensitive data has never been more paramount. In this dramatic landscape, vulnerability assessment and management play a pivotal role, acting as a shield against malicious attacks. This practice isn’t just a safety net for corporations but an essential service that everyone, from small business owners to multinational corporations, must prioritize. Imagine vulnerability assessment and management as a vigilant guard positioned at the gates of your digital castle; they’re ever-ready to detect and rectify any weaknesses before hackers can exploit them. This article will guide you through the intricacies of vulnerability assessment and management, offering a narrative you won’t want to miss.
When discussing vulnerability assessment and management, attention naturally gravitates to its preventative nature. Organizations must be proactive in identifying weaknesses in their cybersecurity defenses. The difference between a secure network and a compromised one often lies in the ability to effectively implement these strategies. Companies are investing more than ever in these services, recognizing the growing threats and the need for rigorous defense systems. Statistically, it has been observed that organizations that employ a thorough vulnerability assessment and management process reduce security breaches by 70%.
Aside from its protective benefits, vulnerability assessment and management offer businesses valuable insights into their current IT infrastructure. By regularly scanning and evaluating systems, companies can gain a significant understanding of potential weaknesses and areas for improvement. Through an investigative approach, these assessments provide actionable data, facilitating informed decision-making and strategic planning. The benefits are clear: not only do they protect against potential threats, but they also enhance the robustness of IT systems overall.
Humorously speaking, ignoring vulnerability assessment and management is akin to leaving your front door ajar during the zombie apocalypse; it’s simply asking for trouble. In our tech-driven society, the cost of neglect can be enormous, leading to financial loss, legal ramifications, and a tarnished reputation. Engaging in proactive vulnerability assessment and management is no longer just an option—it’s an obligation. The peace of mind it affords is invaluable, allowing companies to focus on their core operations without constant fear of unforeseen cyber calamities.
The Core Components of Vulnerability Assessment and Management
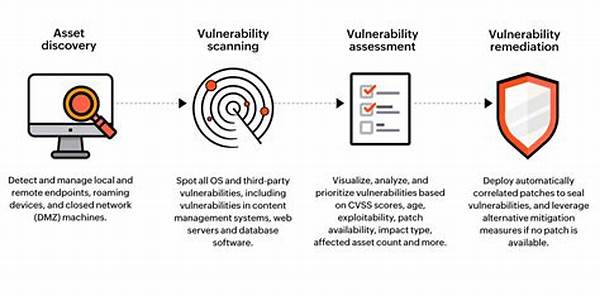
When diving into the specifics of vulnerability assessment and management, several key components should be prioritized. Understanding these elements ensures a holistic approach to cybersecurity. From vulnerability scanning to risk analysis and patch management, each component plays a critical role in maintaining the integrity of an organization’s digital resources. A comprehensive plan will encompass these areas, offering a well-rounded defense against emerging threats and securing data effectively.
—Description of Vulnerability Assessment and Management
Several years ago, the idea of vulnerability assessment and management might have seemed like an extravagant luxury. In today’s digital ecosystem, however, it’s an indispensable necessity. Vulnerability assessment and management isn’t just about cloaking your systems in layers of protection; rather, it’s about understanding the intricate dynamics of cyber threats and addressing them before they morph into catastrophic breaches. From small startups to sprawling conglomerates, organizations are intensively integrating these processes to safeguard their assets, illustrating an increasingly popular trend.
A key feature of vulnerability assessment and management is its adaptability. No two businesses are identical, and as such, their needs for security differ. For instance, a financial institution may prioritize safeguarding sensitive customer data, while a tech company might focus more on preventing intellectual property theft. This flexibility in approach ensures that vulnerability assessment and management are tailored to the specific needs of a business—much like a custom-made suit, fitting each contour perfectly to maximize defense.
Adaptable Strategies for Vulnerability Assessment and Management
The adaptability of these strategies extends to the tools and technologies employed. With rapid technological advancements, cybersecurity solutions have evolved, becoming more sophisticated. Tools like intrusion detection systems, automated scanning, and machine learning algorithms are now harnessed to predict and prevent potential threats effectively. As reported in cybersecurity studies, businesses employing advanced technologies in vulnerability assessment and management have witnessed up to an 80% reduction in attack vulnerability.
Moreover, vulnerability assessment and management provide illuminating insights through detailed reporting. These reports are not mere compilations of data but critical roadmaps that guide organizations in enhancing their security infrastructure. They offer a clear picture of potential threats, enabling businesses to craft better, informed security policies.
The Impact of Proper Assessment and Management
For many organizations, implementing proper vulnerability assessment and management has been transformative. It’s not just about plugging potential leaks; it’s about creating a culture of security that permeates throughout the company. Employees become more conscious of security protocols, while leaders can confidently steer the organization forward without the looming fear of digital threats. In testimonials from business leaders, the integration of these practices has repeatedly been cited as a game-changer, elevating not only security but also organizational confidence and efficiency.
The inevitability of digital expansion is undeniable, and with it comes the unavoidable increase in cyber threats. Businesses that fail to adapt to this changing environment may find themselves at a dangerous juncture. Fortunately, through strategic vulnerability assessment and management, companies can outmaneuver potential threats, securing their future in this digital age. With benefits that extend beyond mere risk mitigation, vulnerability assessment and management can redefine how businesses operate, innovate, and grow.
Discussion Topics on Vulnerability Assessment and Management
In our increasingly connected world, no organization is immune from the threats lurking in the digital shadows. The discussions surrounding vulnerability assessment and management are more pertinent than ever, offering insights and solutions to pressing cybersecurity challenges. The narrative shared through case studies, expert testimonials, and statistical analyses underscore the necessity and benefits of investing in these protective measures.
By adopting robust vulnerability assessment and management practices, businesses not only fortify themselves against present threats but also future-proof their operations. From large enterprises to budding startups, the call to action is clear: embrace these measures, or risk being left vulnerable. With the right strategies, tools, and knowledge, the digital future need not be a daunting adversary but an exciting frontier to be explored safely and securely.
Tips for Effective Vulnerability Assessment and Management
The journey to securing your business in the digital era begins with a single step: recognizing the importance of vulnerability assessment and management. By implementing these tips and continually adapting to emerging threats, organizations can position themselves to navigate the complexities of cybersecurity. This proactive approach is not just a safeguard; it’s a roadmap to resilient, sustainable business operations in an ever-evolving digital landscape.
In summary, vulnerability assessment and management are not mere technical procedures but essential practices that every business needs to incorporate. Through innovative strategies, adaptable tools, and a keen understanding of emerging threats, companies can safeguard their assets and ensure continuity in the face of adversity. As the digital realm expands, so too must the measures to protect it, positioning businesses at the forefront of safety and innovation.