Hey there, fellow tech enthusiasts! Ever thought about what keeps our digital world safe and sound? Well, let’s talk about something you should definitely know: continuous monitoring for threats. It might sound a bit techy, but stick around because it’s more interesting (and important) than you might think!
Why Continuous Monitoring is a Game-Changer
So, what’s the deal with continuous monitoring for threats? Imagine you’re throwing a party but you need to make sure it stays fun and doesn’t get wild. That’s exactly what this monitoring does for your systems—it’s like a never-sleeping bouncer for your digital fortress. Cyber threats are sneaky and can show up uninvited, but continuous monitoring keeps a watchful eye 24/7. It not only detects bad guys but gets smarter over time. The more it monitors, the better it understands the traffic patterns and detects anomalies. So, in a way, it’s like a detective who learns the habits of its suspects.
Now, in the age of big data and cloud infrastructure, the threat landscape is constantly shifting. This is why companies big and small are relying more on real-time monitoring tools to get ahead of potential issues. Not to mention, it’s a lifesaver for compliance and risk management strategies too. You wouldn’t want your brand’s reputation to get a hit because of a data breach, right? Continuous monitoring for threats helps prevent those nightmare scenarios by catching problems before they escalate.
What’s even cooler? The tech behind it is evolving. Machine learning and AI are getting in on the action, making monitoring smarter and more efficient. This means fewer false alarms and more accuracy. So, as the bad guys get craftier, these systems up their game too. And guess what? That allows IT teams to not just react but be proactive. It’s almost like having a crystal ball, but for cybersecurity!
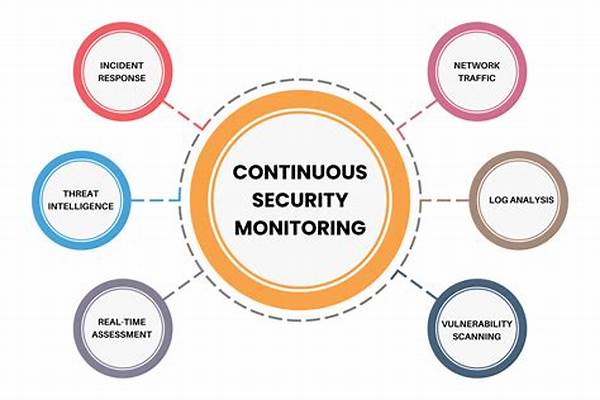
Unpacking Continuous Monitoring for Threats
1. Real-Time Vigilance: Continuous monitoring for threats means your digital security team never sleeps. It constantly checks for suspicious activities in real time, minimizing risks before they become problems.
2. Proactive Defense: It’s not just about detecting threats but anticipating them. Continuous monitoring allows you to patch vulnerabilities before they’re exploited.
3. Adaptable Systems: With continuous monitoring, your security systems adapt based on observed patterns. They learn and evolve, becoming smarter and more intuitive over time.
4. Enhanced Compliance: Whether it’s GDPR, HIPAA, or any other acronyms that govern data protection, continuous monitoring helps ensure you stay compliant by maintaining a constant security overview.
5. Reduced Downtime: Spotting threats early almost guarantees decreased downtime, saving you from potential operational and financial impacts.
The Role of AI in Continuous Monitoring
Step aside, traditional monitoring systems! AI has entered the scene and is making continuous monitoring for threats more fascinating than ever. Gone are the days when monitoring was about simple log tracking. With AI, the system learns from each monitoring wave and gets better at recognizing threats. This means fewer security hiccups and a more seamless experience for users. At its core, continuous monitoring for threats now involves algorithms that sift through endless streams of data, flagging anomalies with stunning accuracy. AI can trace the footprints of a cyber assault from the faintest digital trail, often before the human eye would catch a whiff.
And here’s a kicker: AI-driven monitoring systems don’t just sit around passively. Imagine a security system that not only guards the house but also predicts where the next break-in attempt might occur! AI helps create predictive models to foresee potential weak points, fortifying your systems in advance. In this tech-forward era, it’s like having a crystal ball that’s powered by machine learning! Continuous monitoring for threats with AI on your side is genuinely akin to having a cybersecurity clairvoyant in your corner.
Benefits Beyond Security
Continuous monitoring for threats is not just about safeguarding data; it extends its advantages to operational efficiency and brand reputation, too. Businesses face a myriad of potential disruptions—from network failures to cyber threats—and continuous monitoring plays a vital role in reducing such risks. By maintaining real-time visibility of all operations, businesses can ensure a swift response to any anomalies. This vigilance inherently enhances operational efficiency, as businesses can quickly address and resolve issues before they escalate into significant disruptions.
Additionally, continuous monitoring fortifies brand reputation by preventing notorious data breaches that can lead to customer mistrust. No business wants to make headlines for the wrong reasons, especially when it involves customer data. With continuous monitoring, companies reassure their customers about their dedication to robust security measures. At the end of the day, trust is one of the most crucial assets a brand can own. By consistently demonstrating a commitment to security, brands build enduring trust with their customers, a key driver in today’s competitive marketplace. In essence, continuous monitoring for threats is about securing a business’s future in multiple dimensions.
Elevating Your Security Game
What if I told you that continuous monitoring for threats could transform your entire security posture? You see, it’s akin to upgrading from a standard lock to an impenetrable fortress. While traditional defenses like firewalls and antivirus software provide the first line of defense, continuous monitoring ensures you’re always one step ahead of potential threats. It’s like pairing a high-tech home security system with a team of expert guards who work around the clock to keep intruders at bay. Continuous monitoring doesn’t just react but provides a strategic approach to cybersecurity.
Moreover, as our digital ecosystems expand, touching more aspects of our daily lives, the need for robust monitoring becomes even more pressing. Think of it this way—while we get smarter devices and more interconnected platforms, cyber threats evolve too. It’s a digital arms race out there, and continuous monitoring equips you with the arsenal needed to stay ahead. With the right strategy, businesses can turn potential vulnerabilities into fortified points of strength, ultimately keeping their assets and information untouchable. Remember, in today’s digital age, being proactive isn’t just a choice; it’s a necessity.
How to Implement Continuous Monitoring
Here’s where it gets practical. Implementing continuous monitoring for threats isn’t just about installing fancy software. It takes a structured approach and an unwavering commitment to evolving with the times. First, you need to identify key assets that require monitoring—think databases, customer information, and critical applications. From there, assessing the existing security posture helps determine what tools will be most effective. It’s like tailoring a custom suit—one size definitely doesn’t fit all.
After setting up the necessary tools, the focus shifts to integration. Seamlessly integrating these monitoring systems into your existing infrastructure ensures they’re effective and adaptive. And let’s not forget the human factor; training your team to interpret monitoring data and respond appropriately is crucial. Think of it as empowering them to not only identify issues but anticipate and mitigate them. Continuous feedback and recalibration of the system ensure that it’s always aligned with the latest cybersecurity threats.
Wrapping It Up
In summary, continuous monitoring for threats shouldn’t feel like an impenetrable tech challenge. Instead, think of it as a proactive measure that ensures your digital domains are safe, secure, and running smoothly. In this wild world of cyber threats that change faster than memes go viral, it’s the stronghold you need. By employing tools that watch over systems 24/7, leveraging the power of AI, and training teams to act swiftly, you’re essentially building a bulletproof vest for your digital assets. And honestly, who wouldn’t want that peace of mind?
So go on, step into the world of continuous monitoring for threats, and give your digital security the upgrade it deserves. Consider it an investment in not only the safeguarding of data but also the protection of your organization’s reputation and future growth. Happy monitoring!