Imagine stepping into a world where your digital security is as impenetrable as a fort. This is the promise of multi-factor authentication technology, a marvel in cybersecurity that aims to protect you from looming threats lurking in the digital shadows. But what exactly is this technology, and why should it matter to you? In a world where cyber threats are as common as cities and towns, multi-factor authentication (MFA) rises as the shield we all need. From protecting personal information against identity theft to securing corporate data from corporate espionage, the significance of this technology stretches across domains and user types.
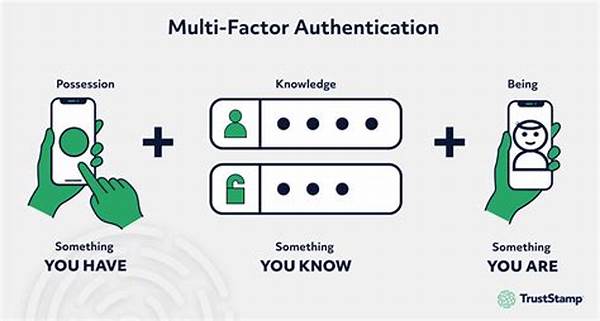
Multi-factor authentication technology is not just a fancy term thrown around in IT departments; it’s a dynamic approach that involves using more than one form of verification to grant access to applications or environments. Think of it as a bouncer at an exclusive club, but instead of checking IDs, MFA requires additional proof of identity before letting you in. These proofs could be something you know (like a password), something you have (like a smartphone), or something you are (like your fingerprint). It makes online accounts less vulnerable to unauthorized access, adding layers of protection that are difficult for potential intruders to penetrate. If you’ve ever worried about your email or bank accounts being hacked, this could be your silver bullet.
The Impact of Multi-Factor Authentication Technology
The implementation of multi-factor authentication technology has become synonymous with enhanced security protocols for organizations globally. Reports indicate that companies employing MFA experience 90% fewer breaches. Yet, beyond corporations, the everyday internet user benefits immensely from this technology too. Consider the case of Jane, an amateur photographer who stored her lifetime’s worth of photos on a cloud platform. One unfortunate day, she received a notification about a suspicious login attempt from an unrecognized device. Fortunately, thanks to the multi-factor authentication technology she had activated, the attacker couldn’t proceed beyond the second security check. Jane’s valuable photo collection remained untouched, sparking her undying trust in MFA.
The Mechanics Behind Multi-Factor Authentication
Multi-factor authentication technology functions mainly by requiring users to pass through multiple checks. The best part? Each check represents a different security dimension. Firstly, there’s what you know—like your trusted password, unique yet memorable. Secondly, there’s what you have—perhaps a smartphone with an authentication app that generates a time-sensitive code. Lastly, there’s what you are—fingerprint or facial recognition adding that final, unassailable fortress. This combination ensures that even if one factor is compromised, the other layers remain robust barriers against unauthorized access.
Real-Life Applications and Usage
The motivation for robust security, facilitated by multi-factor authentication technology, transcends individual use. Authorities worldwide have emphasized the need for improved authentication processes to counteract cyber threats and hacking attempts. It’s clear that the prevalence and development of cybersecurity tools are not just choices but necessities in our digitized world.
The New Norm: Multi-Factor Authentication Trends
Evolution and Future Prospects
The demand and reliance on multi-factor authentication technology have surged phenomenally, particularly with remote work becoming mainstream. Companies now scramble to secure not only their physical workspaces but also their digital platforms. The Identity Theft Resource Center revealed a 17% rise in data breaches in recent months, underscoring the urgent need for companies to evolve their cybersecurity strategies. With its ability to offer superior protection, MFA continues to gain ground, evolving swiftly to incorporate more intuitive and user-friendly options, including biometric and behavioral analysis tools.
Challenges of Adoption
Even with its benefits, implementing multi-factor authentication in organizations isn’t devoid of challenges. Cost implications, user resistance, and the requisite technology infrastructure are notable hurdles. Yet, the scales tip favorably considering how a single data breach could cost an organization potentially millions in damages.
The anecdote of how one company successfully thwarted a breach attempt by leveraging multi-factor authentication technology speaks volumes. Spare a thought for Acme Corp, a thriving tech start-up. As it grew, so did its appeal to hackers seeking sensitive data. Forward-thinking, Acme’s team rolled out an MFA system. When a breach attempt featuring stolen credentials occurred, the MFA system flagged it. The attempted breach was thwarted, saving the company from potential catastrophe.
In conclusion, the versatility of multi-factor authentication technology is unequivocal, safeguarding business interests and personal information alike. Embrace it and step confidently into the future of secure technological ventures.