H1: Real-Time Threat Intelligence Solutions
In an era where cyber threats lurk around every digital corner, the phrase “real-time threat intelligence solutions” becomes not just technical jargon, but a vital necessity. This evolving landscape, akin to a digital gladiator arena, teems with both opportunistic hackers and savvy cybersecurity warriors. The pressing question is, how do businesses, large and small, equip themselves to not just fend off these threats but to do so with speed and precision? Enter real-time threat intelligence solutions—an arsenal designed to empower, protect, and give you that ever-important edge. Imagine having the power of foresight, akin to knowing the weather before you pack for a trip, potentially saving you from disastrous outcomes. This is the essence of real-time threat intelligence, ensuring you’re not just aware but prepared.
In our everyday hustle, when we’re buried under emails, reports, and meetings, it’s easy to overlook the invisible threats. Threats that could, at any moment, escalate from a mere annoyance to a full-blown catastrophe. For many, the first inkling of a cyber attack comes too late, often when the damage is already done. What if you could switch roles and see the attack coming, intercept it in its tracks, and send your digital adversaries packing even before they reach your digital doorstep? Real-time threat intelligence solutions make this possible, providing a proactive approach to cybersecurity.
These solutions don’t just watch from the sidelines; they dive into the digital fray, pulling from vast data pools, and seamlessly weaving together crucial intel that allows for rapid action and mitigation. Think of it as having a digital Sherlock Holmes on your team, constantly analyzing patterns, predicting potential threats, and guiding your defenses to address vulnerabilities before they become breaches. The peace of mind this offers is not just a benefit—it’s a necessity in today’s digital landscape.
H2: Unmasking the Power of Real-Time Threat Intelligence
In implementing real-time threat intelligence solutions, an organization unlocks the door to a realm of detailed insights and enhanced cybersecurity strategies. The key here is real-time—this isn’t about discovering issues after the fact but being abreast of evolving threats. With such solutions, companies step up from being reactive to becoming proactive, ideally staying steps, if not leaps, ahead of potential cybercriminal activities. These systems take in data, not just from within an organization, but across the globe, benefiting from shared intelligence that paints a fuller, richer, and more accurate portrait of the threat landscape.
Now, picture a bustling security operations center powered by this technology. The atmosphere is intense yet controlled, thanks to the ever-vigilant stream of up-to-date threat data. Forewarned is forearmed, they say, and nowhere is this more applicable than in today’s dynamic digital arenas. Businesses leveraging real-time threat intelligence solutions cultivate not just security and resilience but also trust and assurance among stakeholders and clients. When organizations have such a robust defense, they’re not just safeguarding data but protecting their reputation and fostering confidence.
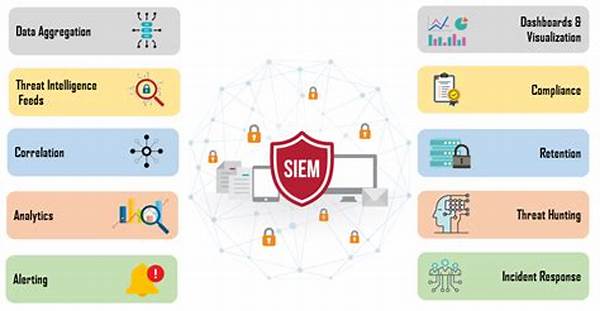
—H2: Understanding the Structure of Real-Time Threat Intelligence Solutions
Effectively understanding the anatomy of real-time threat intelligence solutions can seem like untangling an elaborate web unless broken down systematically. These solutions are built on multiple layers of technology, people, and processes that interlock to create a fortified cybersecurity posture. Let’s dissect this complex architecture to grasp not just how it functions but why it’s a game-changer in cybersecurity.
At the core, these solutions are powered by expansive threat intelligence data sets collected from a myriad of sources across the globe. This data feeds into sophisticated algorithms designed to detect anomalies, patterns, and emerging threats. The computational backbone of real-time threat intelligence solutions leverages artificial intelligence and machine learning to analyze these vast datasets at unprecedented speeds, ensuring no threat goes unnoticed.
