Detailed Packet Analysis Techniques
In today’s digital era, understanding what flows through our networks is crucial, not just for cybersecurity professionals but for anyone who values their digital privacy. Welcome to the world of detailed packet analysis techniques—a realm where bits and bytes tell tales of transactions, communications, and sometimes, misdeeds. Imagine each packet as a tiny envelope passing through unseen channels, carrying a treasure trove of information that can be deciphered and acted upon. Whether you’re a network admin, a security analyst, or simply a curious netizen, mastering the art of packet analysis offers a front-row seat to the invisible theater of the internet.
If you’ve ever wondered how your data travels from point A to B in mere milliseconds, it’s time to uncover the layers of protocols that make this magic happen. Detailed packet analysis is not just about capturing data; it’s about interpreting it, transforming raw data into actionable insights. This domain empowers you to identify security breaches, optimize network performance, and ensure compliance with stringent data protection regulations. Intrigued yet? Stay tuned as we unpack the essence of packet sniffing, deep dive into tools like Wireshark, and explore the techniques that define the cutting edge of packet analysis, making you the digital detective your network needs.
While some see packets as mere data, professionals employing detailed packet analysis techniques know they’re the vital clues in unraveling complex mysteries within networks. By learning how to decode and interpret these packets, you can proactively defend your network, upgrade its speed, and even troubleshoot pesky connection issues with the finesse of a seasoned expert.
Exploring the Essentials of Packet Analysis
Understanding the Power of Detailed Packet Analysis Techniques
Packet analysis is not just a job; it’s an adventure into the unknown realms of bytes and protocols, where each interaction tells a story. The art of analyzing network packets can turn any digital detective into a master analyst, capable of unveiling the secrets hidden within every stream of data. Successful network monitoring, security, and optimization hinge on understanding the intricacies of packets traveling through the network.
In the domain of cybersecurity, detailed packet analysis techniques are indispensable. They empower IT professionals to spot nefarious activities long before they become tangible threats. Imagine being able to pinpoint a data breach as it’s happening or detect an unauthorized access attempt before any data is compromised. This proactive approach can save organizations from significant financial loss and reputation damage.
Yet, there’s more to packet analysis than security. Network administrators leverage these techniques to finetune their systems. By interpreting packet data correctly, they can identify bottlenecks, understand user behaviors, and redistribute load where necessary. Whether it’s ensuring a seamless user experience during high traffic or troubleshooting a malfunctioning application, packet analysis is the backbone of an efficient network.
Detailed packet analysis techniques don’t require a suite of expensive tools or reams of technical manuals. Rather, they demand a curiosity-driven mindset ready to explore patterns and anomalies. Tools like Wireshark and tcpdump provide accessible entry points into packet investigation, turning mundane sequences of ones and zeroes into enlightening narratives. They democratize access to deep network insights that anyone with a penchant for exploration can master.
As an IT professional, you’re on the frontline of your network’s security and performance, so shouldn’t you equip yourself with the best skills and tools to tackle potential threats and maintain robust operations? Delve into detailed packet analysis techniques and transform yourself into the go-to guru for all things network-related.
The Tools of the Trade
Wireshark: The Sleuth’s Choice
Wireshark is arguably the most well-known tool in packet analysis, adored for its intuitive interface and robust feature set. It’s used by network administrators, cybersecurity experts, and hobbyists alike for monitoring network traffic and spotting anomalies. Consider it the magnifying glass in a detective’s toolkit, allowing you to zoom into packet details like never before.
With a simple-to-navigate interface, Wireshark provides users with the ability to dissect packet details, examine protocol structures, and identify the nuances of network streams. Learning to navigate Wireshark is a rite of passage in the world of detailed packet analysis techniques. It helps you interpret the vast sea of data into meaningful, actionable insights, all at the tips of your fingers.
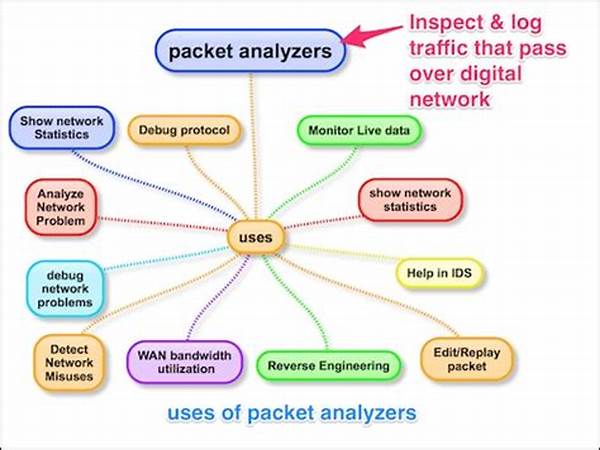
For those ready to dive deeper, here are eight engaging examples of real-world applications and benefits brought forth by detailed packet analysis techniques:
Each of these applications represents a crucial aspect of network management and enhances the importance of detailed packet analysis techniques in today’s technology-driven world.
