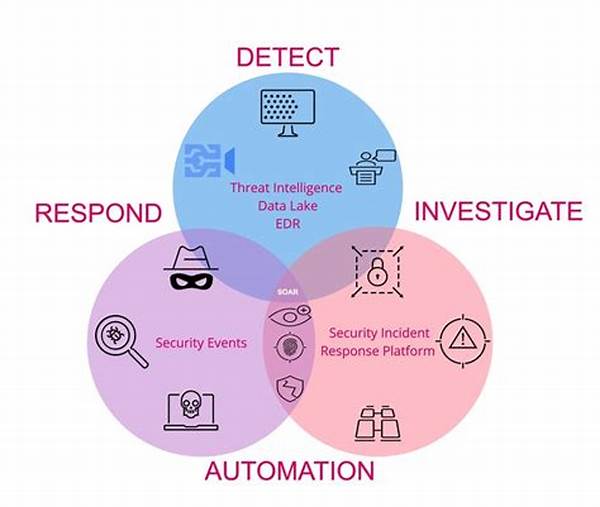
In the bustling digital landscape where billions of data packets traverse the globe at lightning speeds, the necessity for advanced threat intelligence has never been more critical. Imagine the vibrant scenario of data highways bustling with information, some benign, some malicious, constantly under the radar of cyber guardians. Now envision a tool that not only detects but also automatically responds to threats in real time — that’s the essence of real-time threat intelligence automation. Think of it as an elite team of cybersecurity experts who never sleep, are perpetually vigilant, and possess the prowess to act instantaneously. Their sole mission? To protect your digital sanctum with the kind of precision and speed that makes cyber threats quiver.
By harnessing the power of real-time threat intelligence automation, businesses are not only forearmed in their defensive strategies but also gain a competitive edge, showcasing their commitment to safeguarding client data. In a world where data breaches can lead to catastrophic reputational damage and financial losses, having an automated ally that offers protection around the clock is not just an option; it’s a necessity. Real-time threat intelligence automation is the game-changer, transforming how organizations perceive and counteract cyber threats with a proactive rather than a reactive approach.
The Rise of Automated Cyber Defenses
In recent years, the narrative around cyber defenses has shifted dramatically. Organizations are ditching outdated, manual monitoring methods in favor of cutting-edge real-time threat intelligence automation. This shift isn’t just about keeping up with technological advancements but is driven by the sheer velocity and complexity of modern-day cyber threats. With cybercriminals continuously evolving and employing sophisticated hacking techniques, automated systems have become indispensable for maintaining the integrity of a company’s digital infrastructure.
—
Bridging the Cybersecurity Gap
In today’s fast-paced digital economy, the efficiency and efficacy of real-time threat intelligence automation cannot be stressed enough. This advanced technology addresses the perennial issue of bridging the cybersecurity gap by ensuring that companies are not left vulnerable due to slower, manual threat detection and response mechanisms. By automating the process, organizations can focus more on strategic initiatives while their real-time defenses handle the heavy lifting of threat management. Real-time threat intelligence automation fortifies businesses with a kind of digital armor, enhancing resilience and ensuring prompt neutralization of cyber threats.
What Makes Real-Time Threat Intelligence Automation Tick?
The engine powering real-time threat intelligence automation comprises sophisticated algorithms and artificial intelligence capable of distinguishing between benign and malicious activities with surgical precision. This technology not only analyzes huge datasets swiftly but also learns and evolves, adapting to new threats as they emerge. By integrating seamlessly with existing IT infrastructure, real-time threat intelligence automation systems bolster a company’s defenses while optimizing operational workflows, providing a seamless security solution that’s as effortless as it is robust.
Ten Key Elements of Real-Time Threat Intelligence Automation
Efficiency Meets Security
Companies that implement real-time threat intelligence automation quickly realize the mutual benefits of heightened security and improved efficiency. In a world fraught with cyber threats, traditional monitoring systems often lag, leaving organizations vulnerable to fast-acting cybercriminals. By removing the bottleneck of manual processes, automated systems ensure that threats are detected and mitigated in real-time, closing the window of opportunity for potential breaches. This not only bolsters the security posture but also frees up valuable resources, allowing companies to allocate more towards growth and innovation.
With the advancement of AI, machine learning, and big data analytics, real-time threat intelligence automation is continually evolving, offering increasingly sophisticated tools for threat detection and prevention. Each successful thwarting of a cyber threat serves as a testament to the system’s prowess, instilling confidence and peace of mind in stakeholders. As we step further into a digital future, real-time threat intelligence automation stands as a beacon of security and efficiency, poised to lead organizations into a more secure digital era.
Illustration of Real-Time Threat Intelligence Automation
The world of cybersecurity is dynamic and ever-changing, much like a thrilling suspense novel with plot twists at every corner. In this scene, real-time threat intelligence automation plays the protagonist, maneuvering through complexities with confidence and agility. The technology is not only transformative in the fight against cybercrime but also revolutionary in enhancing overall business operations. As organizations continue to navigate the intricacies of digital interactions, adopting such advanced security measures is not just about protection—it’s about staying a step ahead, ensuring security is not a game of chance but a well-calibrated system of defense.
Real-Time Threat Intelligence: A New Era
The incorporation of real-time threat intelligence automation marks a new era in cybersecurity, serving as an indispensable ally for modern enterprises. Its transformative impact on threat detection and management is undeniable, promising not just security but a proactive approach to business continuity. By leveraging advanced algorithms and real-time data, companies can not only survive the onslaught of potential cyber threats but thrive in the confidence of robust security frameworks, poised for the future of digital endeavors.