H3: The Role of Human Expertise in Threat Intelligence
Human expertise plays a critical role in complementing machine-driven analysis within real-time threat intelligence solutions. Security analysts leverage AI-driven insights, adding a layer of intuition and experience that machines cannot mimic. These experts validate alerts, perform detailed investigations, and develop response strategies tailored to the specific threat landscape they manage. This collaboration between man and machine empowers organizations with actionable intelligence, not just data points.
Beyond algorithms and AI, the backbone of these solutions is their adaptability. As cyber threats evolve, real-time threat intelligence solutions must adapt to meet new challenges. This adaptive quality is what sets them apart, providing comprehensive, current, and contextual insights that drive cybersecurity strategies effectively. Therefore, organizations must build a culture that values continuous learning and adaptability, ensuring that their defenses grow stronger with each new intelligence set they assimilate.
—H2: Actions Enabled by Real-Time Threat Intelligence Solutions
H2: Embracing Real-Time Dynamics in Threat Management
Incorporating real-time threat intelligence into cybersecurity operations transforms how organizations perceive and handle threats. It’s akin to upgrading from black-and-white TV to full-color HD—not just in vividness but in clarity and depth. The strategic advantage doesn’t just lie in tech alone but in how teams utilize it. By enabling organizations to act swiftly and decisively, these solutions reduce potential damage, protect valuable assets, and secure reputational integrity.
H3: Real-World Impacts of Real-Time Threat Intelligence
The advantages of using real-time threat intelligence solutions extend far beyond what meets the eye. Companies adopting these can attest to the reduction in successful cyber incidents, shortened incident response times, and increased understanding of an ever-changing threat landscape. By integrating these systems, organizations report heightened efficiency in wireless and network security, proving that investment in such technology pays dividends in maintaining operational integrity.
—
With real-time threat intelligence solutions, organizations don’t just play the defense. They command the field, steering the course of battle towards fortified verges, safeguarding not just systems and data, but also reputation and trust. Embrace the future of cybersecurity and stand triumphant against digital shadow threats lurking in the vast expanse of cyberspace.
H2: Explaining the Benefits of Real-Time Threat Intelligence
Real-time threat intelligence solutions are not a luxury but a necessity in today’s frenetic digital world. They serve as the vigilant sentinels of your digital frontier, working endlessly to preempt the damaging possibilities that cyber threats present. With the integration of these systems, organizations ensure that their defense mechanisms are not only robust but agile. This adaptability is key to navigating the unpredictability of cyberspace, allowing firms not just to survive, but to thrive.
Through testimonials from industry leaders, we hear echoes of satisfaction and assurance, a testament to the transformative force of these solutions. They stand as not only a product or service but an ongoing partnership in the fight against cybercrime. As cyber landscapes continue to shift and morph, staying at the cutting edge of threat intelligence ensures that organizations are not merely reactive but poised to seize the initiative and maintain the upper hand in cybersecurity strategy.
H2: Advancements in Cybersecurity
Organizations that employ real-time threat intelligence solutions often acknowledge marked reductions in cyber incidents and celebrate their newfound capacity for predictive threat management. By staying informed and agile, companies can not only keep pace with but outstrip potential adversaries, crafting a security environment that is smarter, faster, and more resilient.
H3: Integrating Threat Intelligence into Business Strategy
Beyond mere protection, real-time threat intelligence solutions become a crucial component of business strategy. By recognizing threats before they escalate, companies conserve resources and focus on innovation and growth, allowing the security enabled by these technologies to foster rather than hinder business progress.
Such advanced strategies are crafted upon the valid insights that real-time threat intelligence offers, allowing businesses to strengthen their defenses proactively. This results in not only technological robustness but also in fostering trust with clients and stakeholders, ensuring a safeguarded business environment ripe for sustaining success and turning cybersecurity from a challenge into a strategic ally.