Advanced Packet Analysis Strategies
Unraveling the Mystery of Network Data
Have you ever been mystified by how data packets traverse the internet in a blink? As you dive into the universe of detailed packet analysis techniques, you’ll start seeing networks not just as chaotic webs of signals but as organized pathways governed by logic and discipline. Every packet holds a message waiting to be deciphered, and understanding these fresh insights can often be akin to solving a captivating puzzle.
Diving into packet analysis begins with appreciating its role as both an art and a science. While the former speaks to the creativity required to navigate complex data streams, the latter emphasizes the precise methodologies available. Whether using Wireshark for initial investigations or advancing to more sophisticated methods, the principles remain the same — distilling raw data into actionable intelligence and converting potential network vulnerabilities into triumphs of tech-savvy analyst work.
Intriguingly, it’s also about finding patterns amid chaos. Perhaps you’re investigating mysterious slowdown issues; an elusive pattern or a rogue packet might reveal the culprit. When networks perform well, detailed packet analysis techniques often sit quietly in the background. But when alerts sound, and issues emerge, these techniques transform into sharp tools, quickly identifying and remedying stubborn digital gremlins affecting communication and performance.
For testers and analysts new to this field, start by setting clear objectives. Know what you’re aiming to uncover before you commence. Is the goal to ensure operational efficiency, detect security anomalies, or something entirely different? Demystifying intricate network behaviors requires both vision and precision — traits that detailed packet analysis magnifies and enriches.
Incorporating these techniques into routine network monitoring can reveal invaluable insights. They pave a clear path to network optimization, providing coherent direction even amid potential misinformation. Next-generation network solutions increasingly benefit from integrated packet analysis, empowering automated responses that extract timely, critical network insights.
Ultimately, adopting detailed packet analysis techniques represents an investment in network integrity and performance. Equip yourself with this digital decoder ring, and you’ll transform potential chaos into understood, manageable, and operationally optimized realities.
Leveraging Technology for Packet Analysis
Practical Applications and Use Cases
In the bustling age of the internet of things, packet analysis has become indispensable for anyone involved in network management or cybersecurity. By employing detailed packet analysis techniques, network professionals can proactively manage, secure, and enhance their digital ecosystems with ease and efficacy.
Examples to consider:
Crisp Short Reads with High Impact
The Journey of Packet Analysis: Navigating Digital Data
Welcome to the absorbing realm of packet analysis, where the nuances of network data reveal their secrets through meticulous observation and diagnosis. The digital landscape we navigate daily is complex and rich in information, with each packet carrying vital information across global networks. As we become more digital-dependent, understanding the beats and bytes of data transmission becomes paramount.
Embarking on this journey begins with recognizing the value of detailed packet analysis techniques. They are your lenses, allowing you to zoom into the layers of data for insights that can redefine network performance and diminish security threats. Rather than a singular approach, this involves a toolkit of methodologies, such as filtering, capturing, and analyzing, to dissect and reconstruct each data packet for operational clarity.
Industrial sectors harnessing data analytics thrive on these techniques. By interpreting data movement across networks, companies can predict bottlenecks, streamline communication processes, and tailor customer experiences to new heights. Detailed packet analysis is not merely a method — it is a revolution, consistently evolving alongside technological advancements. The network analysis landscape today benefits immensely from automation and AI, turning what once took hours into near-instantaneous results.
This could appear daunting for newcomers. But fear not! Equip yourself with knowledge, remain curious, and embrace advancements like intelligent packet analysis tools. This will empower you with capabilities to manage, respond to, and predict technological challenges with finesse and immediate effect. Moreover, engaging in communities and interactive forums can provide invaluable support and expertise sharing.
In a world increasingly driven by data, adapting to poor network performance is unnecessary. Armed with the right techniques, you can ensure seamless data flow, robust security, and optimized digital communication. Discover a universe of opportunity where ingenuity meets data-driven clarity.
Streamlining Data Flow Techniques
Comprehensive Packet Analysis Insights
Overall, diving into packet analysis unlocks a plethora of possibilities. From seamless data transfers and efficient communication to fortified cybersecurity efforts, these techniques prove indispensable. They empower organization-wide responses, allowing IT teams to provide quick recoveries post-incidents, effective resource allocation, and powerful insights into user interactions.
To sum up, don’t let the network’s rhythm skip a beat. By honing detailed packet analysis techniques, you nurture the backbone of modern communication, ensuring the world remains connected smoothly and securely. From bustling enterprises to small deskside operations, everyone can take advantage of the potential they unlock.
Below are seven illustrations for an enriched understanding of packet analysis:
By leveraging these illustrations, network professionals can gain comprehensive insights into packet dynamics, ensuring efficient and secure data transport across networks. As the digital landscape evolves, adopting detailed packet analysis techniques will continue to play a vital role in maintaining the integrity and performance of global connectivity.