In the ever-evolving landscape of data technology, automated anomaly detection algorithms are becoming indispensable tools for businesses aiming to secure their networks and optimize their services. Imagine this: your company is sailing smoothly when suddenly, an unexpected anomaly threatens to steer your processes off course. Without the trusty compass of anomaly detection, businesses are left to navigate the choppy waters blindfolded. But, what if there was a beacon of hope that ensures smooth sailing—seamlessly, automatically, and efficiently? Enter automated anomaly detection algorithms—your digital North Star.
The world is teeming with data spilling from every crevice of the internet. Like a never-ending font of information, this deluge can sometimes be overwhelming, leading to missed opportunities and unforeseen threats. Automated anomaly detection algorithms are sophisticated tools designed to sift through this data and highlight the anomalies—those pesky deviations that could herald system failures, security breaches, or fraud. But hold onto your hats, this story gets better. These algorithms not only spot the irregularities but do so with the precision of a Swiss watch, allowing businesses to act before small blips transform into catastrophic events. Whether you’re managing transaction data for a global enterprise or overseeing network activity for a burgeoning tech startup, automated anomaly detection algorithms are your secret password to peace of mind and operational excellence.
The magic of automated anomaly detection algorithms lies in their ability to learn and adapt. Like seasoned detectives, they pick up patterns, build profiles, and alert you to the suspicious unordinary activities. The process is intricate yet surprisingly hands-off for users, creating an experience akin to having a virtual data guard dog ever watchful for signs of trouble. But how exactly does this black box wizardry work, and what are its limitations? Let’s dive deeper as we explore how these algorithms are reshaping industries, protecting assets, and doing it all with a hint of algorithmic charm.
The Mechanics of Automated Anomaly Detection Algorithms
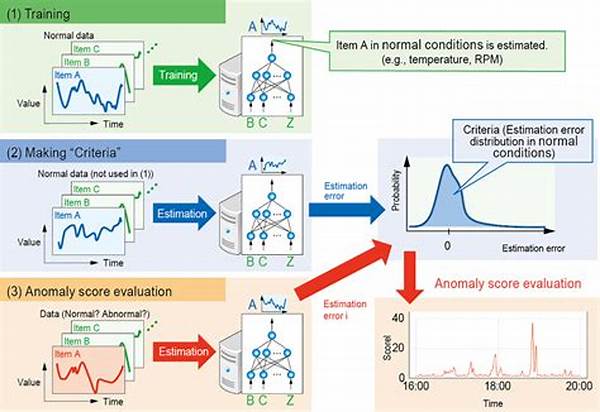
The mechanics behind automated anomaly detection algorithms are both a marvel and a mystery. Utilizing techniques such as machine learning, statistical analysis, and neural networks, these algorithms are able to distinguish between normal patterns and anomalies. It’s a dance of numbers and logic, where the rhythm is as crucial as the melody.
—
Automated anomaly detection algorithms serve a multitude of purposes, each as vital as the next in today’s data-driven world. At the forefront is ensuring data integrity, where these algorithms function as vigilant guardians standing watch over digital landscapes. They are programmed to notice the smallest shifts in data pools, like a hawk eyeing the terrain for prey. By identifying these deviations early, businesses can proactively prevent detrimental impacts, whether it’s a security breach, a financial misstep, or an operational hiccup. Their perspicuity in early detection makes them indispensable to any organization keen on maintaining robust health in their data ecosystems.
Another pivotal role of automated anomaly detection algorithms is in the realm of cybersecurity. In the age of cyber warfare, protecting sensitive information is not just recommended; it’s necessary. These algorithms help address this vulnerability by flagging unusual patterns that may signify cyber threats such as data breaches or unauthorized access attempts. Their deployment helps in safeguarding not just the data but also the trust clients place in the system’s integrity. In this digital armory, the algorithms function as a protective shield, allowing businesses to operate without fear of invisible threats.
Beyond security, automated anomaly detection algorithms also contribute significantly to business intelligence. Imagine being able to analyze market trends in real-time and foresee disruptions before they occur. With these algorithms, businesses can allocate resources more efficiently, optimize operations, and drive strategic decisions based on predictive insights. By harnessing these intelligent insights, companies transform raw data into actionable strategies, giving them a competitive edge over rivals who may still be relying on traditional methods.
Implementation Strategies for Success
Successful implementation of automated anomaly detection algorithms involves integrating them seamlessly into the existing architecture. This typically starts with data scientists and IT professionals collaborating closely to customize the algorithms precisely according to the business’s specific requirements.
Challenges to Consider
Despite the advantages, there are challenges to be considered during implementation. Data privacy concerns, integration complexity, and the potential for false positives can pose hurdles that require strategic planning and expert handling.
Automated anomaly detection algorithms are indeed the unsung heroes of modern commerce. These digital watchdogs keep businesses ahead of crisis curves, enabling smarter decisions and fostering a culture of proactive problem-solving. By being attuned to the algorithms’ capabilities and challenges, businesses can harness their full potential, ensuring a secure, sound, and successful data-driven environment.
—
Understanding the layers that make up automated anomaly detection algorithms is a conversation that extends beyond the realm of tech enthusiasts and data scientists. It’s a topic ripe for exploration, backed by a curiosity that piques interest at various industry intersections. These nuggets of knowledge not only highlight the inner workings but also bridge the gap between technology and everyday application.
Automated anomaly detection algorithms sit at the confluence of data science and operational efficacy. They offer not just solutions but also pathways to enhanced understanding and innovation. Considering their complexities, these discussions serve as a vital medium to broaden comprehension, exchange ideas, and propel advancement.
The Challenges in Implementing Automated Anomaly Detection Algorithms
Undeniably, while automated anomaly detection algorithms offer extensive benefits, they are not without their hurdles. Implementation can often resemble untangling a complex knot, filled with technical trials and strategic thinking.
Navigating Technical Complexities
When businesses choose to embrace these algorithms, they are making a commitment that requires significant backend work and upfront investment. From ensuring data quality to training the algorithms adequately, the labor involved can be daunting. One misstep, and all those accurate detections could take a nosedive into false positives, interrupting operations rather than advancing them.
Moreover, establishing a harmonious blend between an organization’s existing IT infrastructure and the new anomaly detection software is a critical checkpoint. It demands that the IT team, data scientists, and stakeholders align their objectives, considering factors like computational resource demands and cool-down periods between active scanning phases.