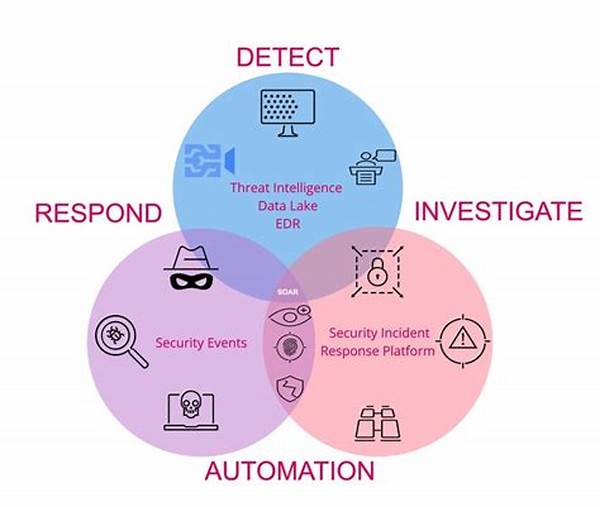
Threat Intelligence Automation Tools: Revolutionizing Cybersecurity
In today’s fast-paced digital landscape, the need for robust cybersecurity measures has never been more pressing. The cyber threats we face are not only increasing in volume but also in complexity. Enter threat intelligence automation tools—a revolutionary solution designed to uplift and revolutionize the way organizations approach cybersecurity. These tools automate the collection, analysis, and dissemination of threat intelligence data, enabling businesses to stay a step ahead of cyber adversaries.
Threat intelligence automation tools are regarded as a game-changer in the cybersecurity world. By automating repetitive tasks, they allow security teams to focus their efforts on strategic decision-making and proactive threat mitigation. Imagine a future where your cybersecurity defenses are not just reactive, but predictive—identifying threats before they manifest into real attacks. This is not just a pipe dream, but a tangible reality with threat intelligence automation tools.
Let us embark on a journey to understand how these cutting-edge tools can transform your business. Through this exploration, we will unravel the benefits, risks, and implementation strategies to ensure you harness the full capabilities of threat intelligence automation tools. The future of cybersecurity is not something to be feared; it’s an opportunity to be embraced with insight and innovation.
From SMEs to large corporations, the appeal of threat intelligence automation tools spans across industries. These tools are equipped to enhance the security posture of any organization, unlocking a world brimming with cyber vigilance and resilience. Embark on this cybersecurity voyage and discover why these automation tools are not just a luxury but an operational necessity.
Unpacking the Benefits of Threat Intelligence Automation Tools
Moving into the core advantages, threat intelligence automation tools significantly improve the efficiency and effectiveness of cybersecurity operations. By automating tedious and time-consuming tasks, these tools free up valuable time for human analysts to focus on more complex, strategic areas.
Understanding the Role of Threat Intelligence Automation Tools
Threat intelligence automation tools have become a cornerstone in the modern cybersecurity arsenal. With cyber threats lurking at every corner, having these automated systems in place ensures swift and informed responses to potential breaches. Automation tools streamline processes, making organizations more agile and better equipped to handle the ever-evolving threat landscape.
Diving into the technical aspects, these tools gather a plethora of data from multiple sources, both internal and external. This data is then harmonized and analyzed, providing organizations with actionable insights. By integrating machine learning algorithms, threat intelligence automation tools not only analyze past data but predict future risks, enabling proactive threat management.
The beauty of these tools lies not just in their efficiency but also in the scalability they offer. Whether your organization is a multinational enterprise or a growing startup, threat intelligence automation tools can be customized to your specific needs. Their adaptability ensures that as your organization grows, your cybersecurity measures grow correspondingly, providing uninterrupted protection.
Furthermore, these tools empower organizations to make informed decisions swiftly. With real-time alerts and intuitive dashboards, business leaders can assess the situation promptly and implement the necessary countermeasures. The blend of technology and human expertise in utilizing threat intelligence automation tools ensures a robust, flexible, and comprehensive security framework.
Key Features and Capabilities
The Versatility of Threat Intelligence Automation Tools
Extending the analysis to specific features, threat intelligence automation tools boast several functionalities that give organizations a competitive edge. First and foremost, the real-time data processing capabilities ensure that any emerging threats are identified and addressed promptly.
Key Components of Threat Intelligence Automation Tools
The Power of Threat Intelligence Automation
The implementation of threat intelligence automation tools offers a transformative approach to managing cybersecurity. With these tools in place, organizations not only boost their security infrastructure but also instill a culture of proactive risk assessment and quick response. The shift from manual processes to automated intelligence brings about an era where data-driven decisions lead the charge against emerging threats.
In this vibrant age of digital advancements, it is crucial to stay ahead of the threat curve. By integrating threat intelligence automation tools, organizations ensure they are not only reacting to threats but anticipating them. The power of automation lies in its ability to revolutionize traditional workflows, offering a seamless blend of technology and human oversight.
Why Organizations Choose Threat Intelligence Automation Tools
Leading the Charge in Cybersecurity
Ultimately, the choice to integrate threat intelligence automation tools represents a commitment to leading the charge in the fight against cybercrime. Organizations investing in these tools witness a marked improvement in their security measures—a testament to the robust, innovative capabilities these tools offer. The seamless synergy between artificial intelligence and human expertise creates a formidable line of defense in the modern digital battlefield.
In conclusion, understanding and embracing threat intelligence automation tools is not just about enhancing cybersecurity. It’s about adopting a forward-thinking mindset that welcomes the dynamic shifts in technology and redefines how security operations are conducted. As organizations continue to evolve in this digital age, those that arm themselves with the right tools will emerge resilient, secure, and ahead of the curve.
Illustrations of Threat Intelligence Automation Tools in Action
Illustrating the Power Behind Automation
Threat intelligence automation tools not only serve as the backbone of modern cybersecurity strategies, but they also represent a beacon of innovation, driving organizations to adopt best practices in threat management. The era of guesswork is long gone; in its place stands a systematic approach powered by data, analytics, and automation. These tools illustrate the sheer potential unlocked when machines and humans collaborate towards a common goal: safeguarding digital integrity.
Today’s cybersecurity challenges demand robust, agile, and intelligent solutions. Embracing threat intelligence automation tools is more than adapting to current needs; it’s preparing for what’s to come. By leveraging these automated technologies, organizations ensure that they are not only reacting to cyber threats but actively shaping the future of cybersecurity.